Criminal Minds: How to think like a hacker?
With increasing website breaches through web application exploitation, it becomes important to rethink the entire security outlook. Why is it that major players in the global business are losing battles to hacking even with huge security infrastructure and budgets?
Security analysts believe that the problem lay dormant and overlooked in the very concept of tradition information security. Organizations have believed that fortifying network and transport layer is the best practice, a myth that took billions away from companies worldwide.
What did the hackers involve in Sony and Alibaba data breaches had? Were they superior at intelligence somehow? Did they have access to some unheard technology? Not exactly.
It has been researched that a majority of data breaches against businesses were not through zero-day threats. In other words, hackers did not have special techniques that couldn’t have been countered. It was always a matter of finding weaknesses and exploiting them to advantage, at the right time.
The solution is simple. How would you prevent a hacker? You need to think like him. You have to test the security system just the way a real hacker would exploit them. Here is a web application hacker guide that will help you understand their strategies better and you can learn from them on how to protect your web assets.
Finding Dark Motivation
Why would someone hack your web applications? According to results from the “Cybercrime Survey Report 2014”, 58% of the attacks happen for financial gains. Malicious damage, competitor grudge, and ethical reasons are some of the other popular motivators to cybercrimes.
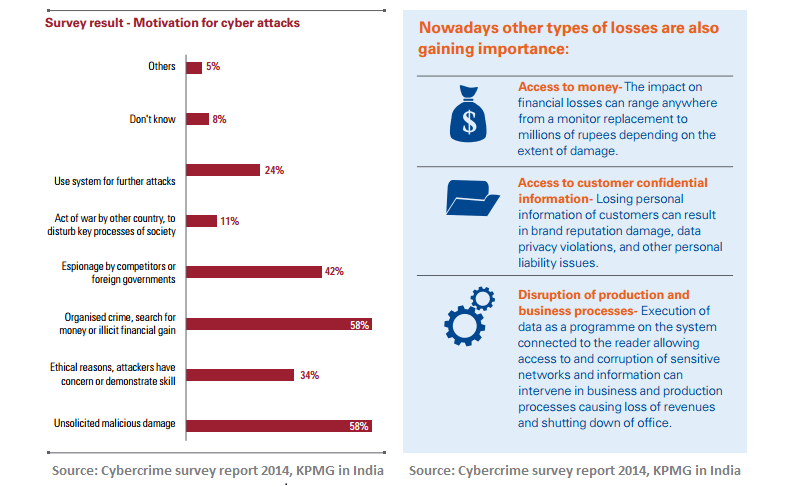
While online business websites are at the highest risk of hacking, the public sector isn’t safer either. Last year alone 155.GOV and.NIC domains were hacked. A majority of these attacks came from neighboring country IPs.
Countermeasure:
Begin with gauging risk level and allot appropriate budget to web application security accordingly. Risks levels are critical for an organization with considerable online reputations and business credibility. Government and banking websites are also lucrative options for hackers around the world.
Detecting Weaknesses
Detecting weaknesses or vulnerabilities in web application architecture is the first step for any hacker. It helps him analyze if a certain website is exploitable. A few years ago, the vulnerability-finding process had to be performed manually, but now there are dozens of open source scanners that look for basic vulnerabilities like
• Cross-Site Scripting (XSS)
• Command execution detection
• CRLF Injection
• SEL Injection and XPath Injection
• Weak .htaccess configuration
In fact, some of the hackers also like to custom-code these web application scanners to test hundreds of websites in a day and feed data on most vulnerable ones, which obviously makes things a lot easier for hackers.
Countermeasure:
Web applications are the future of online survival today. They change and evolve every day according to business’s needs and vulnerabilities are bound to exist in one form or the other. The only smarter way to stay one step ahead of the hackers is to detect vulnerabilities with an even smarter web application scanner. IndusGuard Web not only looks for OWASP and WASC listed vulnerabilities but also monitors for malware, blacklisting, and defacement attempts.
Analyzing Logical Weaknesses
While automated programs can find basic vulnerabilities, it requires an analytical human mind to look for logical weaknesses. These are vulnerabilities within the business logic of an application and are limited by a definition or scope.
Think of a business logic flaw as a door in your house that can be accessed from the terrace. Logic says that your house is secure and difficult to the barge, but your recent outdoor renovation project labor left a ladder in the garden unintentionally. Now you don’t really know about this potential threat, but a thief can exploit it. Even your basic security schedule of checking locks and alarm systems will fail to detect this threat.
Business logic flaws are similar to this scenario. They can have multiple origins and multiple results especially, across dynamic websites and applications. Modern apps are continuously changing with new vectors coming in and you can never really predict that a hacker might find handy.
Unfortunately, most companies do not even know about them unless there is monetary leakage. Following are some of the logic flaws that cause troubles.
• Money-Related Application Logics- These logics command online monetary transactions, deals, discounts, refunds, shipping fee and so on.
• Time-Related Application Logics- These logics define how web applications handle sessions and timeouts for users.
• Process-Related Application Logics- It is also possible to exploit internal-facing applications for human resources management, procurement, warehousing, and other processes.
Countermeasure:
Business logic flaws can only be detected and mended by people who understand how such exploitations work. Manual penetration testing from application security experts is the best way to find such vulnerabilities before hackers.
Exploiting Weaknesses
Finding vulnerabilities is enough neither for the hackers nor for businesses. This is exclusive information that can be used to bring down the system or make it stronger. Hackers typically like to keep the vulnerability finding with them before exploiting at the right time or sell them to someone who plans to achieve the same.
Usually, a single vulnerability like SQL injection is used to breach into the database and pull out required information like customer list or credit card information. However, there have been hacking cases where crooks use multiple vulnerabilities at once to steal sensitive information and then deface or delete pages.
It has been estimated that businesses lose annually $3.8 million Annually to Cyber Exploitations. You can read about it here. In fact, in the past few months only, large online song portal and taxi-for-hire websites have been hacked using vulnerabilities like SQL Injection. Following is the list of most commonly exploited vulnerabilities other than SQL Injection.
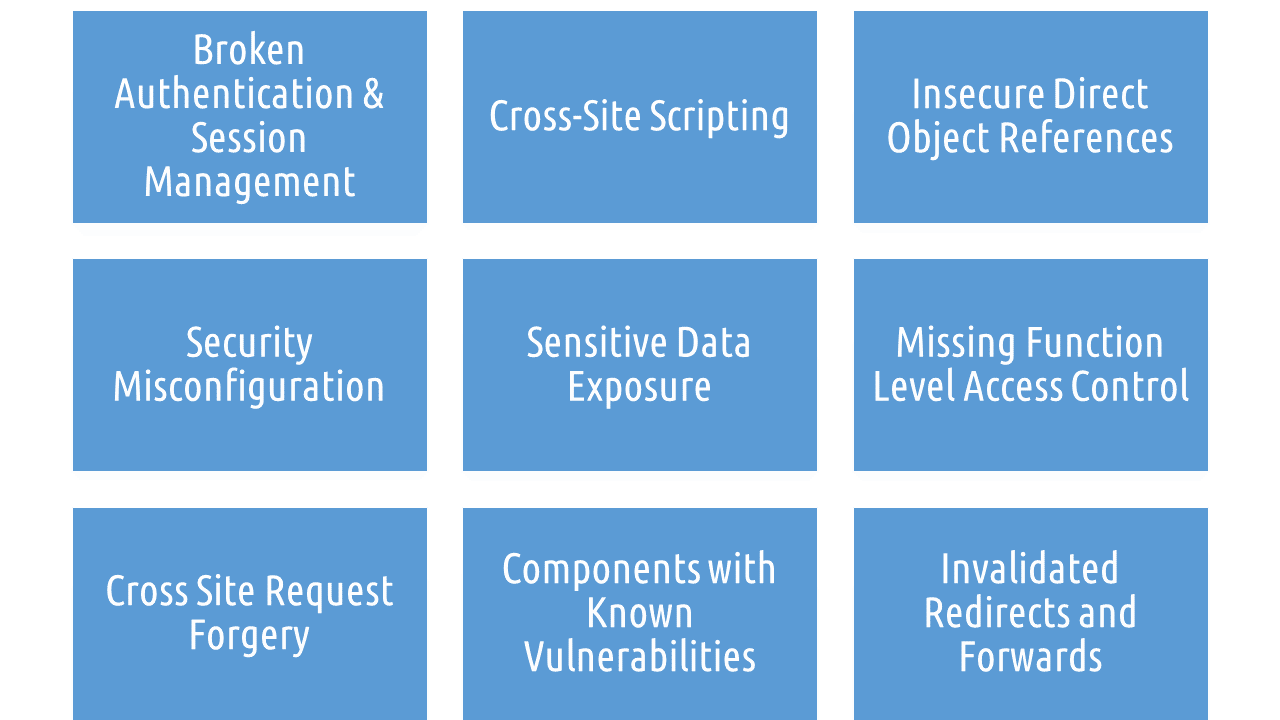
Countermeasure:
After vulnerability detection, patching application source code is not always possible for many reasons. For continuous protection, a web application firewall is a feasible solution that not only prevents attacks but also provides data on attack attempts. It helps to learn more about techniques that attackers use and then frame better policies to detect and protect web applications.
All-out Service Denial
Distributed denial-of-service (DDoS) is exploitation that all web applications are vulnerable to. It is an absolute weapon that all crooks enjoy using against helpless websites. Hired bot services are used to send thousands of requests to the server in a bid to choke it completely. Under a successful DDoS attack, users are unable to access the website, as the server is busy processing requests from bots before it crashes completely. In fact, there have been reports of distributed denial-of-service attacks that had lasted for weeks.

Hackers often ask for ransom in lieu of stopping such attacks. In other scenarios, they just want to disrupt performance out of grudge or rivalry. In every situation, DDoS habits cost millions for companies. Read more about it at “Learn Why and How App DDoS is #1 Security Risk Today”
Countermeasure:
Distributed denial-of-service attacks can only be stopped with constant monitoring. Managed security experts have to look for attack patterns based on malicious IPs, machine fingerprints, and bot signature and create custom rules to block them and prevent DDoS attacks before it can cause any harm.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 October 6, 2015
October 6, 2015



