5 Top Cloud Security Threats and Tips to Mitigate Them
Cloud computing has accompanied a new borderless work world, which boosts the free flow of information and open collaborations. This has allowed companies to be more productive and has made remote work possible, especially in this Covid pandemic, allowing enterprises to ensure business continuity. While the cloud environment provides enormous benefits to organizations, it has also opened a host of vulnerabilities for attackers to exploit.
In the 2020 cloud security report, there are mixed reviews of whether cloud adoption will improve enterprises’ security.
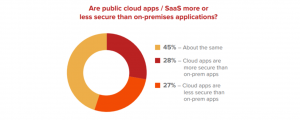
Image Source: bitglass
45% of those surveyed said that both the security of cloud applications and on-premises applications are the same. 28% of respondents said that cloud apps are more secure than on-premises apps while 27% were concerned that cloud apps are less secure than on-premises apps.
The same survey highlighted that 93% of respondents were extremely concentrated on public cloud security. These data show that enterprises recognize that cloud adoption is inherently safe but are battling with their responsibility to use it securely.
Companies, which leverage cloud technologies without being aware of the cloud security risks open themselves up for myriad financial and technical risks. Let’s break down the top security risks that come with adopting cloud technologies and tips to mitigate them.
1. Unauthorized Access to Data
It is the biggest risk to cloud security. According to a new cloud security spotlight report, 53% of respondents see unauthorized access via improper access controls and misuse of employee credentials as their biggest cloud security threat.
Unauthorized access involves individuals accessing enterprise data, networks, endpoints, devices, or applications, without having proper permissions. The good news is that poor access control can be tackled through security solutions in combinations with access management policies. Indusface’s Web Application Firewall allows blocking of access to cloud applications based on IP, countries, GEO location, and many more. It provides complete tracking, monitoring as well as reporting of app access, enabling enterprises to comply with data security regulations.
Tips to prevent Poor Access Management
- Develop a data governance framework for all user accounts. All user accounts should be connected directly to the central directory services like Active Directory that can monitor and revoke access privileges.
- You can use third-party security tools to regularly pull lists of users, privileges, groups, and roles from cloud service environments. Then your security team can sort and analyze it.
- You should also keep logging and event monitoring mechanisms in place to detect unauthorized changes and unusual activity.
2. Distributed Denial of Service (DDoS) Attacks
Another most common form of attack on the cloud, which proves extremely damaging. DDoS (Distributed Denial of Attack) is a kind of attack, which involves denying access to online service for legitimate users by flooding them with malicious connection requests.
Tips to tackle DDoS attacks in the cloud
- Have an excess of bandwidth on your enterprise’s internet connection. The more bandwidth you have, the more hackers must do to flood its connection.
- Discover vulnerabilities in your system – scan your network and system to determine vulnerabilities with web application scanning tools to find vulnerabilities, which can be exploited to execute DDoS attacks. Implement security controls to fix the detected security issues.
- Keep a backup internet connection – a backup connection with a separate pool of IP addresses provides an alternate path in case the primary circuit is flooded with requests.
- Configure WAF rules to filter out the malicious IPs – Configure your WAF firewall with custom rules to monitor and filter out traffic based on your requirements.
3. Cloud Misconfiguration
Three-quarters of all enterprises on the cloud are suffering from some sort of cloud misconfiguration, which affects security. Common weaknesses include default passwords, inadequate access restrictions, mismanaged permission controls, inactive data encryption, and many more. Many of these vulnerabilities result from insider threats and a lack of security awareness.
Another way company introduces vulnerabilities is by attempting to personalize their cloud usage by setting changes or plug-ins. These ad-hoc changes can cause configuration drift, which creates availability, management, and security problems.
Tips to Overcome Cloud Misconfiguration Error
- Get to know your Cloud – Learn all the services, settings, and permissions of your cloud services, and never forgot to leverage the benefits of integrated security features.
- Modify credentials and permissions – thoroughly check the default credentials and set up multi-factor authentication to ensure an extra layer of security.
- Regularly audit your cloud asset – Don’t assume that properly configured cloud settings will remain the same for a long time. Proper auditing and monitoring can help you to identify the sign of misconfigurations.
- Choose the right security solutions – The best cloud security service providers like Indusface can provide a complete package of features, which includes security management, threat detection, and intrusion prevention.
4. Data Leaks and Data Breaches
The largest and critical cloud computing threat for organizations today is the loss of personal and sensitive information and data – both inadvertently and deliberately. The risk of data breaches increases as more companies allow their employees to use personal devices for work without implementing a robust security policy in place. Using personal devices to access storage services like One Drive or Dropbox increases security risks, especially when older OS versions are used. Another way in which sensitive information can be leaked is due to insider threats. Storing sensitive data and passwords in a plain text file can mean it is susceptible if the attackers get their hands on it.
Especially this is high risks in the cloud since it is a shared environment, a single vulnerability on the cloud opens the whole environment to be compromised leading to data breaches and loss.
Tips to avoid the risk of Data Leaks
- Encrypt Data – Sensitive data should not be in your cloud environment without being encrypted.
- Change Password – Store all your passwords in a safer place. Be smarter while you choose a password and increase the frequency in which they’ve changed.
- Set Permissions – Not all employees need the same level of access to your sensitive files. Assign permissions based on a ‘need to know’ basis to prevent the wrong people from accessing.
- Educate your staff – Train your staff to prevent them from inadvertently leaking sensitive information.
5. Insecure API
The adoption of APIs is advantageous for businesses, but it is a nightmare for the security team.
Though APIs are meant to streamline cloud computing processes, they are not always black & white. There is a gray area where APIs if left unsecured can allow hackers to exploit private details. Insufficient API security is one of the major causes of cloud data breaches. Gartner predicts that by 2022, APIs will be the most common vector used frequently in cyber-attacks.
Best Practices for API security
- Comprehensive authentication & authorization policies – APIs should be designed with tokens, signatures, quotas, encryption, API gateways, etc., to ensure API security.
- Web Application Firewalls – applies web-based vulnerability exploit defense to APIs in the cloud
- Choose standard API framework – relay only on APIs which are designed with security in mind. Examine its security aspects and decide whether it is secure enough to integrate 3rd party apps.
Wrapping up
The shift to a cloud environment provides companies much need scalability and flexibility to remain competitive in the unstable business environment. At the same time, remember, cloud migration exposes your firm to security vulnerabilities if you don’t leverage security best practices. Don’t let this happen to you. Be proactive to prevent them in the first attempt!
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 May 6, 2021
May 6, 2021




