Habits to Secure Your Website From Hackers
There are three types of website owners in the world: those with exploitation risk awareness, those who believe that nothing can compromise their website, and those who don’t really care about it.
The second type of owners regret and suffer more often than others. Truth is that we live in a world where more than 20 websites are hacked every single minute, which means that sooner or later attackers will try to get into presumed ‘secure’ systems too and chances are that they’ll succeed.
For those who don’t care, a usual rebuttal is that their business or organization is hardly worth the effort, but real reasons for hacking are actually much more than just monetary gains. Today, attackers hack for defacement, data breach, server takeover for email relay spam, temporary web server utilization, illegal file transfer and for a lot of other malicious activities without knowledge.
These attempts are usually run on an automated script backed by automated tools that look for poorly scripted or secured websites and servers. Hence, every website owner should have a basic checklist to make sure that the cybersecurity is intact, or at least updated.
7 Habits to Secure Website Owners
Habit 1: Auditing Consistently
Administrators and information security officers rarely look beyond their own perception of an attack and exploitation. And that is exactly where a security audit can help assess how strong the security foundation really is.
Ideally, you should be looking at regular audits for almost everything including external resources, mobile applications, web applications, physical security, routers, firewall, hubs, server equipment, virtual infrastructure, VPNs, wireless security, and workstations. However, again due to the fact that 75% of the breaches happen at the application layer, it’s preferable to have a stronger web application security audit program through web application scanning (WAS), dynamic application security testing (DAST), virtual patching, and monitoring.
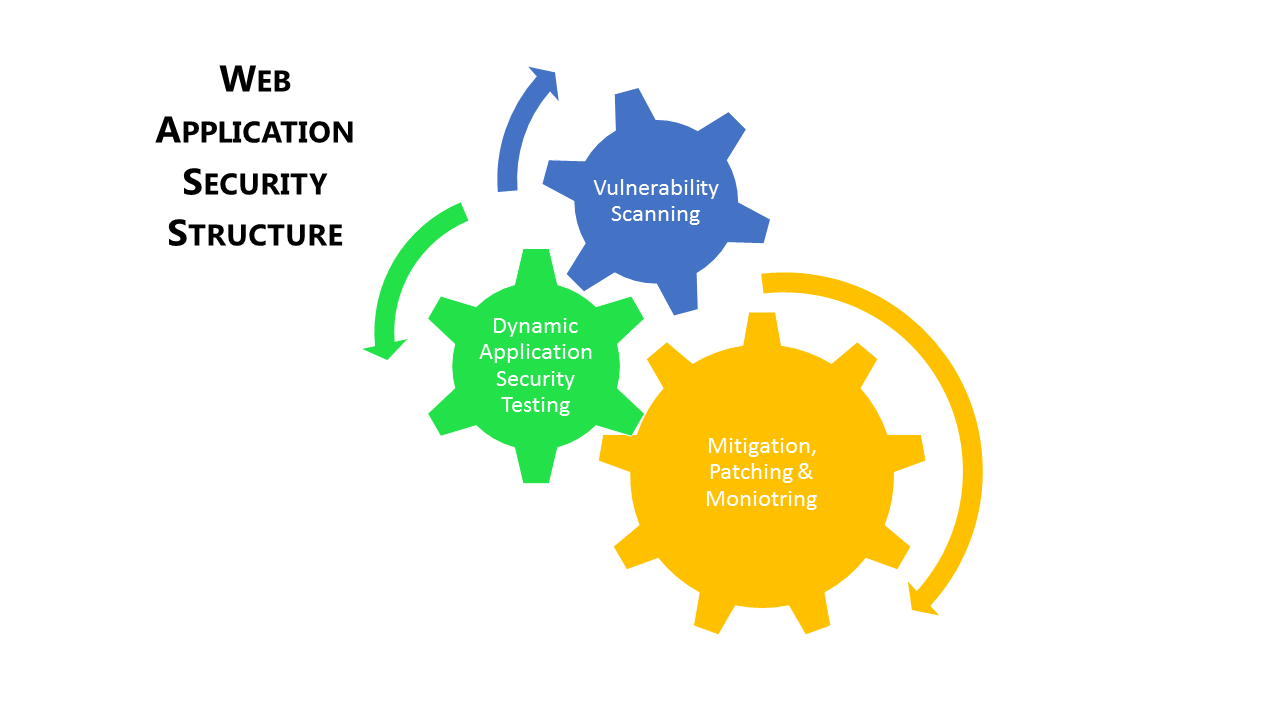
Web Application Security Structure
Habit 2: Reviewing Information Availability
Often attackers utilize available information about the website against the system. It can be anything from public DNS records to employee info that can be socially or reversely engineered to exploit your resources.
Here also, application-layer protection is critical. Information on the application type, server type, developer, operating system, deployment, or bandwidth can be used to launch DDoS, command injection, or Cross-Site Request Forgery.
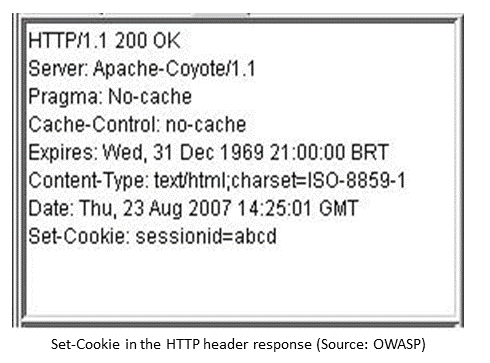
A secure website owner should ideally review and limit publicly available information and analyze how it could be exploited in one way or the other. The absolute concern should be taken before rolling out the directory structure or local machine name information even on the error pages.
Habit 3: Monitoring Continuously
Monitoring attacks, traffic, and user behavior, especially with a dedicated tool or scanner provides valuable information. Website administrators can learn a lot about what countries, IPs, and connections are causing the problem and how you can create custom rules to block or restrict such behavior.
Vigilance policy can be employed for every communication layer especially network with the help of the Intrusion Prevention System. On the other hand, for the application layer, a strong web application scanning (WAS) testing tool can be handy. This way, you do not have to hire a separate security team for web applications, and still be in control of attack logs and decisions to be taken on them.
Habit 4: Updating Regularly
It is actually the most obvious, yet overlooked security habit. Although there is nothing more tedious than updating software, patches, and fixes on multiple platforms and systems, it keeps your security mechanism on the toes.
Be it your operating system or malware scanning tool, no software is perfect. Statistics reveal that more than 90% of updates are security-based. In fact, developers work hard to discover vulnerabilities and coding patches before hackers could exploit them. Quite obviously, failing to update will increase breach risks and compromise your entire network. Other than that, updates are critical on server framework and configuration too.
Habit 5: Looking Beyond Compliance
The Payment Card Industry Data Security Standard has laid down the most trusted set of requirements to ensure credit card information handling and all websites should target its compliance, but it is only a place to lay down the security protocol, not an end to it.
Information security is rather an ongoing process that gets better with experience, data, and learning. Website owners must realize that compliance is the least one can do to improve security. Beyond that, there is a lot more to be performed at both internal and external levels. Innovative initiatives to secure communication and sensitive data should be encouraged within the organization.
Habit 6: Developing Layered Security Architecture
The Open Systems Interconnection conceptual model segregates communication layers into Psychical, Data Link, Network, Transport, Session, Presentation, and Application. Given that every abstraction layer can be compromised using different kinds of vulnerabilities, it becomes critical to developed layered security portfolio.
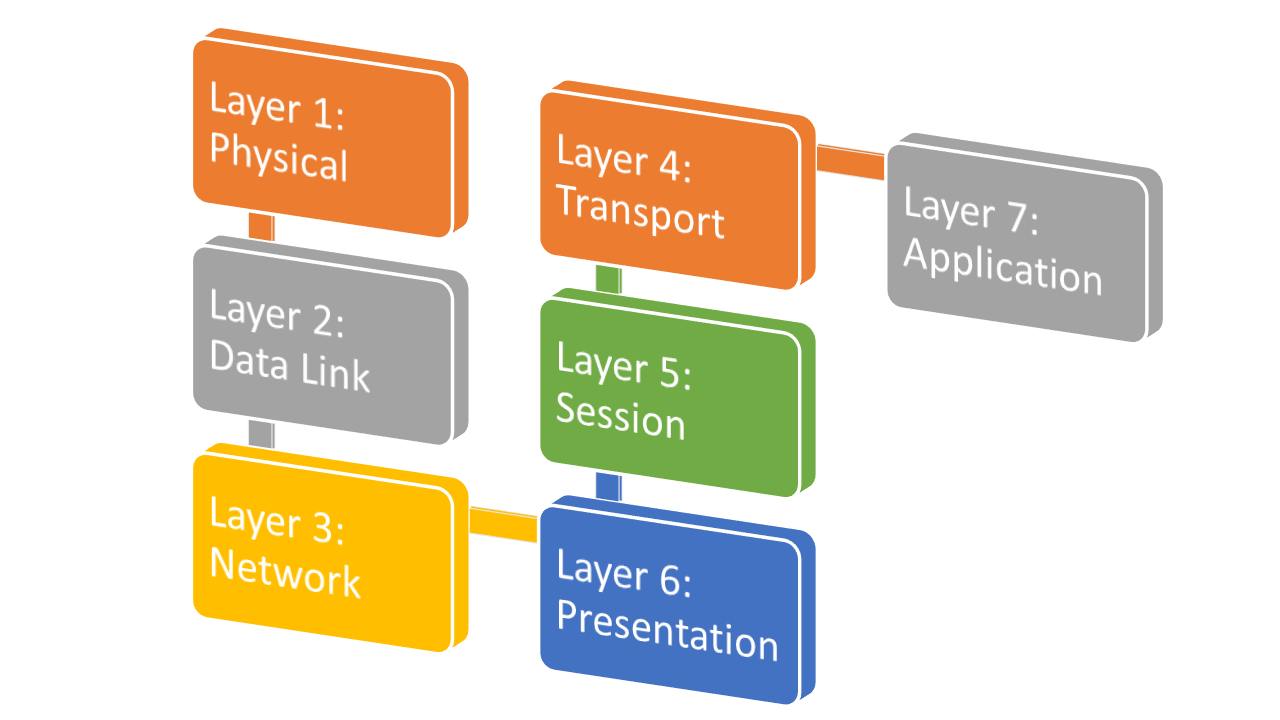
Open Systems Interconnection Model
Layered security comprises securing through psychical resources, disaster management plans, packet filters, malware and Trojan detectors in the system and SSL certificates. A lot of it is covered under the network firewalls and IPS.
However, website owners should also take web application security seriously given most of the attacks happen at Layer 7. As a matter of fact, Indusface research shows that organizations take 30 to 180 days to patch known vulnerabilities, which is plenty of time for attackers to exploit.
We recommend that vulnerabilities at Layer 7 should preferably be detected with web application scanner and should further be patched virtually with a web application firewall that restricts attackers from exploiting those vulnerabilities, till the time developers get their work done.
Habit 7: Budgeting Wisely
We’ve already discussed that more than 75% of the website attacks happen at Layer 7. But did you also know that still less than 18% of the total information security budget is allocated to application security? This huge gap is often neglected with excuses like there is not enough time to look for application-layer vulnerabilities continuously and then allocating time and money to patch them.
Looking at the attack patterns from recent years, application-layer attacks are going to increase in numbers and complexity. Information security research giant Gartner suggests a combination of static and dynamic web application testing backed by a web application firewall for instant virtual patching of the vulnerabilities. Website owners, management, and CISOs should look to disperse their security budget well and pay more attention to application security.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 19, 2015
March 19, 2015





