7 Quick and Easy Ways to Secure Drupal Website
With millions of users worldwide, Drupal is the market leader in the open-source CMS platform. Organizations are using this platform for flexible architecture, speed of implementation, digital innovation, a myriad of free-available community code, and scalability without the fear of software vendor lock-in. Moreover, every single core strategic initiative of Drupal comprises API-first, workflow, and media to make Drupal more ambitious.
However, in this digital landscape, every business worries about security vulnerabilities. The built-in Drupal security features help to mitigate this concern, but any business, which uses Drupal must take some additional steps to completely secure its CMS and keep the pack with its customer’s needs. This is particularly true for organizations, which are subject to compliance frameworks like PCI DSS, HIPAA, etc. Efficiently securing Drupal needs understanding of Drupal security best practices for maintaining it securely.
Drupal Security Vulnerability
Drupal enjoys a reputation as being a secure CMS than other CMS platforms. With the team of security developers who actively develop Drupal security modules, it instantly identifies, announces, and resolves the security issues. Further, being open source also helps Drupal to mitigate security issues, as anyone can examine its source code for vulnerabilities and highlight the fixes.
Despite this, Drupal security vulnerabilities do evolve, and remote code execution attack is one of the riskiest ones. In this attack, a hacker executes malicious software on the victim system, which hosts a Drupal CMS. Drupalgeddon2 and drupalgeddon3, are the two major attacks which exploited remote code execution vulnerabilities in Drupal 7 and 8. This Drupal vulnerability was fixed in 2018.
Other common vulnerabilities in Drupal include access bypass vulnerability that makes it possible for authorized access to content and DoS (Denial of Service) vulnerability which allows attackers to disable the Drupal websites.
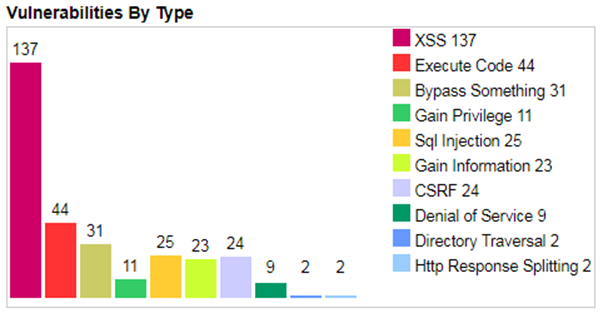
Image source: specbee
Top Drupal Security Best Practices to Follow
1. Check on Your User Roles and Block Access Permissions
Drupal offers multiple users and roles like admin, authenticated users, editors, anonymous users, etc. You can assign and grant permissions manually to each role once you install Drupal or add more modules. To protect the website, exercise the correct roles and file permissions like read, write, and modify. For instance, the anonymous user should possess the least permission like read-only.
If the permissions are loose, this could allow an intruder to access your sensitive files. It is also recommended to block access to important files like the upgrade.php file, authorize.php file, install.php file, and cron.php file.
2. Install SSL Certificate
The SSL certificate is dedicated to the secure processing of sensitive data. Many people argue that an SSL certificate is vital only for eCommerce sites, and informational and blog sites don’t need to maintain an HTTPS connection. But SSL encryption is important for the Drupal login page to secure your login credentials. Further, the SSL certificate offers several SEO and performance benefits, get an SSL certificate from trusted vendors like Indusface to secure data transfer on your Drupal website.
3. Be Smart with Your Usernames and Passwords
According to MobileIron, weak passwords remain the top cause for data breaches. 42% of organizations have been breached due to compromise in user password. Many people who use the easiest passwords like “12345” are more prone to a brute-force attack. Remember today bots are crawling the internet to spoof the login details.
Using a complex username and password is one of the easiest and most effective ways to strengthen Drupal security.
4. Limit the Number of Login Attempts
Limiting login attempts can aid you to avoid being a victim of brute force attacks. As one of Drupal security best practices, versions Drupal 7 and above restrict the login attempts to five per user within 6 hours. If those limits are exceeded, the user is blocked from further logins for 6 hours. If you’re using earlier versions, add a Drupal security module, which comprises a feature of restricting login attempts.
5. Keep Calm and Stay Up to Date
Keeping your Drupal version up to date is really the least action business can do to ensure website safety. Drupal contributors are always looking for Drupal vulnerability and security threats, which could spell destruction. When the contributors push out any new updates, they often include patches and fixes for security vulnerabilities. Delaying these updates can open the door for bad actors. Keep your Drupal extensions and themes up to date to stay away from website threats.
6. Perform Regular Drupal Site Backups
Website backup can aid you to restore your site in case any worst incident happens. In addition to Drupal core and module files, it is important to include all the vital things to your website functioning in your backup. This helps in quick recovery of your site after you’ve been breached with simple rollback.
It is also recommended to have a reliable backup before starting any update to your site, especially important when you are installing a module or theme for the 1st time.
7. Take the Advantage of Drupal Security Features
Drupal security modules can lock down your website and offer an extra layer of protection around it. These security features enable you to block security threats, enforce strong passwords, block malicious networks, scan for vulnerabilities, and much more. Here are the list of the Drupal security features that you must use on your site:
- Security Review Module – automates testing to uncover security mistakes
- Two-factor authentication – Adds an extra layer of authentication in addition to login page
- Password policy – this Drupal security module places another layer of security to login-forms to prevent bots and other security threats
- Content Access – Allows giving permission for content based on role and author
- Password policy – defines secure password policies
- ACL – the Drupal security feature provides access control lists
- Captcha – the Drupal security module to filter unwanted spambots
- Automated logout – log out users after a certain time period
- Session Limit – limits the number of sessions per user
- Hacked! – Security module to check if there are any changes in Drupal themes or core
Enhance your Drupal Security with Indusface
Regardless, how long you have been operating the Drupal website, optimizing site security can be a challenging task. To stay on top of the ever-changing compliance requirements and ever-evolving security vulnerabilities, partner with the Indusface team of experts who specialize in optimizing business-critical websites and apps including Drupal site, and can take your site security to the next level.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 25, 2021
March 25, 2021



