32 Cybersecurity Facts to Know
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedInMany information security lapses happened this year. Records were lost, money was lost, higher management professionals quit, and budgets were reshuffled to improve application security. Indusface brings all of this and a lot more. These important cybersecurity facts from across the world will help you devise powerful anti- breach strategies to keep your business secure and customers confident.
Data Breaches by Volume
1. A total of 750 data breach incidents have been recorded till November this year.
2. The number touched 783 in 2014 with a 27.5% rise compared to 2013. Going by the figures, we are most likely to cross last year’s figures.
3. About 177,837,053 records were stolen.
4. Banking, finance, and business sectors took the biggest hits with about 50% of the data breach incidents reported in these sectors.
5. Businesses and the banking/financial industry lost 21 million records in total, which crunched their business, stock value, and customer trust.
Key Learnings: Despite the rising cybersecurity awareness, businesses are still losing the data breach battle. In the coming year, it will be difficult for the new-age businesses to recover from bad reputation and goodwill damage especially against stiff competition that puts a higher value in garnering customer and business security.
Data Breaches by Cost
6. The average cost to the company per stolen record is $154 this year.
7. The highest per-record cost is for the education sector, which is $300.
8. The figure is $215 per stolen record for the finance and banking sectors.
9. The United States and Germany spend most on data breaches. It is around $230 and 224 respectively.
10. The total average cost of a data breach to a company is $3.79 million this year.
11. In 2015, ‘Lost Business’ has been the highest data breach cost component for organizations. The average amount spent is $1.57 million, which was $1.33 million last year.
12. ‘Lost Business’ takes into account reputation damage, goodwill loss, customer disinterest, and increased customer acquisition spending.
Key Learnings: Although not every business loses millions of dollars directly on small data breaches, other repercussions are nasty. For instance, recently TalkTalk stock tanked 10% and Ashley Madison CEO has to resign after the breaches. In a recent survey, a data breach has also been linked to a loss of traffic and customers.
Distributed Denial-of-Services
13. The United States and China are the top bot-based DDoS attack sources. The availability of cheap cloud computing and hosting in these countries explains that.
14. Most DDoS attacks are used to cloak other attacks. Something that had happened with the infamous Sony breach incident in 2014 too.
15. In 2015, DDoS was extensively used for holding companies against a ransom. Several banking and financial companies received threats to pay millions or suffer from full-blown DDoS attacks that last for days.
16. Companies spent anywhere up to $19, 000 to resolve DDoS attacks on their servers.
17. Malicious or zombie bots and machines are available for just $5/hour. Many rival companies launch a small-scale DDoS attack to disrupt the services of their competitors.
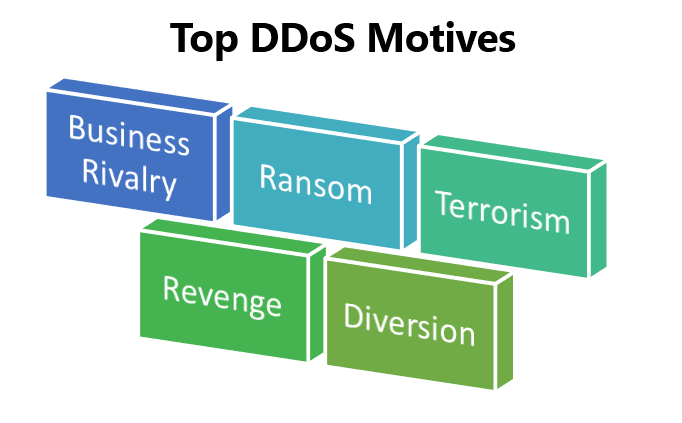
18. No matter what the volume is, DDoS attacks are difficult to stop at every level.
Key Learnings: You can never be fully prepared for application-layer DDoS attacks. It’s an ever-standing threat that can only be resolved with close app traffic monitoring. Indusface Total Application Security monitors DDoS threats and diffuses them before they cause server or application performance damages.
Cybersecurity Budgets
19. The Information Security budget in Asia had fallen by $0.6 million last year. This year too, the figures haven’t improved.
20. On the other hand, information security spending increased by 12% in 2014.
21. Information security makes just 11% of the total IT budget.
22. However, this budget has increased over the past few years. It is expected to rise to 28% by the next year.
23. Chief Internet Officer (CIO) and Chief Technology Officer (CTO) largely decide the security spending structure.
Key Learnings:
Mobile Application Security
24. 1 in 4 Android devices encounters a threat every month.
25. Data breaches can happen through smartphones and tablets.
26. Ios vulnerabilities have increased by 262% compared to 2011.
27. Around 56% of enterprises accept that they are likely to have sophisticated threats in their applications.
Key Learnings: As the world moves towards mobility, app testing will become critical. It’s not just about BYOD security, business apps can be hacked like web apps to crash the server or steal data. Here’s a detailed view on that: Mobile Application Risks Part 1 and Part 2.
Application Layer Statistics
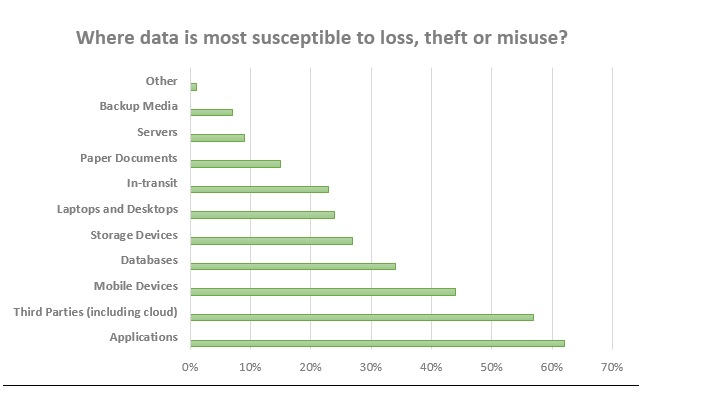
28. 62% of the IT management and IT security practitioners from 42 countries including North America, the Middle East, Europe, Latin America, Africa, and the Asia Pacific regions think that data is lost through the applications.
29. In fact, 34% also believe that cybersecurity risks are the highest at the application layer.
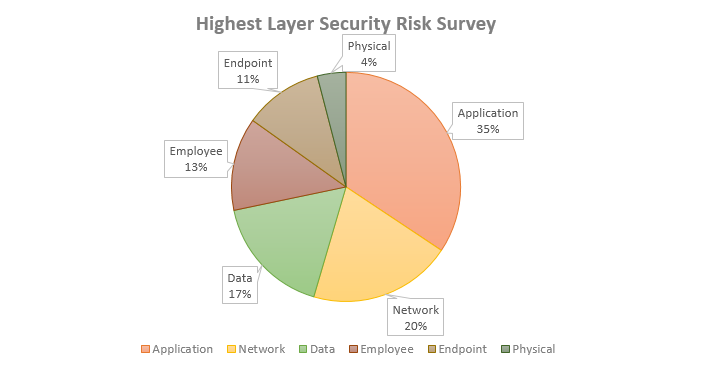
30. Gartner says that 70% of the cyber-attacks happen at the application layer.
31. 44% believe that a web application firewall is an important enabling technology.
32. Did you know that 83% of the hacks and data breaches could have been avoided beforehand with a few changes?
Key Learnings: Today web applications are the doorways to business. The command communication, transactions, shopping carts, and whatnot. Isn’t it obvious that hackers will go after apps to steal Personally Identifiable Info (PII), credit card and bank details, and website accounts? Unfortunately, most businesses still adopt the ‘network layer is everything’ approach. Application layer security awareness is mandatory where the focus should be on continuous weakness detection, attack prevention, and expert monitoring.
Sources
- Indusface Blogs and Infographics
- Ponemon Institute of Research Reports
- Identity Theft Resource Center (ITRC)
- CyberEdge Group 2015 Cyberthreat Defense Report
- Gartner
- EY Global cybersecurity Survey
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 December 29, 2015
December 29, 2015






