The Comprehensive Web Application Security Checklist [with 15 Best Practices]
Over 75% of all cybercrimes primarily target web applications and their vulnerabilities. Attackers focus on exploiting weaknesses such as design flaws, vulnerabilities in APIs, open-source code, third-party widget issues, and access control problems.
A recent study predicts that all this cybercrime will cost a massive $5.2 trillion by 2024 across all industries. How do you protect your web application from all the risks out there?
Here is a go-to web app security checklist to get started.
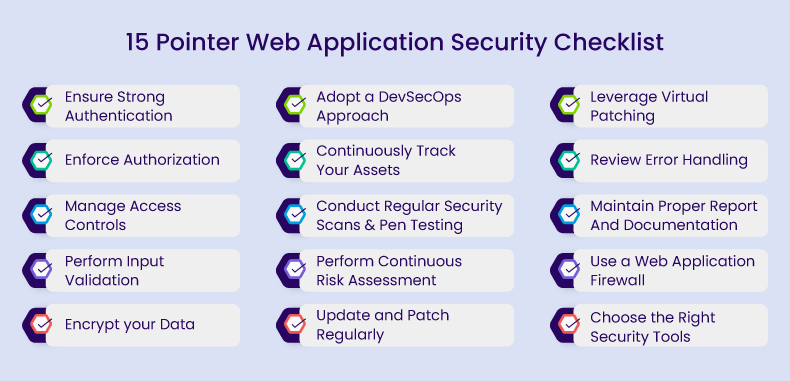
A 15-Step Web Application Security Checklist
1. Ensure Strong Authentication
Authentication is a fundamental pillar of web application security, as it establishes the identity of users interacting with your application. Without strong authentication measures, malicious actors can easily impersonate legitimate users, gaining unauthorized access to your application and its data.
Here’s what to include in your authentication checklist:
- Strong Password Policies: Enforce strong password policies, including complexity requirements and regular password changes.
- Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security by requiring users to provide multiple forms of verification.
- Password Storage: Employ robust hashing and salting methods to securely store passwords, fortifying your defense against potential data breaches.
- Account Lockout Mechanism: Implement an account lockout mechanism to prevent brute force attacks on user accounts.
2. Enforce Authorization
Without proper authorization controls, unauthorized access, data breaches, and potentially malicious activities are risky. By implementing robust authorization, you can ensure that sensitive data and functionalities are only accessible to authorized users, reducing the attack surface and enhancing overall security.
To ensure proper authorization, consider the following:
- Role-Based Access Control (RBAC): Implement a role-based access control system that assigns roles to users and specifies what actions each role is allowed to perform.
- Least Privilege Principle: Users should have the minimum level of access required to perform their tasks, reducing the risk of unauthorized actions.
- Session Management: Use secure session management to ensure that users are only authorized during their active sessions.
- Audit Trails: Maintain audit logs to track and review authorization activities, enabling the detection of suspicious or unauthorized access.
3. Manage Access Controls
Proper access controls are important for various reasons:
- Data Privacy and Confidentiality: Access controls protect sensitive information and maintain data privacy by limiting access to authorized individuals only.
- Preventing Unauthorized Modifications: Access controls prevent unauthorized changes to data or resources, ensuring data integrity.
- Preventing Data Leaks: Unauthorized access can lead to data leaks or data breaches, which can be costly in terms of financial and reputational damage.
- Efficient Resource Allocation: Proper access controls ensure that resources are allocated efficiently by restricting access to those who genuinely need it, enhancing performance and security.
4. Perform Input Validation
Even a simple name or a photo uploaded can become trouble if not checked properly. It’s like letting a stranger in without asking who they are. This could lead to your website crashing or sensitive data being exposed.
To ensure your web app runs smoothly and stays safe, validating and verifying everything in users’ input is crucial. This way, you create a secure online environment while providing a positive experience for your users.
Here’s how to ensure proper input validation:
- Whitelisting: Use whitelisting to allow only specific, known inputs and reject all others.
- Blacklisting: Employ blacklisting to block known malicious inputs, such as dangerous characters or patterns.
- Parameterized Queries: Use parameterized queries to prevent SQL injection attacks by separating user data from SQL queries.
- Regular Expression Validation: Validate user inputs using regular expressions to ensure they match the expected format.
5. Encrypt your Data
The next vital component of your web application security checklist is data encryption. It involves encoding sensitive information to protect it from unauthorized access and maintaining data confidentiality. Here’s what to consider for data encryption in your web application:
- SSL/TLS: Implement SSL/TLS for secure data transmission, ensuring data is encrypted between the client and server.
- Encryption at Rest: Use encryption methods to protect sensitive data stored in databases or on the server.
- Key Management: Properly manage encryption keys and ensure they are stored securely.
- Data Masking: Implement data masking for sensitive information, displaying only the necessary parts to users.
6. Adopt a DevSecOps Approach
A DevSecOps approach incorporates security experts into the development process, seamlessly integrating security testing at every phase of the software development lifecycle. This includes automating security controls, particularly within the CI/CD pipeline, which is crucial for constructing a secure web application from its inception rather than treating security as an add-on.
A wide range of security tools are used in DevSecOps to achieve high automation levels and enhance the security of web applications during their development. Check out our detailed blog on the vital role of WAAP platforms in the CI/CD Pipeline.
7. Continuously Track Your Assets
Attackers like to target forgotten or shadow assets because they are easier to test without causing damage to active sites.
Visibility is the initial step to gain insight into your organization’s security posture. After all, you can’t protect what you can’t identify. It’s crucial to precisely understand the assets that compose your applications and software production infrastructure. This knowledge forms a cornerstone of your web application security checklist.
Follow these best practices to ensure an efficient asset discovery process:
- Define Clear Objectives: Start by outlining the aims and boundaries of the asset discovery process, aligning it with the organization’s requirements.
- Collaborate Across Teams: Engage stakeholders from diverse departments, such as IT, security, and compliance, to compile a comprehensive inventory of assets.
- Utilize Automated Tools: Choose an application security product that provides complete visibility and control over external assets.
- Maintain Data Accuracy: Regularly update and verify asset information through well-structured procedures to confirm the correctness of the discovered assets.
8. Conduct Regular Security Scans and Manual Pen Testing
Two crucial elements your web application security checklist cannot be complete without are:
Regular security scan
Intelligent scanners run automatically on a daily and on-demand basis to keep identifying all known vulnerabilities in the application. The scanners systematically analyze various application components, including input fields, APIs, and databases, to identify potential security flaws such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Pen testing
Conducting penetration testing is essential for uncovering security vulnerabilities throughout your web application, incorporating its backend and databases. Unlike automated tools, manual testing by certified experts can reveal unknown vulnerabilities and business logic flaws.
Incorporate the best practices outlined in our web application penetration testing checklist blog to assess your security posture.
The embedded DAST scanner within AppTrana can be tailored to perform daily scans on web and API applications or at a frequency of your choice. It augments automated assessments with manual penetration testing conducted by security experts who identify business logic vulnerabilities.
9. Perform Continuous Risk Assessment
In 2021, organizations lacking a zero-trust approach incurred an average breach cost of $1.76 million higher than organizations that embraced zero trust as a security strategy.
While apps are not entirely un-hackable, risk assessment and prioritization help you set realistic goals, policies, and security standards. You need to keep assessing your organization’s risks and keep them within your tolerance levels.
Your assessments should address the following queries:
- What are the most critical IT assets for your organization?
- Which types of data breaches could significantly impact your business’s success?
- What are the potential threats to your organization and their origins?
- What security vulnerabilities exist, both internally and externally?
- What would be the consequences if your organization’s security weaknesses were exploited?
- How likely is it that a security weakness will be exploited?
- What security threats or cyberattacks could disrupt your organization’s ability to operate?
10. Update and Patch Regularly
It is not enough for you to identify vulnerabilities; they must be immediately remediated. Security patches are updates aimed at fixing identified security vulnerabilities. These should be applied as soon as they become available.
This practice ensures that your web application remains resilient against emerging threats, minimizes the risk of security breaches, and upholds data integrity, user trust, and compliance with regulatory requirements, making it a critical and ongoing element of your security strategy.
11. Leverage Virtual Patching
There are scenarios where software vendors may not have released patches for known vulnerabilities, or applying patches may disrupt critical operations. Virtual patching provides an effective alternative.
Virtual patching is a rule set or configuration that blocks exploitation attempts and mitigates risks until a permanent fix is available. By doing so, virtual patching minimizes the window of opportunity for attackers, reducing the likelihood of successful exploits. This dynamic approach is particularly valuable in protecting applications from zero-day vulnerabilities or where patch deployment could lead to operational disruptions.
AppTrana can virtually patch high-risk vulnerabilities and stop attacks directly at the WAAP without requiring code modifications. This presents an excellent opportunity to decrease the vulnerability exposure period, allowing development and quality assurance (dev/QA) processes to catch up and apply patches to the code later.
12. Review Error Handling
This is another indispensable element of the web application security checklist. When logging into a web app, if the user encounters a detailed error message stating, “The password you entered is incorrect; please try again.” While this seems helpful for him, it could be a gift to a cybercriminal.
To prevent this, use concise error messages like “Invalid username or password.” Avoid giving clues or sensitive information and ensure consistency in error messages. Inconsistencies may inadvertently reveal information to malicious actors, so it’s important to maintain a uniform approach.
13. Maintain Proper Report And Documentation
Imagine a security breach occurs, and your organization needs to respond quickly and effectively. Proper documentation in this context would involve having an incident response plan, clear records of what security measures were in effect, and detailed logs of the breach, including its timeline, affected systems, and the actions taken to contain and mitigate the incident.
Thanks to thorough documentation, the security team can promptly identify the breach source of the compromised data and implement countermeasures to mitigate further damage.
This expedites recovery, helps assess the incident’s impact, and provides vital compliance and risk assessment information. Furthermore, consistent documentation helps track security improvements, strengthening the web application’s security posture.
Uncover the specific requirements for application security within various compliance frameworks.
14. Use a WAF (Web Application Firewall)
WAF plays a vital role in protecting web applications against dangers from compromised or malicious endpoints, functioning as reverse proxies rather than traditional user-focused proxy servers.
One of the key advantages of WAF lies in its agility, allowing for the quick adaptation of security policies to combat ever-changing attack vectors. For instance, during a DDoS attack, the WAF can promptly apply rate-limiting measures through policy modifications. Check out the six key considerations in deploying a WAF, here.
15. Choose the Right Security Tools
Your web application security tools should not merely function as repair agents like traditional antivirus software. Instead, they should act as collaborative allies, providing invaluable support to your security team and web application developers in various capacities, including offering proof, expertise, monitoring, and management.
A critical decision-making factor is the issue of false positives. When security engineers or developers cannot trust the accuracy of a tool’s alerts, they are compelled to validate every piece of information it provides. It is recommended to choose the vendor who are bundled with managed service to handle the false positives.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 October 31, 2023
October 31, 2023