API Discovery: Definition, Importance, and Step-by-Step Guide on AppTrana WAAP
The growing use of APIs in various business areas exposes organizations to new security risks. An analysis of data breaches reveals that US companies could face losses ranging from $12 billion to $23 billion in 2022 due to compromises linked to APIs.
Lack of visibility plays a major role in the rise of API breaches. The lack of visibility inherently creates blind spots. How do you overcome the problem of hidden APIs?
To better protect your API, you should maintain an inventory of APIs, track the API usage regularly, and fix vulnerabilities in your APIs. And this process is known as API discovery.
Notorious API Hacks in the Recent Past
With increasing dependency on APIs, APIs have become the prime target for attackers. Recent reports show this has already started.
Malicious API traffic rose by 681% in 2021. Experts estimate that insecure APIs cost businesses up to $75 billion annually.
One of the disastrous realities of API abuse is providing access to a massive amount of data.
In the case of the Twitter breach, the attacker gained access to 5.4 million users’ data.
In Jan 2022, Twitter revealed that a vulnerability in API led to data exposure. On top of that, Dec 2022, the threat actor sold 400 million Twitter profiles on the dark web.
The Experian API leak is another example of API insecurity. The company recently faced this situation when one of its API bugs possibly leaked credit scores with minimum details.
Experian patched this vulnerability immediately. However, the concern is that the same weakness may be available on countless other websites.
The Risks Posed by Insecure APIs
API risk is a growing problem with significant risks to your business, including:
- Data losses – As API connects external applications and users with your internal apps. They are a possible route to your sensitive data.
- Service disruption –If an API is not properly maintained, it may not be able to handle a large volume of traffic or requests. It can cause service disruptions.
- Loss of reputation – Security breaches can bring litigation, fines, and damage to reputation. A single data leak can result in irreparable damage to your brand.
The first step in preventing API breaches is maintaining an API inventory. You can easily do that with Indusface’s API Discovery product bundled as part of AppTrana WAAP. After all, if you are unaware of the existence of APIs, you can’t secure them.
What is API Discovery?
API discovery is the process of identifying and cataloguing the APIs that are in use within an organization. API discovery aims to create a comprehensive inventory of all APIs, including internal and external ones.
Why is API Discovery Essential for API Security?
How well do you know your APIs? Have you ever asked the questions like:
- How many APIs are running in your organization?
- How frequently were they changed/updated?
- What is the impact of those changes on your application functionality?
- When you launch a new version of an API, what happens to the older version?
- How do you find an API that was not an official one, but a developer ended up creating it to reduce rework?
The biggest problem in API security is unknown as in not knowing what APIs exist. Companies risk not knowing what they have and end up losing control of them. OWASP API Top 10 has a list of top vulnerabilities on APIs. Specifically related to API inventory are shadow, zombie and rogue APIs.
Shadow APIs
Shadow APIs are unmanaged or unprotected APIs that escaped the security team’s attention. They result in a security gap.
A recent report highlighted that out of the 16.7 billion malicious requests observed, 31% or 5 billion were on shadow APIs.
The threat vectors in the OWASP API top 10 2023 grow with the extension of these unprotected APIs. Shadow APIs put your data at risk at any time. With data exposure, attackers can carry out a wide range of attacks.
Zombie APIs
Zombie APIs are depreciated APIs that are still running in the background. Everyone assumes that they are disabled. But these forgotten APIs expose security vulnerabilities as they don’t have the latest updates.
Zombie APIs commonly arise when a new version replaces the old one. Few businesses leave both versions accessible to support their customers who have old devices. However, these APIs pose security risks to the company and the customers.
For example: Suppose V17/profile/edit mandates authentication and V4/profile/edit doesn’t. In such cases, the old APIs left the door open to misuse.
Rogue APIs
Rogue APIs are APIs that are not officially sanctioned, controlled, or authorized within an organization’s infrastructure. These APIs may be introduced by individual developers or third-party applications without proper oversight, potentially leading to security vulnerabilities and compliance issues.
An instance of a rogue API involves a third-party integration with a company’s internal systems, bypassing proper authorization channels, and leading to data leaks and unauthorized access.
The Role of API Discovery
Once the inventory of APIs is created, assessing the security risks associated with each API is possible. You can also implement appropriate controls and countermeasures to mitigate those risks.
Additionally, regular monitoring and testing of the APIs can be used to detect any new vulnerabilities or misconfigurations that may arise over time.
However, most companies are taking limited steps to discover API endpoints. Why is that?
Hidden Obstacles in API Discovery
It is hard for an organization to map or keep a complete inventory of API endpoints. There is so much diversity and complexity; hence it is a major target for attackers.
Here are a few obstacles that prevent API discovery:
Lack of Awareness
Lack of understanding is one major issue that significantly impacts API discovery. Many organizations lack awareness about their risks with APIs. They fall into one or more of these categories:
- Lack of consumption awareness
They think they are not consuming any APIs. However, the APIs are everywhere, and they may be using them in some way in their organization. Even if they are aware, they assume they have track of all the APIs.
- Prioritize APIs based on traffic volume
Organizations may overlook APIs that have low traffic volume. Attackers don’t target APIs based on how much traffic flows through your APIs. They care about APIs, which are likely to expose more sensitive data.
- Assuming APIs are secure and left untouched
The security team may think that all APIs are protected in their environment. However, the reality is that organizations expose APIs externally for various reasons without their knowledge. Testing purposes, 3rd party development access, and partner demos are a few of them.
These gaps create inaccurate documentation which lacks details about unknown functionality and missing endpoints.
APIs Are Not Static and Evolve Constantly
Software changes regularly. So do the APIs. Many businesses are changing existing APIs or adding new APIs every week. Most of these updates are not managed by security experts.
It is challenging for organizations to keep track of rapid updates. It is also tricky to understand how those updates affect the overall product.
API Management Burdens
The management gap is the crux of the API discovery issue. The lack of API visibility is not just due to legacy APIs lacking security updates. The more APIs you build, the harder it becomes to track.
Software development involves hundreds of APIs. The APIs used in a given app are independent of each other. Further, there is no one place to look for all APIs. Some APIs come from code repositories. And Internal teams may be developing some APIs.
API documents from developers are often incomplete. API documentation needs frequent updates in its existence. A static documentation or one-time API discovery process is pointless. It becomes outdated.
Reducing the discovery gap is the prerequisite for any engineering team looking to reduce API risks. API protection tools should ensure effective protection by eliminating the elements causing hindrances in API discovery.
Discover, Analyze and Secure APIs with AppTrana WAAP
Having a complete API inventory is not where the API security starts and ends. While maintaining continuous and up-to-date API inventory, it is important to risk rank the API portfolio and protect the risks proactively. API protection from AppTrana WAAP helps you discover APIs, scan APIs for vulnerabilities, and finally protect them through positive security model automation.
Here is a quick walkthrough on how to onboard the site on AppTrana WAAP and how the APIs are discovered with the AppTrana API Discovery feature:
Continuous Discovery and Inventory of All APIs
AppTrana WAAP provides comprehensive visibility into API requests as all traffic flows through it. This enables automatic API discovery, which occurs every 24 hours.
You can discover, track, and create an inventory of all APIs with automatic API discovery. It puts spotlights on
- APIs with well-published specification
- Legacy APIs without API specification – Zombie APIs
- Hidden API endpoints that are not documented – Shadow APIs
Go to AppTrana >> Protect>> API security policies >> Select the Domain >> Discovered APIs to see the list of APIs discovered in the selected domain, the method of APIs, and their path as shown below:
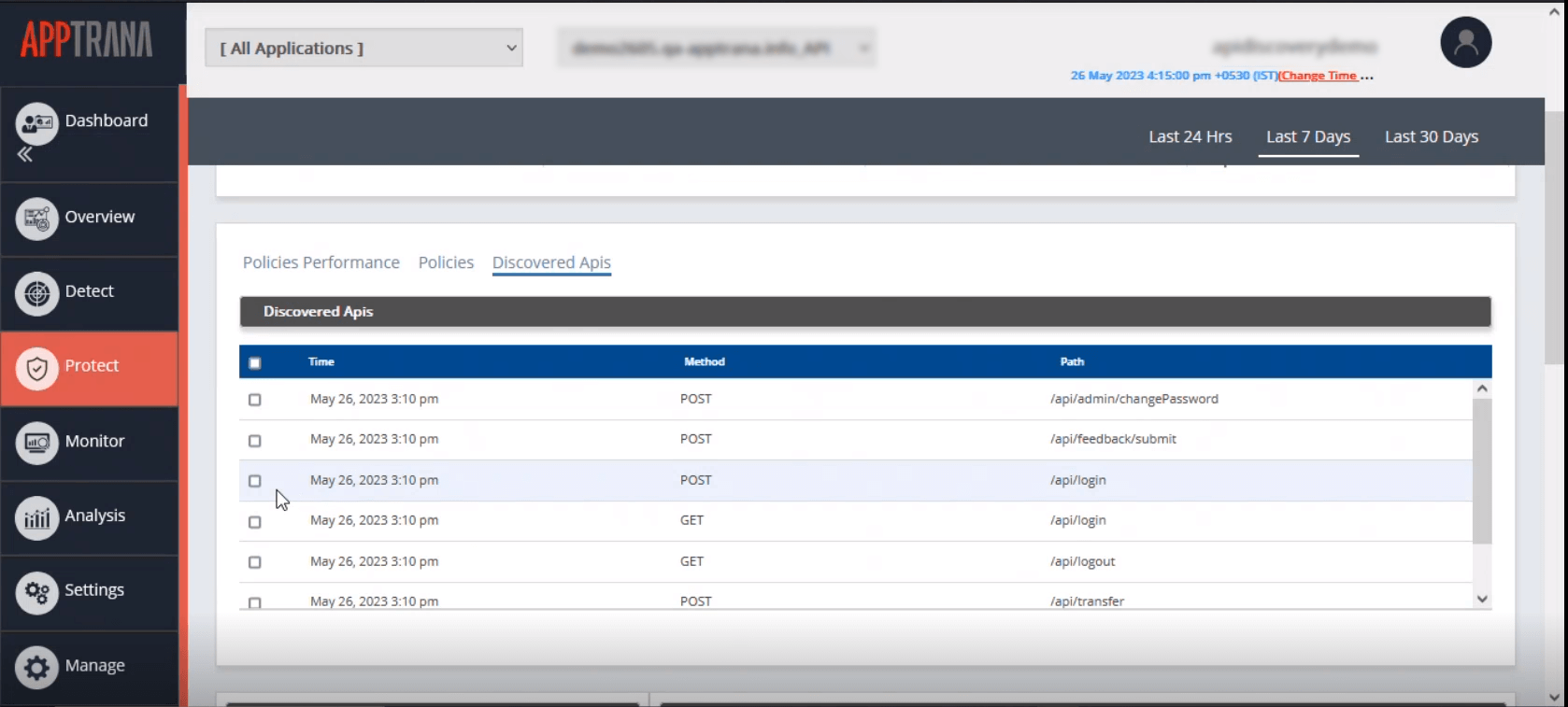
Continuous discovery ensures up-to-date API inventory when new technology is added, or your apps evolve.
AppTrana WAAP API Discovery – How Does it Work?
For AppTrana an API is method + URI Path.
For example, for the YouTube API,
GET youtube/v3/playlists,
PUT youtube/v3/playlists,
POST /api/v1/license
indicate different APIs – list, insert and update playlist, respectively.
The first part of the discovery is identifying unique APIs from the large number of requests we see. The main complication is handling path parameters, i.e., dynamic values in the URI path used to pass parameters.
For example:
/api/v2/license/123
/api/v2/license/456
...
the last part of the URI path is a dynamic parameter: the customer ID. The discovery process will identify such dynamic parameters. In many cases, determine the parameter type.
This will result in discovered APIs like
/api/v2/license/{integer_param1}<.code>
This process is repeated for every URL, and the discovered dynamic parameters and types could be refined as further requests are typically processed by generalizing the type.
Once all APIs are discovered, they are categorized by endpoint depending on the base path.
This is a grouping exercise for easier management. It involves grouping a flat list of hundreds of discovered APIs into a few top-level endpoints/categories like a customer, product, admin, license, etc.
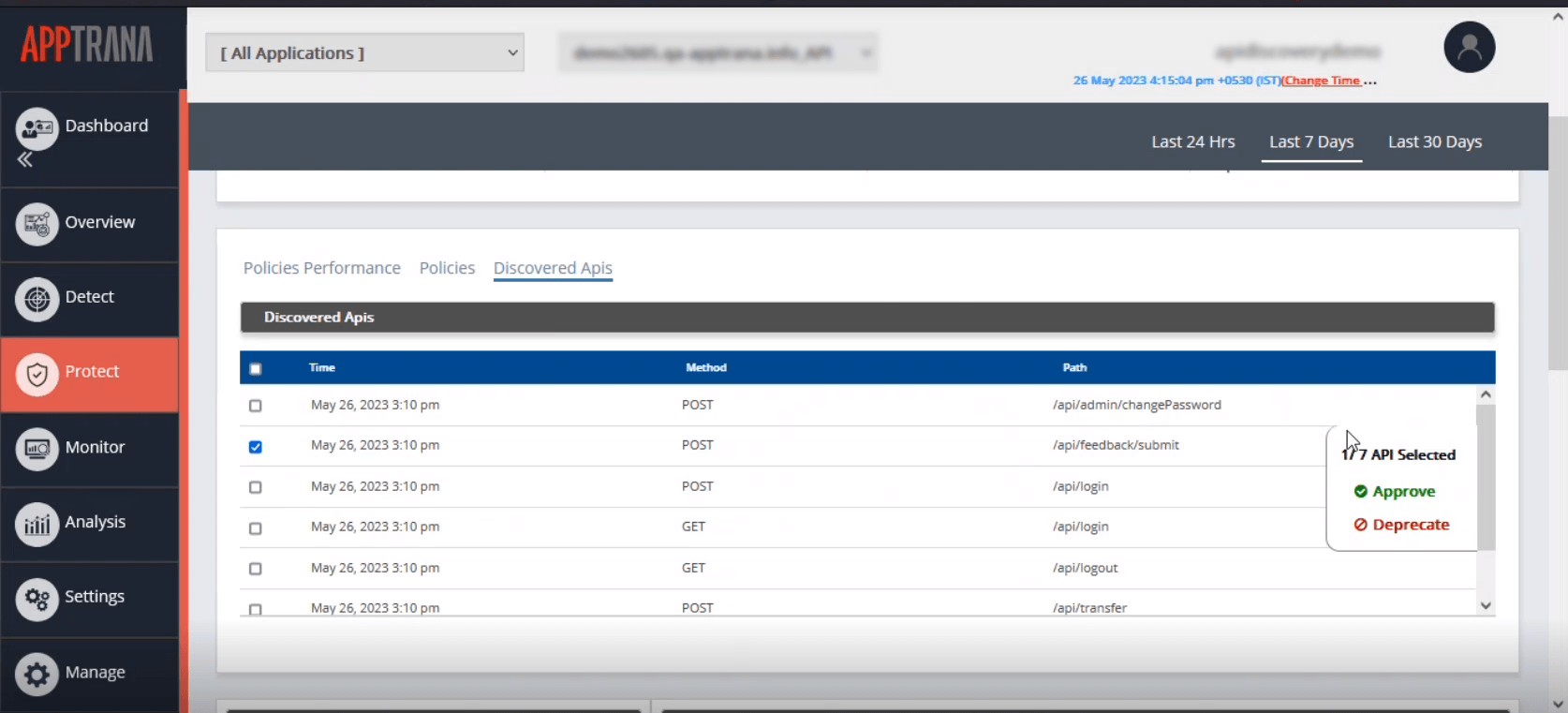
In addition to listing the APIs, AppTrana also offers the following options:
| Approve | Adding the valid API(s) into the Swagger file to enforce the positive security model | |
| Deprecate
|
Deprecate only | Deprecate API(s), as they are not currently usable but might be helpful. |
| Block | Block all incoming calls from the selected API(s) as they are no longer being used | |
Secure APIs with the Positive Security Model
API discovery plays a vital role in building a secure environment, and AppTrana offers protection for your critical APIs by utilizing the API inventory you have profiled. Additionally, AppTrana seamlessly integrates predefined policies and automatically generates positive security policies using your organization’s OpenAPI specification (also called Swagger file).
Addressing False Threat Detections
AppTrana enhances the accuracy of detections by separating blocking decisions from initial detections. The discovered APIs will be automatically added to the swagger file and listed in the policies section. However, the positive security model will only be enforced on these APIs when the user enables the policy.
The screenshot illustrates how users can influence or customize the security policies applied to their API:
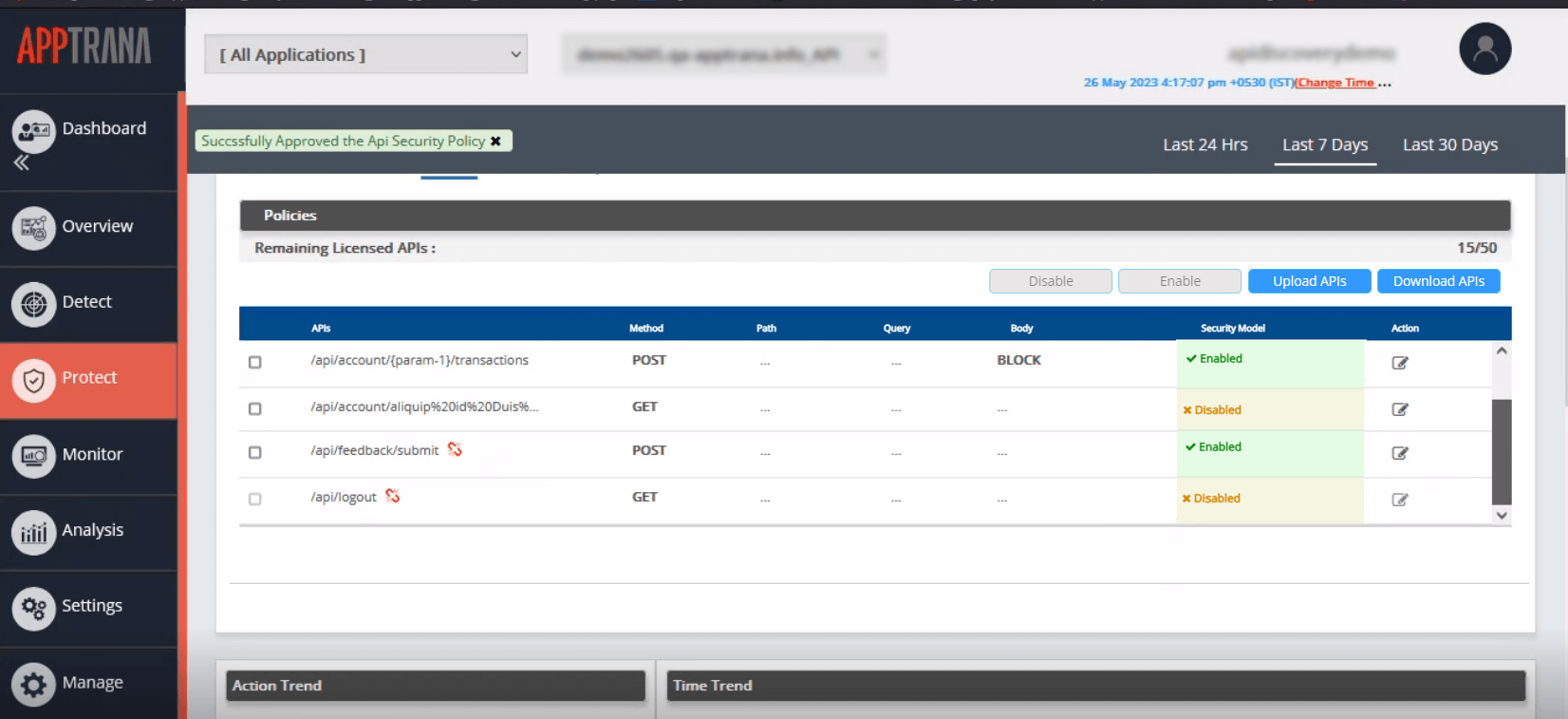
- APIs that have been approved and have the positive security model enabled.
- APIs that have been approved but have the positive security model disabled.
- APIs that have been deprecated but still have the positive security model enabled. (The deprecated APIs are indicated with a symbol next to their name.)
- APIs that have been deprecated and the security model is disabled.
Security Analytics and Trends
AppTrana takes API security to the next level by incorporating vulnerability analytics, providing an overview of the security and quality of all APIs in your organization.
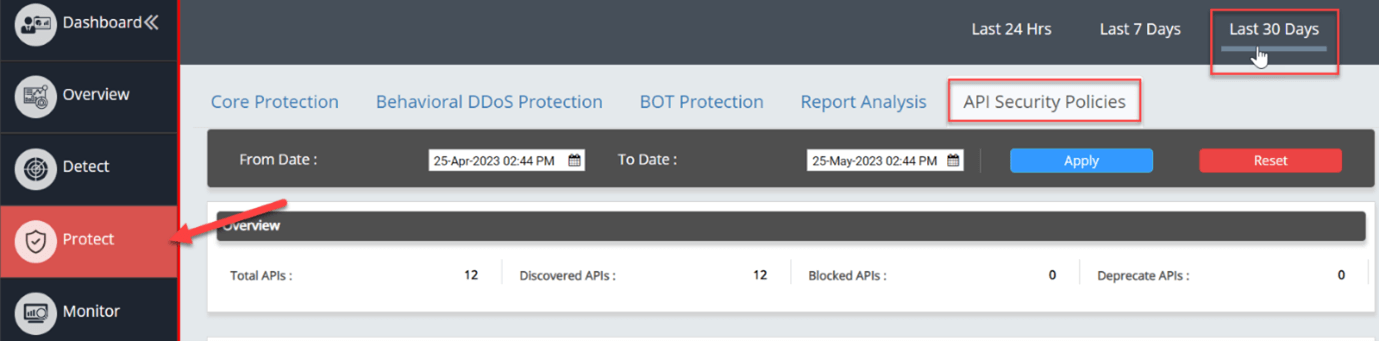
Select Protect > > choose website> > API Security Policies and select any time span such as the Last 24Hrs (or) Last 7 Days (or) Last 30 Days to get overall visibility of the API protection instance.
The overview section displays the total number of APIs, newly discovered APIs, blocked APIs, and deprecated APIs.
Policies Performance section collates the information from all the active API security instances into the graphical dashboard. It offers two views, including details like the top 5 APIs that receive malicious hits and the total number of requests per API.
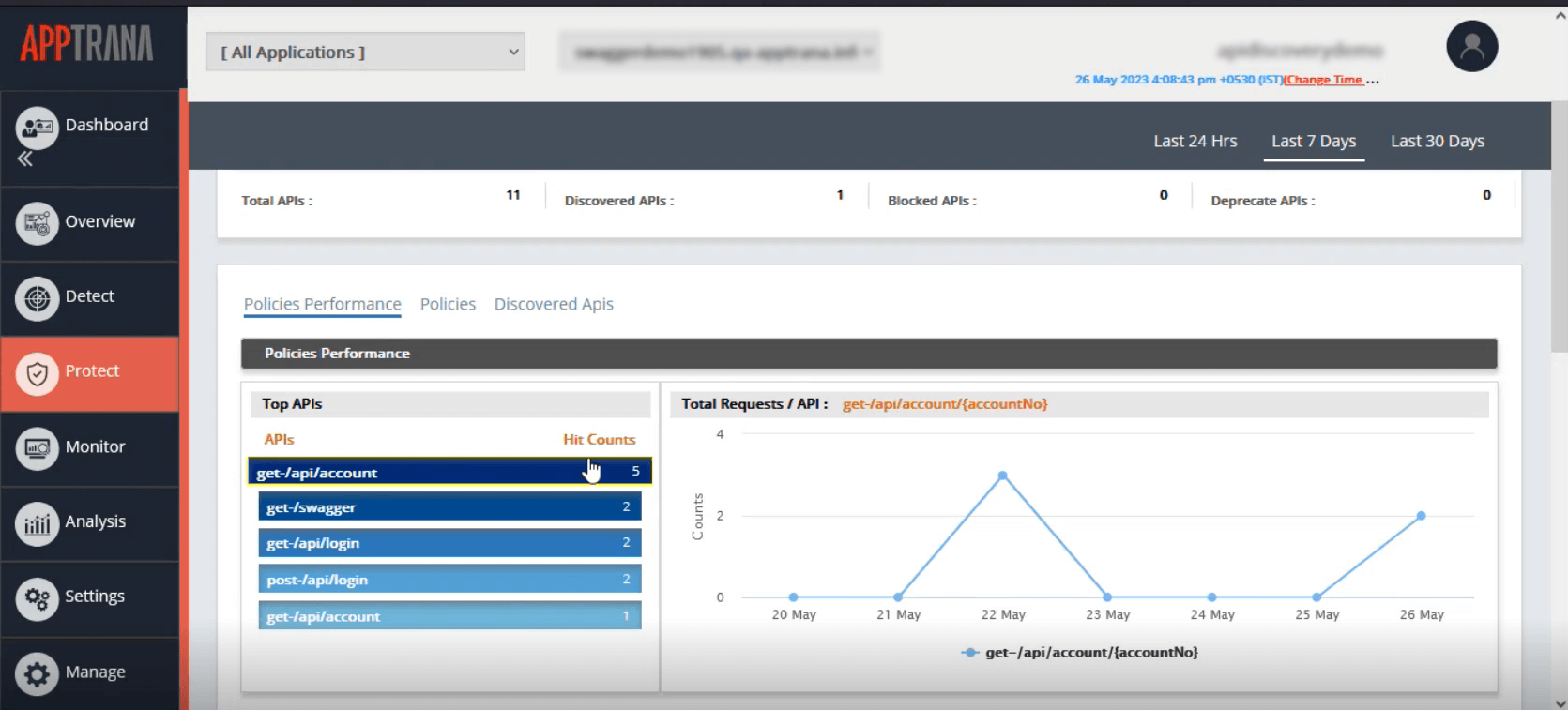
AppTrana WAAP also provides analytics for policies to illustrate how well your APIs are being protected. The policies section has an overview of API security status:
- Action trend – Total percentage of allowed and blocked APIs separately
- Time Trend – Total count of API requests allowed and blocked with respect to time
Request details section can tell you the details of malicious requests received from the APIs, along with the time, origin of the country request, IP address, and the action taken.
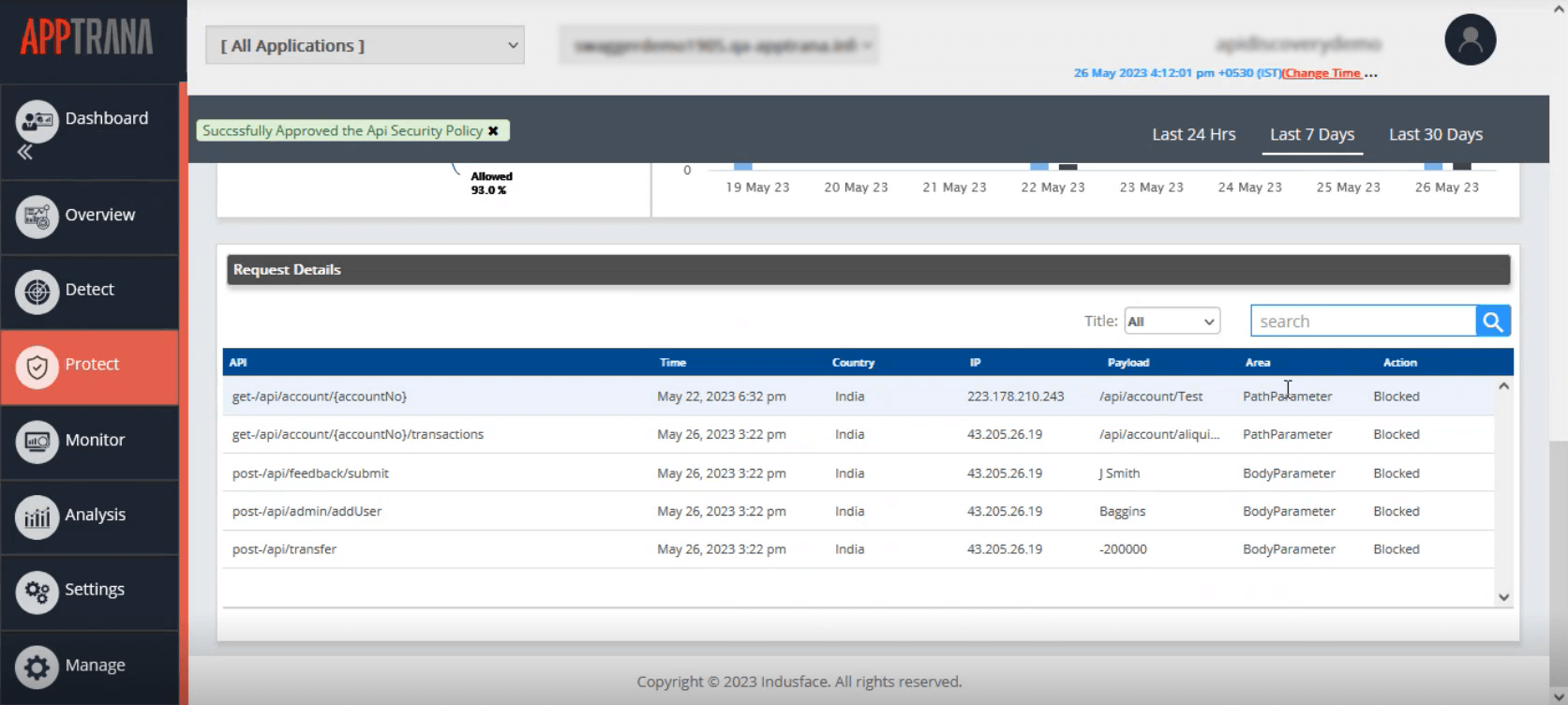
With this summary, you can track–
- Which APIs are risky?
- Where are these APIs called from?
- Who evokes these APIs?
- What is the frequency of these calls?
API discovery is essential for any organization that wants to protect its data and systems from potential threats.
Don’t wait for a security incident to occur; act now with AppTrana WAAP – Discover the power of AppTrana API security today by signing up for a free trial.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 January 17, 2024
January 17, 2024



