API2:2019 Broken User Authentication: The What, Impact, Sample Exploit, and Prevention Methods
What is API2:2019 Broken User Authentication?
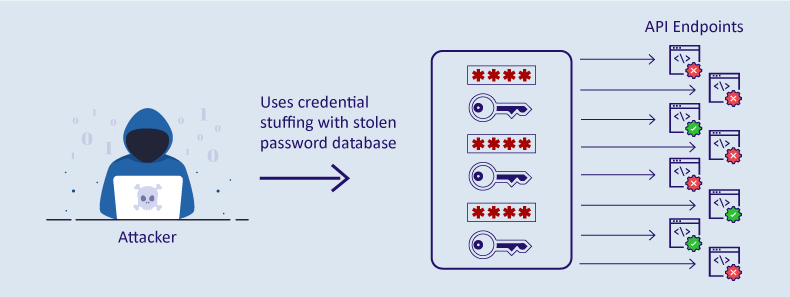
API2:2019 Broken User Authentication happens when an attacker bypasses an API’s authentication and authorization mechanisms and gains access to sensitive data or functionality that should only be available to authorized users.
Impact
As per OWASP Top 10 API risk rating, broken user authentication has a technical impact score of 3, which is severe. As we have seen, authentication systems are at the core of API security. When you don’t properly implement these mechanisms, your apps and APIs are vulnerable to data breaches and leaks.
Attackers gain access to key functionalities and data that they can use, modify or delete data. For instance, there is an authentication flaw in the systems designed to share criminal records within the police department. This authentication flaw lets anyone view and update criminal records by calling on APIs. And that is dangerous.
Attackers may exploit broken user authentication to engage in account takeover and further malicious activities such as fund transfers, phishing, spreading malware, etc.
Exploitability
Broken user authentication has an exploitability score of 3, as per OWASP. An exploitability score of 3 means these flaws are easily exploitable for attackers.
When weak passwords cause broken user authentication, attackers can easily buy stolen credentials on the dark web. Since users tend to reuse credentials across devices and platforms, they may be able to hack into several of their accounts using stolen credentials.
For performing brute force attacks and credential stuffing, attackers can access bad bots that minimize manual efforts in these kinds of attacks.
Prevalence
As per OWASP, broken user authentication has a prevalence score of 2, meaning it is a common API risk. It is prevalent because API authentication is complex and challenging for developers and security engineers to implement, especially in public-facing APIs. Their assumptions, lack of awareness, and lack of context pave the way for poor implementation of authentication mechanisms in APIs.
When does API2:2019 Broken User Authentication Vulnerability Arise?
There are several scenarios where API2:2019 Broken User Authentication vulnerability can arise in web applications. Here are a few examples:
Weak Password Policies: If a web application allows users to choose weak passwords or doesn’t enforce password complexity requirements, attackers can easily guess or crack the password and gain access to the application.
Session Hijacking: If a web application doesn’t use secure session management techniques, attackers can steal user session tokens or cookies to impersonate legitimate users and access sensitive data or functionality.
Insecure Communications: If a web application doesn’t use HTTPS to encrypt user credentials or other sensitive data, attackers can intercept and steal this information.
Broken Access Controls: If a web application doesn’t implement proper access controls, such as role-based or attribute-based access, attackers can bypass the authentication and authorization mechanisms to gain access to sensitive data or functionality.
Password Reuse: If a user reuses the same password across multiple websites or applications, an attacker who gains access to one site can use the same password to access other sites.
What Could be the Impact of a BUA Exploit?
A BUA (Broken User Authentication) exploit can have significant consequences for the security of a web application and the data it stores. If an attacker successfully exploits a BUA vulnerability, they can gain unauthorized access to sensitive data, perform actions on behalf of legitimate users, or take over user accounts. Here are some examples of potential impacts:
Data Theft: An attacker can steal sensitive data such as personal information, credit card details, passwords, or trade secrets by exploiting BUA vulnerabilities. This data can then be used for identity theft, fraud, or corporate espionage.
Account Takeover: An attacker can use BUA vulnerabilities to gain access to legitimate user accounts, allowing them to perform actions on behalf of the user, such as transferring funds, placing orders, or sending messages. This can lead to financial losses, reputational damage, or legal liability.
Service Disruption: An attacker can use BUA vulnerabilities to disrupt the normal functioning of a web application by blocking legitimate users from accessing the application, modifying or deleting data, or injecting malicious code. This can result in operational disruption, reputational damage, and loss of revenue.
Regulatory Compliance: BUA vulnerabilities can also lead to non-compliance with regulatory requirements such as GDPR, HIPAA, or PCI DSS, leading to regulatory penalties, fines, or legal action.
Overall, the impact of a BUA exploit can be significant, leading to financial losses, reputational damage, and legal liability for the organization that owns the web application.
An Example of How API2:2019 Broken User Authentication Vulnerability Can be Exploited
Here is an example of how an API2:2019 BUA vulnerability could be exploited:
Suppose a web application uses a RESTful API to authenticate and authorize user requests. The application requires users to provide a valid username and password to access their account information in the API request body.
However, the application fails to implement proper rate-limiting or throttling mechanisms, allowing an attacker to launch a brute-force attack against the API.
Here’s an example of how an attacker might exploit this vulnerability using Python code:
import requests
# This is the target user's API endpoint
url = 'https://example.com/api/user'
# This is the list of possible usernames and passwords
usernames = ['admin', 'user', 'test']
passwords = ['password1', 'password2', 'password3']
# This is the attacker's loop to try all combinations of usernames and passwords
for username in usernames:
for password in passwords:
# This is the attacker's request, using the current username and password
response = requests.post(url, json={'username': username, 'password': password})
# This is the attacker's check for a successful login
if response.status_code == 200:
print('Success! Username:', username, 'Password:', password)
break
In this example, the attacker is using the requests library in Python to send POST requests to the target user’s API endpoint with different combinations of usernames and passwords.
The attacker uses a loop to try all possible combinations without proper rate limiting or throttling. Once the attacker successfully guesses the correct username and password, they can access the target user’s account information.
A practical example: The Parler Data Scrape
Parler, a social network in the US, faced a massive data scraping attack in 2022. This massive breach led to 70TB of its users’ profile data, messages, posts (including deleted posts), and videos being leaked. This happened because the social network’s platform only had partial authentication, per analysis. There was a minimum of one endpoint that didn’t have any form of authentication.
Why so? These API endpoints were probably not meant to be public-facing APIs as they allowed direct access to user profile information and content. Parler may not have intentionally configured these pages to be accessible without authentication. But this broken user authentication flaw had a catastrophic impact on their business.
To prevent such vulnerabilities, employing robust API security tools is essential. Our blog compares the best API security software, detailing their features, benefits, and limitations.
How Does One Test for Broken User Authentication Vulnerability?
Penetration testing is the most comprehensive way to unearth BUA vulnerabilities. Leverage the Infinite API Scanner to get comprehensive results with a bundle of automated scanning and pen testing. Here are the most common use cases to test for:
Identify the API endpoints that require user authentication: Review the API documentation to identify the endpoints that require user authentication. These endpoints may allow users to access or modify sensitive data, such as account information or payment details.
Test the authentication mechanism: Test the authentication mechanism by attempting to access the authenticated endpoints with valid and invalid credentials. Verify that the API returns an appropriate response, such as an error message or a 401 Unauthorized status code, when invalid credentials are provided.
Test the authorization mechanism: Verify that users are authorized to access only the resources they can access. Test this by attempting to access resources that are not authorized for the authenticated user. Verify that the API returns an appropriate response, such as a 403 Forbidden status code, when the user is not authorized to access the resource.
Test for session management flaws: Test for session management flaws by logging in as a user, then attempting to access the same endpoints with a different user’s credentials. Verify that the API returns an appropriate response, such as a 401 Unauthorized status code, when the user attempts to access endpoints with a different user’s credentials.
Test for rate limiting and throttling: Test for rate limiting and throttling by attempting to launch a brute force attack against the authentication endpoint. Verify that the API limits the number of authentication attempts from a single IP address, and returns an appropriate response, such as a 429 Too Many Requests status code, when the rate limit is exceeded.
Test for other authentication vulnerabilities: Test for other authentication vulnerabilities, such as weak passwords, password reuse, or credential stuffing attacks.
Overall, testing for API2:2019 BUA vulnerabilities involves verifying that the API implements proper authentication and authorization controls and protecting against session management flaws, brute force attacks, and other vulnerabilities that can lead to broken user authentication.
How to Find API2:2019 Broken User Authentication Vulnerability Through Automation?
The process of testing for API2:2019 Broken User Authentication (BUA) vulnerabilities can be automated using various tools and techniques. Here are some examples:
Automated scanning tools: Security testing tools such as the Infinite API Scanner can be used to perform automated scans of web applications and APIs to identify potential BUA vulnerabilities. These tools can identify common issues, such as weak passwords, session fixation, or cookie vulnerabilities, and report any findings to the tester.
API testing frameworks: Automated API testing frameworks such as Postman or SoapUI can be used to test the API endpoints for BUA vulnerabilities. These tools can simulate requests to the API endpoints with different user credentials, test for rate limiting and throttling, and verify that the API responds appropriately to invalid requests.
Custom scripts: The Infinite API scanner allows pluggable custom scripts to test the API endpoints for BUA vulnerabilities. These script plug-ins can automate testing of the authentication and authorization mechanisms, verify that the API is not vulnerable to common attacks such as brute force or credential stuffing, and generate reports of any vulnerabilities identified.
Continuous integration and delivery (CI/CD) pipelines: BUA vulnerability testing can be integrated into the CI/CD pipeline for the API. Automated tests can be run during the build process to ensure that new code changes do not introduce BUA vulnerabilities. It also identifies any existing vulnerabilities that may have been introduced in previous API versions.
Overall, automating the testing process for API2:2019 BUA vulnerabilities can help to identify vulnerabilities more quickly and efficiently and enable developers to address these issues before attackers exploit them.
How does AppTrana WAAP Protect Against BUA Exploits?
The AppTrana WAAP bundles an API security solution to protect APIs against a number of attacks, including API2:2019 Broken User Authentication (BUA) exploits. The API Protection solution implements various security measures to ensure that user authentication is implemented securely in the API. Here are some ways that AppTrana can protect against BUA exploits:
Session management: A WAAP can protect against session fixation, session hijacking, and session replay attacks by implementing secure session management mechanisms such as session timeouts, secure cookie management, and secure token management.
Rate limiting and throttling: A WAAP can protect against brute force attacks and other automated attacks by implementing rate limiting and throttling mechanisms to limit the number of requests from a single IP address or user.
Vulnerability management: A WAAP can identify and prioritize vulnerabilities using automated tools and techniques such as vulnerability scanning, threat intelligence, and machine learning. This can help quickly identify and remediate any discovered BUA vulnerabilities.
API security policies: AppTrana can help you implement positive security policies specific to the protected API. This ensures that the API is only accessible by authorized users and that data is protected against unauthorized access or modification.
Overall, the AppTrana solution can help protect against API2:2019 BUA exploits by implementing a range of security controls and mechanisms designed to prevent unauthorized access to sensitive data, protect against automated attacks, and ensure that the API is implemented securely.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 March 15, 2023
March 15, 2023






