How to Choose the Best Website Penetration Testing Tool?
What makes a good website penetration testing tool? Speed, agility, efficiency, or cost benefits? How about all of them?
Hackers use automated tools to scan websites and apps before manually trying to exploit security loopholes. As the first step towards securing assets, you should do the same – only with better resources and before them.
We’ve already talked about penetration testing, and this post covers some valuable suggestions on selecting and optimizing the pen testing tool for your business.
What is Penetration Testing Software?
Pen-testing software is typically used as part of penetration testing to automate certain tasks to enhance testing efficiency and uncover vulnerabilities. Some software is commercial, while others are open source.
Some of the pen testing tools are used to replicate the attacks that threat actors do. In contrast, others are bundled with stronger features to examine security vulnerabilities without disturbing production environments and prioritize remediation action.
Penetration testing is quite a complex and sophisticated task. It could take hours or even days if it all needs to be completed by hand. Thus, the requirement for automated penetration testing software arises to carry out certain tests efficiently and quickly.
Security teams of most organizations are turning to cloud-based pen-testing tools to advance their in-house security programs via strategic automation.
Types of Tools Used in Successful Penetration Testing
The pen-testing software can be broken into the following categories:
- Port Scanners – Port scanners occur in the first pen-testing phase. This tool lets you detect all open network entry points on a given system.
- Vulnerability Scanner – An automatic tool to assess systems, applications, or networks for known vulnerabilities. This tool can take part in a standalone assessment or a continuous complete security monitoring approach.
- Application Scanner – This tool examines the security weaknesses that reside in web applications. The web application scanner scans apps against cookie manipulations, memory buffer overruns, SQL injections, XSS, and more.
- Web Application Assessment Proxy – This tool sits between the targeted web server and the web browser of the pen-tester to closely examine all the data and information flow between the two.
How Powerful is the Penetration Testing Software?
Mirror real-world attacks
The testing tools can simulate the same attacks that the attacker does. Penetration testing tools will test your security mechanisms the same way a real-world hacker might do by using techniques and exploits utilized by the actual attacker to check whether you’ve placed adequate security measures.
Validate which vulnerabilities pose an actual risk
Pen-testing software finds vulnerabilities and validates whether those vulnerabilities pose a severe threat, saving you more time and resources. Automated testing tools attempt to exploit discovered vulnerabilities with real-time attack scenarios, proving whether the weakness is exploitable.
Save more time through automation
You can successfully automate lots of pen-testing tasks without losing effectiveness. These tools come up with robust automation capabilities. The more steps you automate, the more your security team focuses on core tasks that require their attention. Buying paid automated penetration testing software against a free or open-source tool is a key benefit. Automation is where you will obtain the greatest efficiency and cost savings.
Improves results with robust dashboard and reporting
The dashboard of automated penetration testing tools offers a quick overview of the result. It displays a graphical summary of the discovered weaknesses, scan activity, and a list of the latest scans. Further, the vendors strive hard to make the report section of the tool as user-friendly and human readable as possible.
Most tools’ report starts with a visual summary of the result. Indusface WAS, for example, includes the findings section and details about discovered vulnerabilities like description, risk score, and recommendations for addressing them.
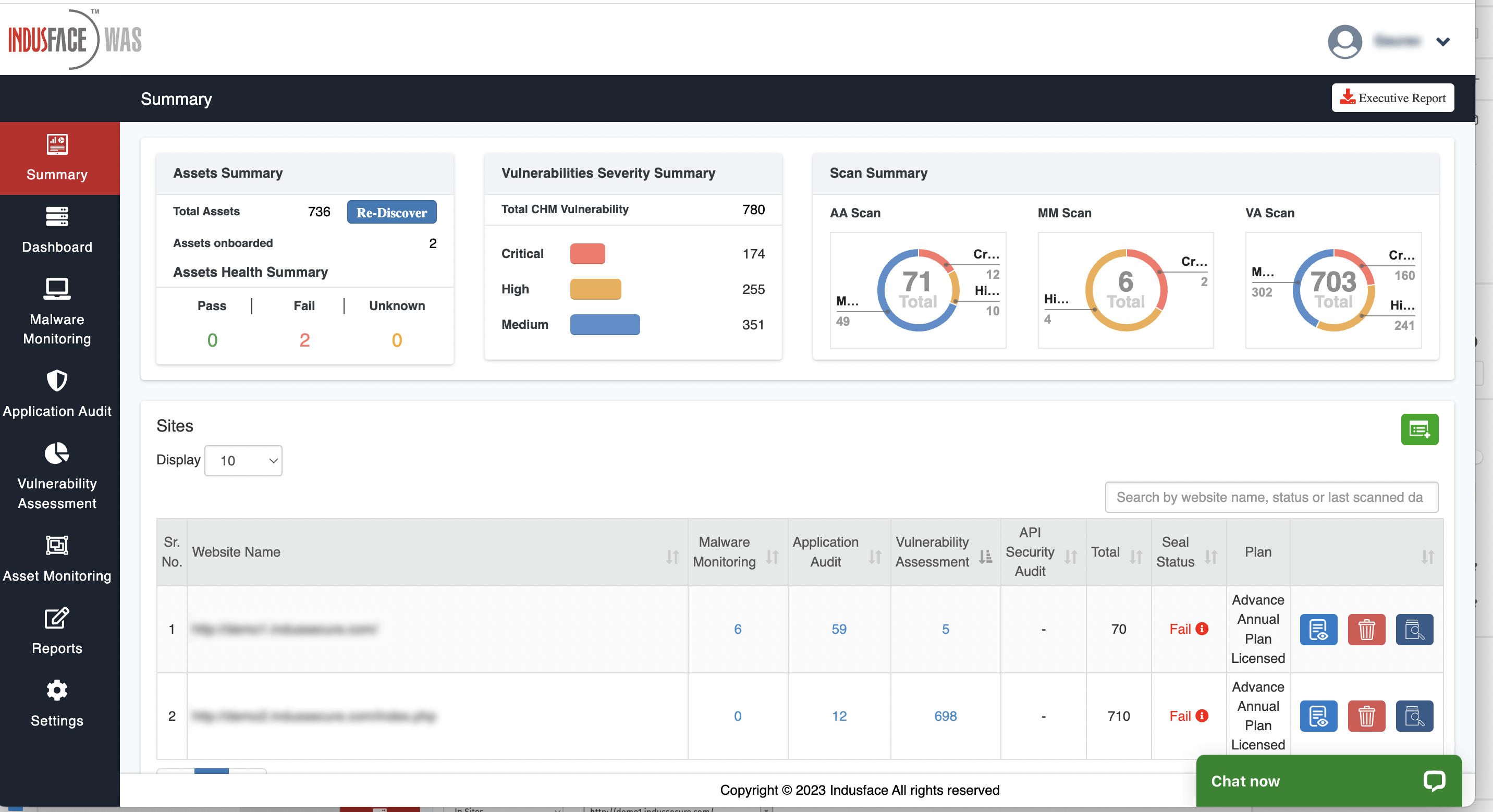
Prove compliance with Industry regulations
Several mandated security compliance regulations exist in each industry, and many regulations like PCI DSS, OWASP Top 10, and SAN 25 require frequent pen testing. Automated testing tools perform unlimited scanning to ensure complete coverage against that compliance.
Continuous security monitoring
You can schedule the scanner to test your system for security weaknesses periodically. Scans can be scheduled when your system changes or updates. Since these tools are regularly updated with the details of emerging threats, you won’t miss any critical vulnerabilities. As a result, you can quickly react when new vulnerabilities are identified.
How to Find the Best Website Penetration Testing Tools?
Look for more than just automated testing
A dozen would appear as you search for tools to test a website. Believe us when we say that most are not thorough penetration testing instruments.
Pen testing is more than just running a scanner to look for predefined problems with the website or an application. Yes, it is a part of the process, but it requires a critical understanding of how hackers think and react, which only a human tester can provide.
Before you pay for a tool or even test it, ensure it is not just a bot.
Application logic mapping is critical
Smart hackers understand that most successful online businesses have already covered the OWASP Top 10 vulnerabilities. They thus analyze the business logic behind the application and try to exploit loopholes that a typical bot or an inexperienced tester would overlook.
Let’s consider a scenario where an e-commerce site offers a promotion where customers who make three separate purchases within a month receive a 20% discount on their fourth purchase. This promotion is designed to reward loyal customers.
However, there is a business logic flaw in the system. Smart hackers could exploit this by making three separate purchases and returning the items, effectively resetting their purchase count to zero. This allows them to continuously receive the 20% discount on their fourth purchase, even though they are not genuinely loyal customers.
This example illustrates how a business logic flaw can be used to take advantage of a promotion or incentive in an e-commerce site, potentially leading to financial losses for the business. It’s a vulnerability that may not be covered in the standard OWASP Top 10 list but can significantly impact the business.
The process is incomplete and inefficient if you are pen testing for a predefined list of 10-20 vulnerabilities.
Follow risk-based methodology
Selecting a penetration testing tool is not just about the tool itself but also the methodology used by the testers. A risk-based method is crucial for comprehensive testing.
Some penetration testers may solely focus on using their tools and predefined tests. However, the real threats to your business often lie in specific areas, the so-called “low-hanging fruit” that attackers exploit first.
You want penetration testers who understand your business objectives and tailor their approach to target your highest-risk areas.
Malware coverage
Google and other search engines are serious about infected websites. They are quick to blacklist any web resource that can harm users. Often, website penetration testing tools do not cover infected code. Check with the vendor if their penetration testing service covers malware detection.
Ask for a testing plan
Security vendors that understand the risks diligently convey the testing phases, exact dates, and follow-up procedures of the tests. Testing involves documentation of credentials, and descriptions of web assets. As you can see, it’s a process- not something you can request today and get the report by tomorrow morning.
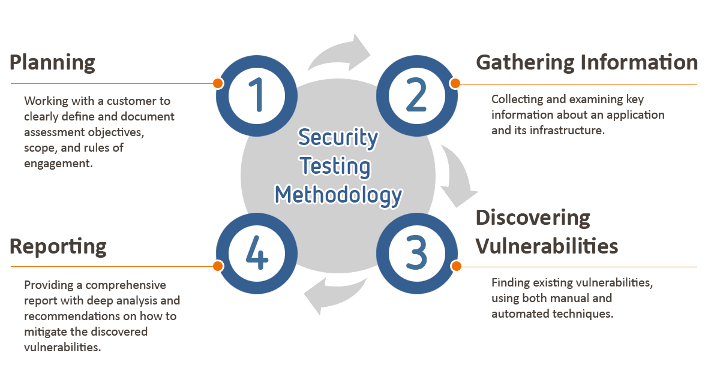
Vendors that do not follow a proper pen testing methodology are often inexperienced and unlikely to deliver thorough reports.
Look at the reporting module
Reporting is everything. What’s the use of a report that doesn’t convey information efficiently? While a security vendor might have a brilliant testing team, it all boils down to how they put it together for you to act upon.
Here are a few things to look for in penetration testing sample reports:
- Defined reports
- Consistency in reporting vulnerabilities
- Understandable
- No signs of data manipulation/ unbiased
- Tester’s advice/observation/notes
- Decision-making value
Indusface WAS offers dashboards with graphical representations of the data. There are even options to download/export reports.
Here are some essential pen-testing reporting options in Indusface WAS:
- A provision to separate the pen-test report from the entire report in one click
- A dedicated section that helps you find and keep track of all the historical pen test results
- Gathering the re-validation data in no time
- Zero dependency on external teams during the audits and compliances to gather the pen test details
- A historical graph that showcases a pen test summary
Here is a quick walkthrough of penetration testing reporting in Indusface WAS:
See if you’re getting severity insights
Regarding reports, security admins would unconditionally want the severity security metric. This offers a quick view of what resources are open to attacks and the risks the business faces in its current state.
The risk severity of each vulnerability will help you prioritize remediation action.
Ask for remediation support
Any company would agree that an assessment is the first step towards securing your business. Your website penetration testing tool report likely contains a list of vulnerabilities that need to be fixed according to priority.
Top penetration testing tools guide how to get rid of the reported security issues.
Check for WAF compatibility
Protection would be the second if vulnerability detection is the first step in web security. A web application firewall means instant protection.
Over the years, several surveys have shown that fixing vulnerabilities is tedious.
Our recent state of application security report revealed that of 46,000 critical and high vulnerabilities identified across 1,400 websites, approximately 31%, which amounts to 14,794, have remained unaddressed for over 180 days.
Traffic routed through a WAF is secure from common hacking attempts. Furthermore, suppose your penetration testing tool is synchronized with a WAF. In that case, you can virtually patch vulnerabilities and obtain instant protection, even with a shortage of resources to manage security risks.
Keeping the websites and your online business safe is a continuous process. A loaded, full-featured penetration testing tool is your foundation for:
- Finding vulnerabilities before attackers
- Ensuring all critical issues are resolved
- Monitoring risks
Ease of implementation
One of the critical factors to consider when selecting a website penetration testing tool is its ease of implementation. A tool that is straightforward to set up and use will save you time and resources.
Complex and convoluted installation processes can hinder your ability to conduct thorough penetration tests efficiently. The right tool should come with clear and user-friendly instructions, allowing your team to start quickly. This user-friendliness can significantly impact your testing process, making it more efficient and effective.
Support and False Positive Monitoring
While the tools are essential, their support and post-testing monitoring are equally crucial. Look for penetration testing tools that provide reliable support services. A dedicated support team can help troubleshoot issues, answer questions, and assist you in making use of the most of the tool’s features.
Additionally, consider tools that excel in false positive monitoring. False positives can be common during penetration testing, leading to unnecessary alarm and confusion. A tool that can effectively distinguish between true vulnerabilities and false alarms is invaluable in ensuring the accuracy of your assessments.
Manual or Automated Pen -Testing?
Penetration testing tools are not meant to replace human expertise; they are valuable extensions for penetration testers. These tools enable testers to streamline routine testing tasks, freeing up their intellectual capacity to focus on creative and out-of-the-box thinking. Successful penetration testing is not about choosing between pen testers and automated software but selecting the right tools to empower your team.
Indusface Web Application Scanning (WAS) offers continuous monitoring, detection, and cataloging of web applications. It conducts thorough and precise scans to unveil real-time vulnerabilities, configuration errors, data exposures, and malware within modern web applications. WAS provides enhanced visibility and control by identifying known, “shadow,” and overlooked applications across your environment.
To further enhance security, WAS complements the automated checks with manual penetration testing conducted by experienced security professionals. The manual testing phase includes providing proof of concepts for each identified vulnerability, ensuring that your testing process attains precision that leads to zero false positives.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 October 20, 2023
October 20, 2023




