46 Ways to Stop Ecommerce Security Threats
Any online business can get hacked. Individuals, brands, Fortune 500 companies, startups… hackers don’t discriminate.
Are security threats critical? Absolutely.
It doesn’t matter who you are either. Whether you’re an entrepreneur just starting out, an IT manager, an established business owner, a CIO, a director of security, a CTO, or something in between, you have to be concerned about the digital security of your company. It’s paramount in 2017.
You need only look at the number of high-profile hacks and data leaks to understand why. If you believe you’re “too small” for hackers to bother with, think again.
The Osterman Research’s security survey 2016 reports that:
- 71% of SMBs experienced a security breach in the previous 12 months. That number was 75% for companies with fewer than 500 employees.
- Phishing (43%), virus or worm infection (36%), and ransomware (23%) were the three most successful forms of attack.
Most telling of all, though, is that fewer than 50% of respondents believe they can successfully defend against an advanced attack.
Small, medium, or large businesses…we’re all at risk without proper protection. So what is at stake? Everything that matters: your reputation, your revenue, and your growth.
Just under two-thirds of consumers (64%) said it’d be unlikely they’d do business with a company that suffered a financial data breach, while nearly half (49%) said the same about a business where personal details were stolen.
Tighten up those leaks – people want an ironclad fortress before they hand over their confidential information. Can you provide them that?
“If you spend more on coffee than on IT security, you will be hacked. What’s more, you deserve to be hacked.” – Richard Clarke, former Special Advisor to the President on Cybersecurity
The Must-Have Tools
Lucky for you, the tools are out there to keep you safe from the big (and small) e-commerce security threats. You just need to decide what your most pressing needs are, and then get the right tool to make it disappear.
Free Tool to Test Website Security Online
Online businesses need tools that can scan web applications and provide online reports on vulnerabilities, their nature, and their business impact. AppTrana’s Free Basic Plan is one such tool that you can opt for. It provides bimonthly free security scans, OWASP Top 10 Threat Detection, and SANS Top 25 Vulnerability Detection.
Tools to Protect Against DDoS Attacks

A distributed denial-of-service attack can happen to anyone at any time, and for several different reasons, including holding your website ransom – whether it’s for fun, for revenge against some perceived slight, to disrupt your business, or to shine a spotlight on some cause or belief.
A DDoS attack sends a coordinated amount of high-volume traffic to flood and overwhelm your network and/or application resources. As a result, your legitimate users and customers can’t access it. Everything comes to a screeching halt.
According to research by Arbor Networks, there was an average of 124,000 DDoS events per week in the 18 months prior to July 2016. The top targets for attacks bigger than 10Gbps were the United States, Great Britain, and France. You need to protect yourself.
Indusface’s Web Application Firewall combines application monitoring and human intelligence to defend you against DDoS attacks. It works to prevent attacks while allowing legitimate traffic – your visitors – to pass safely through the net.

Indusface’s Web Application Firewall provides 24/7 testing, monitoring, tuning, reporting… and peace of mind.
All-In-One Platforms

Sometimes, you just want an all-in-one platform to do most – if not all – of the heavy lifting for you.
The HP Touchpoint Manager allows you to monitor and track the security health of all the devices on your Windows network. You can reset passwords, lock devices, deploy security patches, receive alerts, and more, from one convenient dashboard.
Comodo One is a similar IT solution providing remote monitoring and management, remote control and access, security patch deployment, network assessment, analytics, reporting, and more. Best of all? It’s free.
Comodo One offers a quick start guide to get you up and running in no time.
Finally, AppTrana from Indusface is the complete package: web application scanning to identify vulnerabilities, web application firewall to block attacks until patched, and protect against DDoS. It’s an all-in-one solution to help stop threats before they do any damage to you or your business.
Data Loss Prevention Tools

It’s easy for confidential data to slip through your security shields – sometimes intentionally, sometimes by accident. Obviously, you want to prevent it either way.
Enter data loss prevention (DLP) tools. They monitor, detect, and block outbound sensitive data from getting out into the wrong hands.
A few options include:
- MailControl – an anti-spy email solution that prevents email tracking that can help hackers with social engineering and phishing schemes.
- CSID – offers solutions for identity protection, small business monitoring, and data breach mitigation. They have an A+ rating with the Better Business Bureau.
- Endpoint Protector – a cross-platform DLP product for Windows, Mac, and Linux. It was named the top data loss prevention service at the 2016 Cybersecurity Excellence Awards.
Keep your sensitive data safe where it belongs… behind the security of your network or computer.
“Companies spend millions of dollars on firewalls, encryption, and secure access devices, and it’s money wasted because none of these measures address the weakest link in the security chain.” – Kevin Mitnick, computer security consultant and former hacker
And just what is the weakest link in your security chain? People. Your employees. Your customers. You.
Everyone needs tools to keep them and their devices safe while online.
Online Protection and Anti-virus Tools

It’s no secret that the e-commerce web is full of some nasty, scary things: viruses, trojan horses, and other malicious scripts meant to disable, take over, or steal. If you or your employees spend any time online, you need a digital suit of armor.
These service providers consistently rank at or near the top of consumer reviews:
- Symantec Endpoint Protection is available for both Windows and Mac, providing online website security for 1-350 users with antivirus, firewall, browsing protection, remote management, behavior monitoring, and intrusion protection. It’s got an average 4-star rating.
- Avast Endpoint Protection Advanced is a Windows-only solution for 1-100 users, including antivirus, remote management, and browsing protection. It’s got an average 4.4-star rating.
- Sophos Endpoint Protection for Windows and Mac includes the standard antivirus, browsing protection, device control, application control, data control (DLP), and remote management. It’s got an average 3.8-star rating.
- ESET offers security solutions for Mac and Windows and either small, medium, large, or enterprise-level businesses. No matter your size, they’ve got a product for you. It’s got an average 4.2-star rating.
Secure Browsing Tools

Beyond defending yourself from viruses and other vicious scripts, you need to safeguard the information you and your customers transmit across the expanse of cyberspace. Leave it uncovered, and someone can snatch it between Point A and Point B.
Protect the transmission of sensitive financial and other confidential data by having all employees use the HTTPS Everywhere browser extension for Chrome, Firefox, and Opera, or SSL Always for Safari. They force an encrypted connection between the browser and the website whenever possible using the SSL protocol.
Get an SSL Certificate for your website security and other online properties – it encrypts the connection and authenticates site identity (it’s the reassuring green padlock you may have noticed while surfing online). Customers want to see that before they hand over any personal details.
Good suppliers for business include Indusface, Comodo, Symantec, RapidSSL, and Thawte.
Last but not least, consider a virtual private network (VPN) for all online activity, but especially for employees on the road or working remotely, that may be using public wifi signals.
A VPN creates a virtual tunnel between a computer and a destination on the internet. The data sent between them is shielded from prying eyes, and it’s encrypted within that tunnel just in case someone tries to breach it for a closer look.
Great business options include VyprVPN for Business, SaferVPN, and NordVPN. Check out other reviews to find the perfect solution for your unique circumstances.
Oh, and a quick reminder to turn on automatic updates for the latest patches and improvements to your OS and apps. An up-to-date system is the strongest system.
Encryption Tools

Of course, browsing online is not the only activity that might leave your data vulnerable. We send billions of emails, instant messages, and texts every day. Most of us never stop to consider whether they’re secure. The harsh reality? They’re not.
Unless you take steps to shelter them.
Protect your files, emails, messages, and voice/video calls with unhackable end-to-end encryption solutions:
Encryption for text messages and telephone calls
Try Silent Circle (hardware and software solutions for secure communication, and the winner of a Frost & Sullivan New Product Innovation award in 2015), Signal by Open Whisper Systems (encrypted calls and texts for both iOS and Android, and recommended by Edward Snowden!), or even the ubiquitous Whatsapp (although it does offer end-to-end encryption, it’s not as strong a solution as the others).
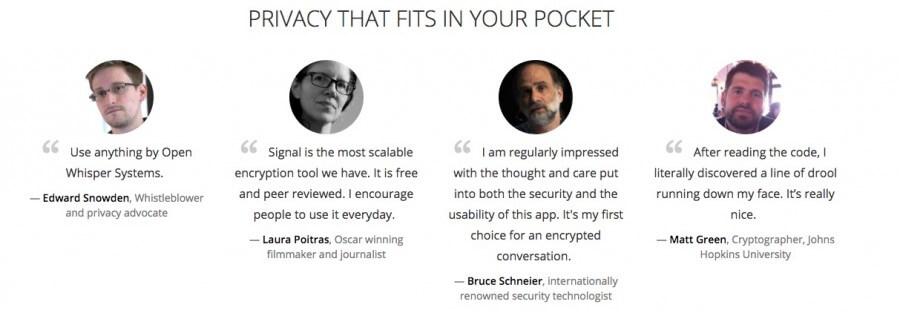
Encryption for email
Look at the following options for encryption for email:
- ProtonMail (end-to-end encryption, anonymous registration, open-source, and a solid 4.7-star rating on the Google Play Store)
- HPE SecureMail (a Cybersecurity Excellence Award winner for email security in 2016)
- Sendinc (military-grade encryption and compliance)
- Proofpoint (heavy-duty encryption, incoming and outgoing protection, and data loss prevention protocols).
Encryption for files and drives
No discussion on encryption would be complete without talking about tools for your files and drives used in the e-commerce infra.
An encrypted hard drive, for example, keeps everything under lock and key should your computer be lost, stolen, or hacked. FileVault for Mac and Bitlocker for Windows are the industry standards (and already included with the operating system).
A third-party solution like VeraCrypt is cross-platform and good for individual files, folders, or entire volumes.
On the mobile front, the iPhone is encrypted by default, while an Android phone can be encrypted under ‘Settings > Lock screen and security’.
But what about the cloud? More and more businesses are using it as a convenient, scalable, and affordable storage solution for their documents and files, but those benefits do come with increased risk.
While major providers like Dropbox, Google Drive, and Box are encrypted, it’s not impossible or even unprecedented that someone could gain access. That’s where a tool like CipherCloud comes in. A Cybersecurity Excellence Award winner for encryption and a finalist for cloud security in 2016, it’s a powerful service that works with virtually every major cloud provider out there to make you safe, secure, and compliant in the cloud.
Data Backup and Ransomware Tools

Ransomware attacks are on the rise and are increasingly common. Victims paid out $24 million in the U.S. in 2015 alone. Ransomware is malicious software that takes control of a computer or network and blocks access to it until a ransom is paid to the perpetrator.
The most common ransomware attacks are via application DDOS, where the hacker threatens to take the application down via app DDOS if the owner doesn’t pay a ransom. Indusface Total Application Security can help protect against this, as it continuously monitors for emerging threats and DDoS attacks.
You can also protect yourself by keeping separate backups of all important files and documents so that you have copies of everything should it happen to you or your company.
Reliable, affordable solutions include Backblaze, Carbonite, CrashPlan, and NovaBACKUP, which is ranked the #1 data backup solution by Top Ten Reviews.

Backing up your files is just smart planning. If you’re targeted by ransomware, you have a recovery plan that doesn’t include paying the hackers.
In order to prevent the ransom in the first place, you could also try a tool like CryptoStopper. It deploys fake decoy files in your system and then monitors them for signs of unauthorized encryption. The moment it detects it, the tool takes action to block the encryption process before it can finish and lock you out.
Backup and monitor. That’s the only way to stay safe.
Passwords and Account Access Tools

Your security is only as good as the passwords that guard the gate. Simple passwords that are used multiple times could eventually cost you. If someone cracks, guesses or finds it, they could end up with access to everything.
“Passwords are like underwear: you don’t let people see it, you should change it very often, and you shouldn’t share it with strangers.” – Chris Pirillo, CEO of LockerGnome
Your best bet is a password manager like 1Password, Dashlane, or LastPass. These services not only keep your passwords safe in one encrypted container, but they’ll automatically log you in without having to remember and enter each individual password. You just have to remember your master password.
Not only that, but each is a sophisticated password generator, too. They can create passwords made up of numbers, letters, and symbols for every website, service, app, and tool you use.
The strongest passwords are unique, random, and long (experts suggest 12-15 characters). Don’t use popular names, phrases, or things people can guess or find on your social media profiles (things like maiden names, your children’s names and birthdates, and so on).
In addition to having strong passwords for everything, you should take it a step further and add two-factor authentication to your accounts and services. With it, you’re required to provide the password and a second item (a PIN, a security token, your fingerprint, your voice, and so on) before access is granted.
Use tools like the Google Authenticator, Authy, Duo, and Yubikey, as well as the online database Two Factor Auth to find sites that use the protocol and make your accounts much more secure.
OneLogin was named best identity management tool at the 2016 Cybersecurity Excellence Awards. It’s a scalable identity and access management platform – for your employees and/or users – that is equally at home with small, medium, or enterprise businesses.
Finally, privileged identity management services like Centrify or CyberArk (both recently named leaders in the field) work to protect, monitor, detect, and respond to threats against the administrator and other privileged accounts.
If those identities are compromised, an attacker can gain full access to files, systems, and documents not available to everyone at a company. Forrester estimates that 80% of security breaches involve privileged credentials.
Other Resources

- Stay Safe Online – learn how to monitor and protect against threats, train employees, report attacks, and more. Powered by the National Cyber Security Alliance.
- FCC’s Cyberplanner – create a custom cybersecurity plan for your business by entering in a few details and areas of concern.
- The Metasploit Framework allows you to test your defenses via penetration testing.
- Wireshark lets you examine your network at a microscopic level. View traffic and activity, and identify problems before they become too serious.
The more you know, right?
“There are certain things all network, IT, and security professionals should have in their tool bag. The most important is knowledge; i.e., where to learn more about a particular topic, technique, or tool. It’s impossible to know everything; so focus on where to get quality instruction and information.” – Ron Woerner, director of CyberSecurity Studies at Bellevue University
Educate yourself and your employees on phishing attacks and how to best avoid them. Remind them to use strong passwords. As the saying goes, an ounce of prevention is worth a pound of cure.
The big guys know they’re targets, and take steps to prevent it. They have the budget, the personnel, and the hindsight of past breaches.
The little guys – the SMBs – often believe they’re safe. They’re wrong. They make even more appealing targets because of that misconception. They often don’t have the budget, personnel, or hindsight to work with, and the hackers know it. In fact, a full 60% of attacks targeted SMBs, according to a recent Verizon study.
Don’t be part of that statistic. The tools and tips here will help to keep you safe from most attacks.
“The only truly secure system is one that is powered off, cast in a block of concrete and sealed in a lead-lined room with armed guards.” – Gene Spafford, professor of computer science and security at Purdue University
Need help securing your business? Indusface is your one-stop-shop for all your security issues. Contact us to find out how we monitor, detect, and protect you from security threats.


 March 21, 2017
March 21, 2017






