3 Ways to Stop Botnet DDoS Tools
What is a cyber attack? If you perceive these attacks to be carried out by an individual hacker trying to work around your server, your top concern should be the ever-growing sophistication of hacking technology. You might be surprised to learn that hackers have dozens of tools at their disposal that can bring your website down in seconds. It’s frightening that cybercriminals use thousands to millions of infected devices and control them remotely to attack websites at a large scale.
[no_toc]
- Bots were responsible for 90% of the attacks in 2017 [Indusface Yearly Report]
- 1 in 3 Website Visitors is a bot [CSO Online]
- Bad botnet attack 96% of websites with login pages [Help Security Magazine]
What are Botnets?
A botnet is a collection of internet-connected devices that are corrupted or hijacked to carry out malicious activities. Any device can become infected by visiting a malicious site, and it automatically downloads malware without you even noticing.
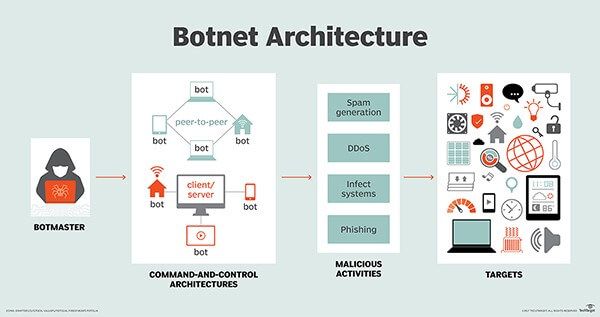
Hackers often send a large number of emails to target systems. These types of phishing schemes can sometimes be hard to detect, even with alerts and tech-savvy users. Unfortunately, once the malware is on the device, it can unpack a virus and take over the device.
Lately, rent-a-bot services, offering services at as low as $5 an hour, have provided hackers with a readily available army to bring down any website or application.
Cybercriminals create bot armies to launch DDoS attacks, spam campaigns, and other types of attacks that can be used to bring your website down and/or steal data. Surprisingly, these types of attacks are easy to carry out too, with botnet armies available on a rental basis. Full-service attacks are available for as little as $5 per hour, and the interested party can easily stretch their hour with a monthly plan that averages $38.
You can explore the ways to identify bots, here.
How Bad Botnets Affect Your Business?
Keeping a business application up and running is critical to your brand’s reputation, and hackers want to target this weakness with DDoS attacks. The unpredictability of these attacks makes it difficult to prepare for them, which further incentivizes criminals to act. The following are some examples of bad bots disrupting major businesses in recent times.
- DDoS attacks cost banks up to $100, 000 per hour
- 20% of such attacks last for days and even months
- 87% of the attacked companies were hit more than once
- Over one week in December 2015, cybercriminals made over 5 million login attempts at a Fortune 100 B2C website using multiple attack groups and hundreds of thousands of proxies located throughout the world
- Over two days in January 2016, a large retailer saw two major Sentry MBA attacks with over 20,000 total login attempts
- During one day in January 2016, a large retailer witnessed over 10,000 login attempts using Sentry MBA and over 1,000 proxies
With the rapid rise of the Internet of Things, botnets and zombie armies are only going to increase. Irrespective of your business size, it is imperative to adopt a technology that can distinguish between good and bad bots while stopping malicious threats.
How to Stop Bad Botnet?
Businesses simply cannot deploy a separate tool for each threat. Many CSOs have mentioned that over the last three years, their organizations have purchased too many tools and are now looking to consolidate these solutions. One VP of Security from a large software company mentioned that she has 87 people in her organization, yet they have 89 tools to manage. According to her, this was untenable. Here are some of the ways that you can manage bot menaces along with your existing application-layer threats.
- Detect and Analyse Anomalies: Log the web application firewall data for cybersecurity teams to analyze and learn from new attack patterns and technologies. Once machine learning and AI learn what to look for, they can quickly give their human counterparts the information they require to mitigate the attacks and fallout.
- Block Bots Instantly: Detecting and addressing advanced, complex bot attacks take Thousands of pieces of ever-changing data and anomalies to need to be quickly analyzed in order to find potential incidents. Train your web application firewall (from recent attacks) to flag suspicious traffic and block it if required.
- Consolidated Layer 7 Protection: A more efficient cybersecurity process can help reduce costs and help streamline the process. Artificial intelligence and machine learning can rapidly and efficiently detect threats, resolve them, and prevent them in the shortest amount of time possible with the greatest potential for resolution. A 360-degree protection solution such as AppTrana can detect, protect, and monitor all your application layer threats, including botnets.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 January 16, 2018
January 16, 2018



