Are CISOs Becoming the Soft Target?
The CISOs are trying their level best to cope with the rising and unique nature of cyber threats. In the present times, each and every CISO conscious of their organization’s security, is taking appropriate security measures against top threats like XSS, DDoS, CSRF, SQL injection and investing on DLP solutions or for Web Applications, in a WAF with custom rules (masks credit card numbers, SIN numbers) with targeted policies to prevent sensitive data exposure of clients. Despite this, whenever any organization becomes the victim of a cyber-attack, that too due to the customer’s negligence, the CISOs have to face the heat.
Recently a security firm found a unique attack on ‘online banking’ apps. This attack could have taken place only due to the absolute ignorance on the part of the customers about any cyber norms. Can citing the attack a result of customer error, help the CISOs in washing their hands off the responsibility of keeping their organization secure? No!
Unwillingly, they have to become part of the ‘blame game’, which in turn chokes the bandwidth of their job responsibilities.
Banks across the world have adopted a ‘Two Factor Authentication System’. Two-factor authentication is a security process in which the user provides two means of identification, one of which is typically a physical token, such as a card, and the other of which is typically something memorized, such as a security code. While most sites ask for a single password, two-factor authentication systems require customers to enter a second, one-time password that has been emailed or texted to their phones. The hope is that a second identifying factor eliminates the risk that criminals can break into customers’ accounts simply by stealing an online password.
The researchers have uncovered, what they say is a sophisticated, multistage attack by cybercriminals determined to bypass the so-called two-factor authentication systems.
The attack starts with a phishing email:
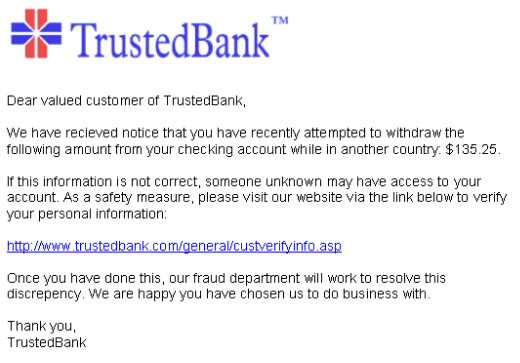
The email, which appears to come from popular retailers/ banks etc. includes malicious attachments disguised as receipts. By opening the attachments, victims download malicious software onto their machines. In turn, when someone tries to reach a real bank site, that software redirects the victim to a site managed by criminals.
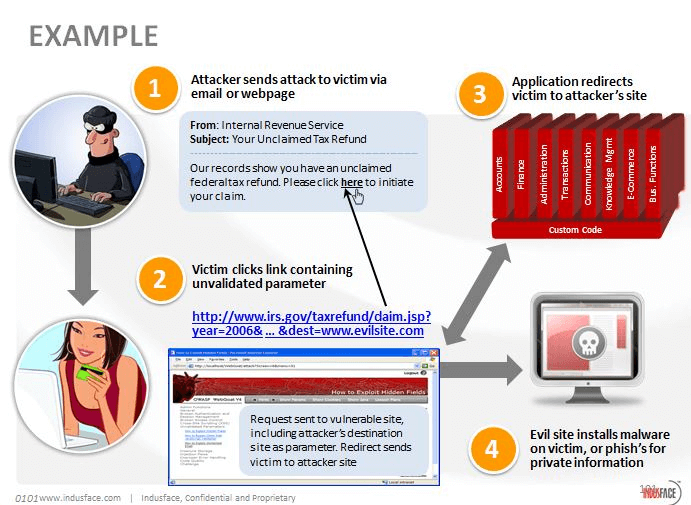
The attackers then sends that password to their own command and control server. Thereafter, combined with the victim’s stolen online banking credentials, the hackers pilfer their victims’ accounts.
When the security firm published their article, they received a lucid review by a reader:
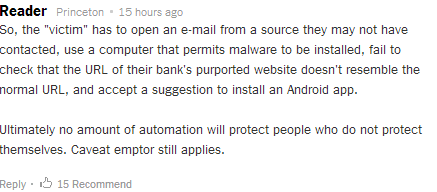
We, the security researchers at Indusface totally agree with the statement ‘No amount of automation initiatives by CISOs can protect people unless they are made aware of the current threat trends.’
The least that the CISO can do is to ensure that their own properties and apps which are in their control do not become segways for launching an attack and they need to first focus on what they can control (implementing two-factor authentication, having a strong vulnerability detection and protection program) and post that tie it up with customer education. The first part is more important and the second part, despite the reasoning that no matter what is done they cannot control it fully, can at the least minimize the brand damage. (For example: A customer is compromised as they have shared their password indiscriminately- there is no way a bank can do anything about that)
While focus needs to be there on securing the organization’s IT infrastructure, the organizations also need to be proactive in building customer awareness on plausible online threats and need to educate them via regular mails, brochures, phone and even direct contacts, if required.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 July 25, 2014
July 25, 2014



