The Cost of Cybercrimes for Businesses
With the rise of the great Indian cyber empires across sectors like BFSI, IT, E-commerce, and Telecom & Communication, crooks have devised even more sophisticated ways to exploit vulnerabilities that prove to be a lethal hole in the defense.
Indian businesses simply cannot afford to compromise on cybersecurity for a number of reasons, but huge cash inflow underlined by massive growth potential attracts exploitation attempts from all across the world, and sadly there are certain sectors that are attacked more often and more brutally than others.
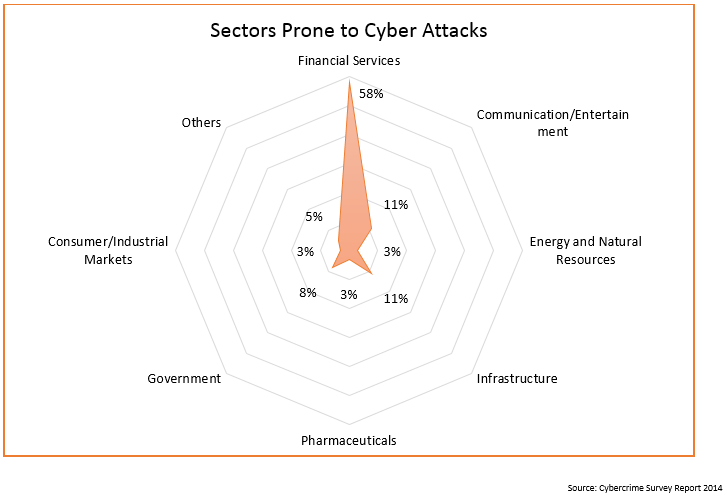
Before we move on to the insights on why these business sectors are more prone to attacks, it is important to understand why exploitation is bad for the business in the first place. Following are the top seven reasons that make CIOs and CISOs fear exploitations.
- Reputation Damage
- Disruption of Business Process
- Financial Loss
- Intellectual Property Theft
- Disclosure of Privacy-Related Information
- Dropped Employee Morale
- Others
Reputation damage and disruption of business are, in fact, the biggest concerns, which directly and indirectly lead to major financial losses. And then, of course, no one can potentially calculate the loss of face for the brands.
They are after the money, but there’s more.
Today, almost every organization is extensively involved in information technology for carrying out normal business processes. From payment to communication, almost everything revolves around internet-powered technology, which also makes them prone to attacks.
If you look at the motives of these attacks, illegal financial gains top the list followed by unsolicited malicious damage, defacement, and business or a foreign rivalry. Quite clearly, business sectors like banking, finance, and insurance are always on the radar for financial gains, but eCommerce isn’t far behind given the momentum it has picked in our booming economy.
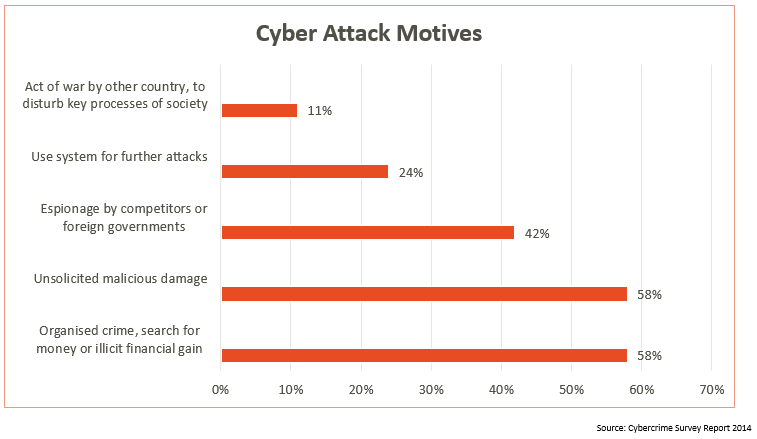
Although a lot of financial and e-commerce companies have adopted internal and network layer security measures, application security is often overlooked. Many websites in India are still prone to basic OWASP Top 10 Vulnerabilities including SQL Injection and Cross-Site Scripting (XSS). Often amateur measures like a secret cookie and only accepting POST requests fail to secure applications.
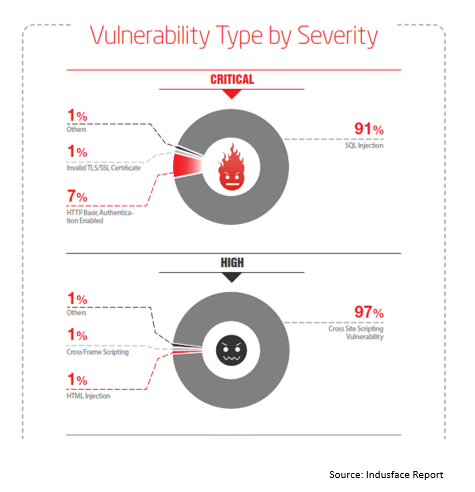
Other than the usual input injection risks and payment system vulnerabilities, business websites also attract threats with substandard mobile applications across Android, iOS, Windows, and Blackberry platforms.
Attacks have evolved, so should the security measures.
Statistics show that India is the second most targeted cybercrime country in the world after the United States. This shouldn’t come as a surprise given the growing number of internet users in our country and the giant leaps we are taking in information technology.
However, even after being one of the hottest locations for cyber exploitation, we are largely unaware, and unfortunately underprepared.
Indian companies rely overly on antivirus software, traditional firewalls, and intrusion prevention systems when the risks are far greater at the application layer. Information technology research giant Gartner has repeatedly emphasized how 75% of the attacks take place on the application layer and how network firewalls along with intrusion prevention systems fail to provide key elements like web attack signatures, web vulnerability signatures, and automatic policy learning.
We need to realize that the international security outlook is evolving with the associated risks. Businesses, today, rely heavily on web applications that power everything from electronic payment to online carts around a plethora of technologies such as C/C++, Java, .NET, Python, PHP, Ruby, Perl, and more. Often these applications are coded for multiple and frequent changes, bringing forth new risks and exploitation potentials.
That is why CIOs and CISOs in India need to reconsider their security perspective and should focus on a more holistic approach built around total application security that comprises of the vulnerability detection system to scan and report threats with 24/7 continuous monitoring, along with WAF that can defend from exploitations by virtually patching vulnerabilities at the application layer.

 February 19, 2015
February 19, 2015






