CVE-2024-4577 – A PHP CGI Argument Injection Vulnerability in Windows Servers
On June 7, 2024, a new critical PHP vulnerability CVE-2024-4577 was revealed, mainly impacting XAMPP on Windows. It happens when PHP runs in CGI mode with specific language settings, like Chinese or Japanese.
The problem comes from how PHP handles certain characters, allowing attackers to inject code through web requests and take control of servers.
This vulnerability, if exploited, could lead to the execution of arbitrary code, a scenario with severe consequences for system integrity and data security.
Insights and Analysis – CVE-2024-4577
CVE-2024-4577 signifies a CGI argument injection vulnerability within PHP, capable of compromising Windows-based servers running PHP.
Risk Analysis
Severity: Critical
CVSSv3.x: Base Score: 9.8 Critical
Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CVSSv2: Base Score: 7.5 High
Vector: CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P
Exploit available in public: Yes
Exploit complexity: Low
The vulnerability impacts:
- PHP 8.3 versions earlier than 8.3.8
- PHP 8.2 versions earlier than 8.2.20
- PHP 8.1 versions earlier than 8.1.29
These versions, if left unpatched, remain susceptible to exploitation, leaving servers vulnerable to unauthorized access and potential data breaches.
The vulnerability traces its roots to errors in character encoding conversions, particularly within the “Best Fit” feature on Windows systems. This oversight provides attackers with a loophole to bypass existing security measures, notably those designed to thwart CVE-2012-1823, a predecessor vulnerability.
Active Exploitation
Hackers try to exploit the vulnerability within a day of its disclosure. The availability of proof-of-concept (PoC) attack code and active scans online underscores the urgency to apply immediate patches.
Attackers are exploiting CVE-2024–4577 in different ways with two primary attack scenarios emerging:
- CGI Mode Exploitation:
This vulnerability can be directly exploited when configuring the Action directive in Apache HTTP Server to map HTTP requests to a PHP-CGI executable binary.
- XAMPP Vulnerability:
The default configuration of XAMPP, a widely used PHP development environment, is susceptible to exploitation. Even if PHP is not configured in CGI mode, simply exposing the PHP executable binary in the CGI directory makes it vulnerable.
Common examples include copying php.exe or php-cgi.exe to the /cgi-bin/ directory.
Mitigation Strategies
Mitigating CVE-2024-4577 requires a multi-faceted approach, involving proactive measures and timely patching. Key mitigation strategies include:
-
- Immediate Patching: System admins should quickly update PHP installations to the patched versions (8.3.8, 8.2.20, and 8.1.29) provided by the PHP Group.
- Disabling CGI Features: In vulnerable environments like XAMPP, disabling PHP CGI features mitigates the risk of exploitation.
- Modifying Server Configurations: Employing mod_rewrite rules can enhance server defenses against potential exploits, augmenting existing security measures.
- Rewrite Rules: For users who cannot upgrade PHP can use these Rewrite Rules to block attacks temporarily.
RewriteEngine On
RewriteCond %{QUERY_STRING} ^%ad [NC]
RewriteRule .? - [F,L]
AppTrana WAAP Coverage for CVE-2024-4577
AppTrana WAAP ensures that our customers are shielded from the risks associated with CVE-2024-4577 and similar vulnerabilities from Day 0.
In addition to relying on patches from the software vendor, the Indusface managed security team has developed rules specifically designed to swiftly detect injection vulnerabilities in PHP and prevent exploitation attempts.
| Rule ID | Name |
| 124 | PHP Injection Attacks Policy |
| 99876 | PHP Injection Attacks Policy |
WAAP effectively blocks potential attacks by issuing a robust 406-status code:
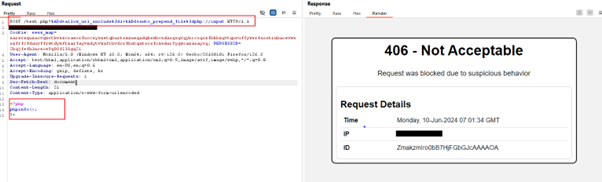
AppTrana WAAP has a proven track record of safeguarding organizations from cyber-attacks by addressing both zero-day exploits and known vulnerabilities at the earliest stages.
Leveraging the expertise of our managed service team, along with built-in DAST Scanner and autonomous patching capabilities, AppTrana WAAP ensures that our customers remain protected from both new and existing exploits.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 June 10, 2024
June 10, 2024




