CVE-2024-4879 & CVE-2024-5217 Exposed – The Risks of RCE in ServiceNow
Recent critical vulnerabilities in ServiceNow, a widely used cloud platform, have put numerous organizations at risk of data breaches. Threat actors are exploiting these input validation flaws, enabling remote code execution and unauthorized access.
Despite recent fixes, government agencies, data centers, and private firms remain targeted.
This blog highlights how these flaws are exploited for data theft and outlines security measures to mitigate these risks.
ServiceNow Vulnerabilities – Overview
ServiceNow addressed several critical vulnerabilities on July 10, 2024, including CVE-2024-4879 and CVE-2024-5217, both of which are input validation flaws that allow remote code execution (RCE). A less severe flaw, CVE-2024-5178, was also addressed.
Despite the release of security updates by the vendor on July 10, 2024, many systems remain vulnerable to attacks.
CVE-2024-4879: Jelly Template Injection Vulnerability
This critical vulnerability affects the Vancouver and Washington DC versions of ServiceNow. It involves a jelly template injection flaw that allows unauthenticated remote attackers to execute arbitrary code within the platform. The issue arises from improper input validation, leading to severe security risks.
Risk Analysis
Severity: Critical
CVSSv4.0 : Base Score: 9.3 CRITICAL
Vector: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N
CVSSv3.1: Base Score: 9.8 CRITICAL
Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: Yes.
Exploit complexity: Low
| Release | Fixed Version |
| Utah | Utah Patch 10 Hot Fix 3 Utah Patch 10a Hot Fix 2 |
| Vancouver | Vancouver Patch 6 Hot Fix 2 Vancouver Patch 7 Hot Fix 3b Vancouver Patch 8 Hot Fix 4 Vancouver Patch 9 Vancouver Patch 10 |
| Washington | Washington DC Patch 1 Hot Fix 2b Washington DC Patch 2 Hot Fix 2 Washington DC Patch 3 Hot Fix 1 Washington DC Patch 4 |
CVE-2024-5217: Incomplete Input Validation in GlideExpression Script
This critical vulnerability is present in the Vancouver and Washington DC versions of ServiceNow. It is caused by incomplete input validation in the GlideExpression script, allowing unauthenticated remote code execution.
Risk Analysis
Severity: Critical
CVSSv4.0 : Base Score: 9.2 Critical
Vector: CVSS:4.0/AV:N/AC:L/AT:P/PR:N/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N
CVSSv3.1: Base Score: 9.8 Critical
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: Yes.
Exploit complexity: Low
| Release | Fixed Version |
| Utah | Utah Patch 10 Hot Fix 3 Utah Patch 10a Hot Fix 2 Utah Patch 10b Hot Fix 1 |
| Vancouver | Vancouver Patch 6 Hot Fix 2 Vancouver Patch 7 Hot Fix 3b Vancouver Patch 8 Hot Fix 4 Vancouver Patch 9 Hot Fix 1 Vancouver Patch 10 |
| Washington | Washington DC Patch 1 Hot Fix 3b Washington DC Patch 2 Hot Fix 2 Washington DC Patch 3 Hot Fix 2 Washington DC Patch 4 Washington DC Patch 5 |
CVE-2024-5178: Incomplete Input Validation in SecurelyAccess API
This medium-severity vulnerability impacts the Washington DC, Vancouver, and Utah versions of ServiceNow. It involves incomplete input validation in the SecurelyAccess API, which can lead to unauthorized access to sensitive files by administrative users.
Risk Analysis
Severity: Medium
CVSSv4.0 : Base Score: 6.9 Medium
Vector: CVSS:4.0/AV:N/AC:L/AT:N/PR:H/UI:N/VC:H/VI:N/VA:N/SC:N/SI:N/SA:N
CVSSv3.1: Base Score: 4.9 Medium
Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N
Exploit available in public: Yes.
Exploit complexity: Low
| Release | Fixed Version |
| Utah | Utah Patch 10 Hot Fix 3 Utah Patch 10a Hot Fix 2 Utah Patch 10b Hot Fix 1 |
| Vancouver | Vancouver Patch 6 Hot Fix 2 Vancouver Patch 7 Hot Fix 3b Vancouver Patch 8 Hot Fix 4 Vancouver Patch 9 Hot Fix 1 Vancouver Patch 10 |
| Washington | Washington DC Patch 1 Hot Fix 3b Washington DC Patch 2 Hot Fix 2 Washington DC Patch 3 Hot Fix 2 Washington DC Patch 4 |
Exploitation Details
Attackers are actively exploiting critical vulnerabilities in ServiceNow to infiltrate systems and steal data. The process begins with reconnaissance, where attackers use tools like FOFA and Shodan to identify vulnerable ServiceNow instances.
They then employ automated tools to inject payloads into exposed endpoints, testing for RCE by exploiting flaws such as CVE-2024-4879 and CVE-2024-5217. Upon confirming a vulnerability, attackers execute arbitrary code to establish control, often by opening a reverse shell.
They chain multiple vulnerabilities together, such as CVE-2024-4879 with CVE-2024-5217 and CVE-2024-5178, to gain full database access and bypass security mechanisms. With database access, attackers enumerate users and extract sensitive information, including hashed and plaintext credentials, which are then exfiltrated.
To maintain access, attackers deploy backdoors and modify configurations, ensuring continued control over the compromised system.
Mitigation Steps
To protect against these vulnerabilities, organizations should:
- Apply the Latest Patches and Hotfixes: Ensure all instances are updated with the security patches provided by ServiceNow.
- Monitor Systems for Unusual Activity: Set up monitoring for suspicious activity related to these vulnerabilities.
- Use Multi-Factor Authentication: Enhance security by implementing multi-factor authentication.
- Regularly Review and Update Security Protocols: Ensure robust protection against emerging threats by keeping security protocols up to date.
AppTrana WAAP Coverage for ServiceNow Flaws
AppTrana WAAP customers receive built-in protection against these critical vulnerabilities.
- SQL Injection Protection: Safeguards database integrity and prevents unauthorized data access.
- Cross-site Scripting (XSS) Protection: Prevents unauthorized code execution and data leakage.
These rules are designed to provide comprehensive security and help prevent potential exploitation of ServiceNow vulnerabilities.
Example Use case
The screenshots show how AppTrana WAAP effectively blocks this vulnerability. WAAP promptly responds to malicious requests intercepted by Burp with a strong 406-status code.
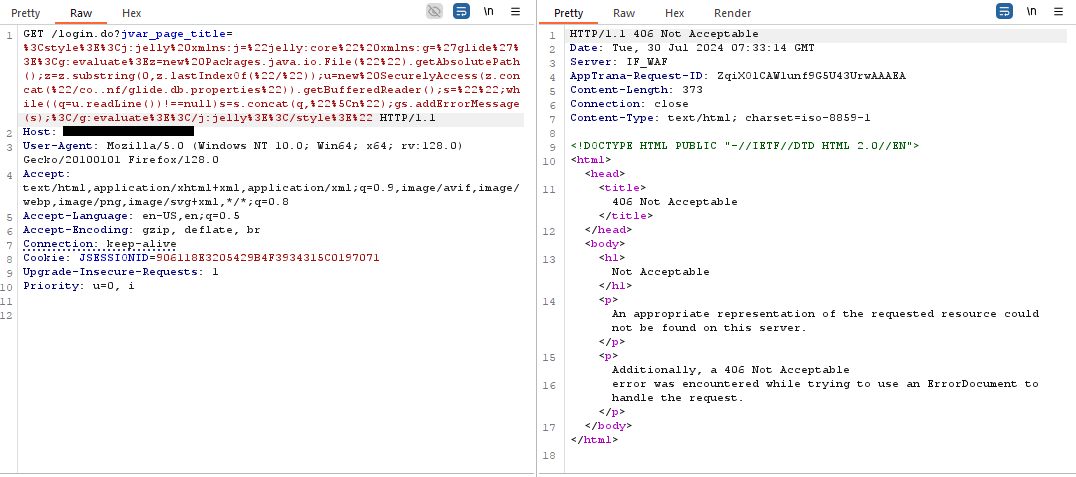
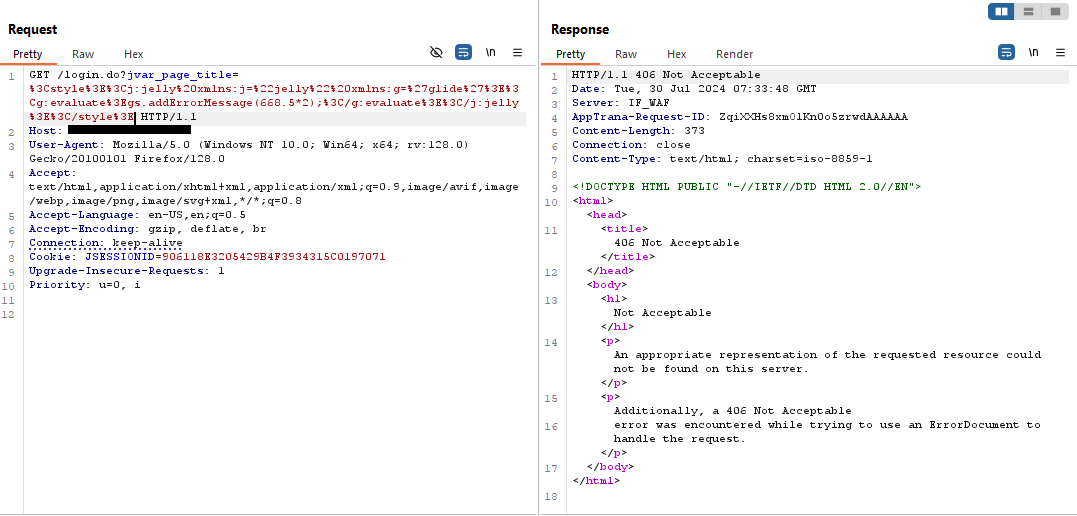
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 August 1, 2024
August 1, 2024




