CVE-2024-8517 – Unauthenticated Remote Code Execution in SPIP
A critical security flaw has been discovered in SPIP, a popular open-source content management system (CMS). This flaw, identified as CVE-2024-8517, stems from a command injection issue in the BigUp plugin. The vulnerability allows attackers to execute arbitrary OS commands remotely and without authentication, simply by sending a malicious multipart file upload HTTP request.
This blog will explore the details of this vulnerability, its potential impacts, and the essential steps for mitigation.
CVE-2024-8517 – SPIP BigUp Plugin – RCE
Risk Analysis
Severity: High
CVSSv3.1: Base Score:9.8 Critical
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: No
Exploit complexity: Low
CVE-2024-8517 arises from improper handling of user inputs in the lister_fichiers_par_champs function. This function fails to adequately sanitize data from file uploads, particularly when the bigup_retrouver_fichiers parameter is set to 1. As a result, attackers can craft malicious HTTP requests containing harmful PHP code, which, when processed, executes arbitrary commands on the server.
The vulnerability affects all versions of SPIP before 4.3.2, 4.2.16, and 4.1.18.
One of the most alarming aspects of this vulnerability is its unauthenticated nature. Attackers do not need any special privileges or access to exploit it; they can perform the attack by simply sending a specially crafted HTTP request to the affected SPIP server which increases more chances of exploitation.
Impact
The vulnerability allows remote code execution, potentially leading to:
- Unauthorized Access to Sensitive Data: Attackers could gain access to confidential information stored on the server.
- Modification or Deletion of Critical Files: The integrity of critical system files could be compromised.
- Installation of Malware: Attackers may install malicious software or backdoors on the server.
- Lateral Movement: The compromised system could serve as a foothold for further attacks within the network.
- System as a Launching Point: The server could be used as a base for additional attacks targeting other systems.
While it has not yet been observed in the wild, the publication of a proof-of-concept (PoC) exploit increases the likelihood of it being used in real-world attacks.
Mitigation Strategies
To mitigate the risks associated with CVE-2024-8517, it is crucial to update to the latest patched versions: 4.3.2 or later for the 4.3.x branch, 4.2.16 or later for the 4.2.x branch, and 4.1.18 or later for the 4.1.x branch.
Also consider implementing the following additional mitigations:
- Restrict Access: Limit the file upload functionality to trusted users only.
- Enhance Input Validation: Apply strict input validation and sanitization for all file uploads.
- Monitor Logs: Regularly check system logs for any unusual activity related to file uploads or command execution.
- Conduct a Security Audit: Perform a thorough security audit of affected systems to ensure no compromise has occurred.
- Strengthen Security Practices: Review and enhance overall security measures, especially those related to file uploads and command execution prevention.
- Deploy a WAF: Utilize a Web Application Firewall (WAF) to filter potentially malicious requests.
AppTrana Coverage on RCE Vulnerabilities
With AppTrana WAAP, our customers are shielded from RCE exploits, including CVE-2024–8417, right from Day 0.
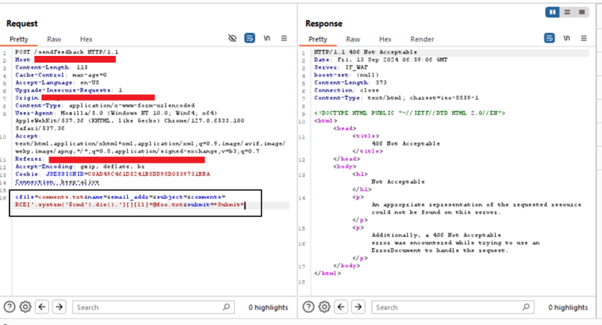
The screenshots illustrate AppTrana WAAP’s capability to effectively block this vulnerability. When malicious requests are intercepted by Burp, WAAP responds promptly with a firm 406-status code.
1)name= “HELLO[AB’.system(‘id’).die().’CD]”
![CVE-2024-8517 - AppTrana WAAP Coverage - command injection PoC using the payload HELLO[AB'.system('id').die().'CD]](https://www.indusface.com/wp-content/uploads/2024/09/CVE-2024-8517-AppTrana-WAAP-Coverage-PoC-1.png)
2) name=”RCE’-system(‘id’)-‘[ABCD]”
![command injection PoC using the payload ) name="RCE'-system('id')-'[ABCD]"](https://www.indusface.com/wp-content/uploads/2024/09/CVE-2024-8517-AppTrana-WAAP-Coverage-PoC-2.png)
3) name=”RCE’-sprintf(system(‘id’),die())-‘[ABCD]”
![command injection PoC using the payload name="RCE'-sprintf(system('id'),die())-'[ABCD]"](https://www.indusface.com/wp-content/uploads/2024/09/CVE-2024-8517-AppTrana-WAAP-Coverage-PoC-3.png)
4) name:RCE[‘.system(‘$cmd’).die().’][][ll]=@foo.txt
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 September 13, 2024
September 13, 2024






