CVE-2024-9264 – Grafana’s SQL Expressions Vulnerability
A critical vulnerability, CVE-2024-9264, has been discovered in Grafana, the open-source analytics and visualization platform widely used by organizations worldwide.
According to Netlas.io, over 100,000 Grafana instances may be vulnerable globally, with nearly 19,000 in the U.S. alone.
This vulnerability poses significant risks, enabling remote code execution (RCE), allowing attackers to execute arbitrary system commands and access sensitive files.
CVE-2024-9264 – Risk Analysis
Severity: Critical
CVSSv4.0 : Base Score: 9.4 Critical
Vector: CVSS:4.0/AV:N/AC:L/AT:N/PR:L/UI:N/VC:H/VI:H/VA:H/SC:H/SI:H/SA:H
CVSSv3.1: Base Score: 8.8 High
Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: High
CVE-2024-9264 is a command injection (CI) and local file inclusion (LFI) vulnerability identified in Grafana versions 11.0.x, 11.1.x, and 11.2.x. It allows attackers with Viewer permissions or higher to exploit SQL Expressions, a feature designed for post-processing query outputs.
The flaw arises from improper input sanitization when handling SQL queries sent to DuckDB via the Grafana API. With this, malicious actors can escape the intended SQL context, execute arbitrary commands, and even access restricted files.
How Does the Exploit Work?
For an attacker to successfully exploit CVE-2024-9264, the following conditions must be met:
- DuckDB binary installed: The DuckDB binary must be installed manually and added to Grafana’s PATH.
- User permissions: The attacker must have at least Viewer permissions to the Grafana instance.
- API access: The attacker can access the SQL Expressions feature via Grafana’s API, which was mistakenly enabled by default.
By crafting a malicious SQL query and leveraging the API, attackers can:
- Execute commands on the host system (Command Injection).
- Access files outside of intended directories (Local File Inclusion).
This vulnerability poses a threat to system confidentiality, integrity, and availability, enabling attackers to:
- Access sensitive data
- Manipulate data or system configurations
- Cause service disruptions
Mitigation and Prevention
To safeguard against CVE-2024-9264, consider these steps:
- Upgrade Grafana: Immediately update to patched versions:
- 11.0.5, 11.1.6, or 11.2.1 (security fix only).
- 11.0.6, 11.1.7, or 11.2.2 (security fix + features).
- Restrict Permissions: Minimize the number of users with Viewer or higher permissions to reduce potential exposure.
- Audit PATH: Ensure the DuckDB binary is not in Grafana’s PATH unless explicitly required for secure operations.
- Use a Web Application Firewall (WAF): Deploy a WAF to monitor and block suspicious SQL commands and other unusual activities in network traffic.
Discover how WAFs prevent SQL injections—read our blog on Preventing SQL Injection Attacks.
AppTrana WAAP Protection
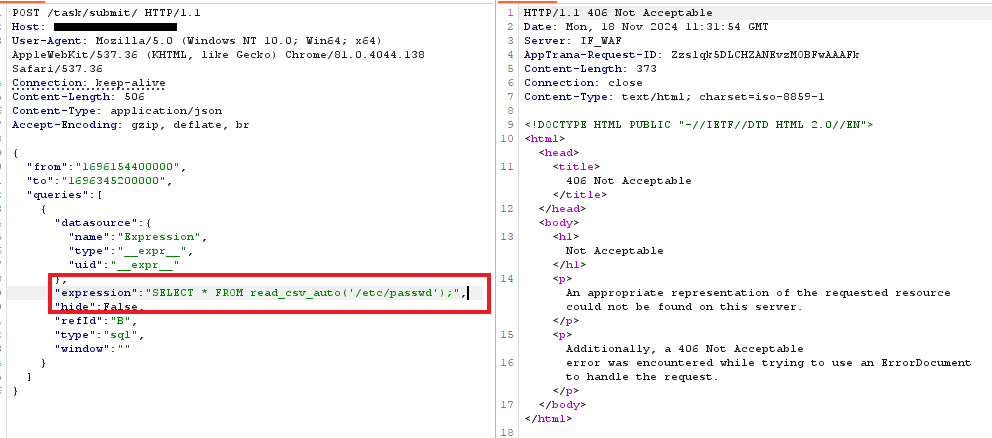
With AppTrana WAAP’s out-of-the-box coverage, our customers have been protected against this CVE from the day 0.
During PoC simulations for CVE-2024-8190, AppTrana WAAP effectively blocked the malicious request, as illustrated in the screenshots.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 November 19, 2024
November 19, 2024






