DDoS Attack Mitigation – Don’t Compromise on Security for Speed
The current era of business is not dependent on the traditional working style. DDoS attacks are more prevalent and outrages in networks and websites are getting prominent. The result is right in front of us – Many breaches and attacks are reported. A DDoS attack can also be carried out with the intent of slowing down a site, and not necessarily bringing it down
A recent study has also highlighted a stark fact – at least 25% of online users tend to leave a website if it takes more than 4 seconds to load the webpage. This not only increases the bounce rate; the consequences turn out to be more severe due to lost uptime and performance.
A discovery from Amazon highlighted that the extra loading time (100 milliseconds) damaged their sales by 1%. The percentage may seem small to us, but for them, the amount could be millions.
Interesting Stats On DDoS Attacks
Issues related to cybersecurity are becoming daily struggles for business. Here are some of the interesting statistics regarding DDoS attacks and managed DDoS protection.
- At least 20% of DDoS attacks has risen and impacted websites by 200%
- In 2019, the reported DDoS attacks with 2+ attack vectors reached 82%, affecting multiple websites adversely
- As per a recent security survey, the average and estimated cost of a single DDoS attack ranges between $20,000 and $40,000 per hour
- Another survey highlighted that 32% of serious DDoS attacks occurred due to network intrusion
- By 2022, the anticipated DDoS attacks would double to be $14.5 million
Get URI-Based DDoS Protection for your Applications
What is DDoS Mitigation?
When a targeted network or a server is successfully protected from DDoS (Distributed Denial-of-Service) attack, it is referred to as DDoS mitigation or DDoS attack mitigation.
What are the signs that your website is under a DDoS attack?
There are a few symptoms that might indicate that your website is under a DDoS attack. Some of the most common signs are:
- Your website starts responding slow
- Visitors face the ‘website unresponsive’ page very often
- Your website is unavailable for the users very often
A lot of website owners find it a little difficult to understand if their website is under attack.
How businesses should Mitigate DDoS Attacks?
There are basically 4 stages of managed DDoS protection, which can be mitigated using a trustworthy cloud-based provider.
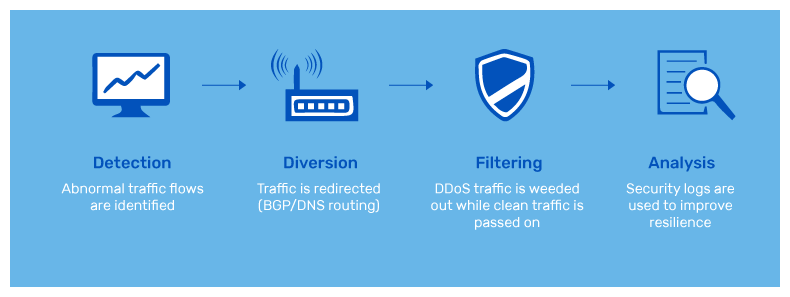
1. Detection
As the name suggests, this 1st step of DDoS attack mitigation is to prevent a distributed attack. To do so, your website is required to identify an inconspicuous attack from traffic ranging from normal to high volume.
Suppose, you have released a new product or service whose description is explained well on your website. Now, with that announcement, your website is swamped with authentic visitors (both existing and new). When things are so well, you would never want your website to be under attack that could prevent the visitors to stop seeing the content or leave your website dejected.
A few of the common things that this stage does is:
- Protect your IP reputation
- Take help of your previous data and use it for proper security measures
- Identify common attack patterns
2. Response
This is the second stage of mitigation involving the responses from the DDoS attack mitigation network. This is a smart way to hurl back incoming identified threats via the means of dropping malicious bot traffic. This again absorbs the remaining traffic.
A classic example is the use of WAF page rules. It is mainly done for handling the infiltration or attacks on lower levels, like L4 or L3 NTP amplification or Memcached with the help of the application layer (L7).
3. Routing
As per the Routing DDoS attack mitigation solution, you can smartly route the traffic and break it into chunks. This not only makes the process manageable but also prevents DoS (denial of service).
4. Adaption
This is a fact that most businesses will agree with. If you work within a good network, it constantly evaluates the traffic to look for attack patterns like:
- Improper use of specific protocols
- Attacks emerging from specific countries
- Repeating offending IP blocks
Business challenges with respect to maintaining the security
Since DDoS and other types of vulnerability attacks have become increasingly common, there is a huge requirement for businesses to have a security system that is trained to not compromise on projection for speed. This can be challenging for businesses to incorporate as both of the parameters are very important.
Choosing DDoS attack mitigation involves buying equipment that would be constantly live on the website and continue to filter the incoming traffic and absorbing the attacks as an added protection. However, what is more, important is to implement the systems and equipment in a systematic way.
Here are a few tips:

- Zero Trust policies
Zero trust policy has been adopted by a lot of major global organizations and has been successful. It is a great way to maintain network speed without compromising system security. According to some experts in the industry, most cyberattacks manage to get a privileged entry to the target network.
This implies the fact that network vulnerabilities often take place from systems connected to the home or other friendly networks. Zero trust policy is a great way to lead an uncompromised strategy towards network vulnerabilities. It basically means every outside network (although friendly), device, and the system will be verified before allowing access to the home network.
Zero trust policies are a great way to reduce network vulnerabilities to a bare minimum. However, it has its own share of challenges as scanning friendly networks again and again upon connection request might lengthen the process as well as decrease the reliability factor to some extent.
- Pre-development testing
Though 92% of businesses agree that security testing is important for any new application or product, 39% accept that there is no security involved right at the beginning of the development.
Having security testing on new applications at the end of the development speeds up the entire process but compromises on safety to a great extent. So, modern-day enterprises set the security team to work in tandem with the development team for continuous testing and integration at every step.
The entire process can be a bit tolling and lengthy and organizations should look to automate the entire process. Manual testing can be included but only if automated testing fails to be versatile.
- Increase in latency
It is very important for businesses to work on network latency, that is the ping speed. A lot of organizations focus on network speed for its users while leaving all the data on the cloud vulnerable to attacks. This happens more so because it is difficult to tell the difference between legitimate and illegitimate traffic without making a detailed scan. Having a security check in this section will increase the latency further.
Though most businesses focus on improving service latency, it makes them vulnerable to untested illegitimate traffic. So, just the way a zero-trust security network is strategized for a home network, a security scan to analyze the traffic could go a long way into providing the extra layer of safety against untamed traffic.
However, just like development testing, this testing should be automated and quick as a manual check could increase the latency to a point where there is a loss of legitimate traffic. So, it is important to hit the right balance between the time taken to provide necessary DDoS security scans and the actual security for the data stored in the cloud of the home network.
Qualities of a DDoS Attack Mitigation Solution That Are Secure And Do Not Compromise on Speed

1. Automated
Believe it or not, even if you go for a security solution that inclines mainly on human IT security staff, at one point in time it is bound to succumb. This is because human scrutiny is not as sophisticated or in line with the digitally examining process. Even if the human interface regarding DDoS attack monitoring is tight, they are bound to fail. But with an automated solution, attacks can be identified and absorbed even when the volume is small and the duration is short.
2. ‘Always On’
It is a factual finding that most DDoS attacks are sub-saturating and short attacks. These attacks are more likely to last less than 5 minutes and under a network range of 1 GB/s. These types of minimalistic attacks are prone to evading scrutiny and detection by a majority of homegrown and legacy DDoS mitigation tools.
The configuration of such tools ignores shorter attack activity, thereby creating weaker detection thresholds. Always on mitigation quality minimizes the latency penalties and scans the traffic constantly for potential attacks. As it is not dependent on human awareness, its approach reduces the mitigation time.
3. Provides Visual Results
For any company (including yours and mine), comprehensive security visibility based on network activity is a vital aspect. This is, no doubt, a key to combating serious DDoS threats. However, this quality does not stop here. Managed DDoS protection agrees and complies with the forensic and reporting analysis by utilizing the data of the past DDoS threats.
4. Works in a granular way
When opting for a DDoS attack mitigation solution, select one that can identify and allow good traffic and bar the bad ones with the assistance of closed-loop detecting, granular, blocking filters. The rules of the solution should provide closed-loop and heuristic policies.
It should allow faster creation mode and deployment features so that you can quickly respond to the improvising and evolving, sophisticated nature of the present age DDoS attacks.
Conclusion
It is very important for any organization to strike the right balance between security and speed. A chunk of DDoS security issues crop up only due to extra emphasis on speed, be it traffic or in-house network processes. But then, it is not wise to spend on a compromise on security for speed.
And though there are challenges, working on automating the process will help streamline the security scans to a point where the latency replicates the users’ expectations.


 July 31, 2020
July 31, 2020






