Here’s How You Can Secure Enterprise Mobile Applications
Mobile security not bothering you? You have got to be someone living away from all the application security worries we mere mortals are dealing with or you could be one of those people who think, “This will not happen to me”. Unless you are living off the grid, it most probably will, and soon. A report by the research firm Gartner has mentioned that the majority of the mobile applications will fail basic security tests by 2015. This is bad news especially for the enterprises with BYOD (Bring Your Own Device) on the rise, as employees more often than not, download applications from app stores. These apps have the ability to access all the data on the user’s phone, including the business data, as they offer negligible security assurance, putting the enterprises’ data at significant risk. Gartner says organizations should focus on data protection and application containment solutions to boost mobile security. This is not such a difficult task to attain the correct security solutions in place.
Mobile Applications and Security
Mobiles have now made a world of their own. They have quickly evolved as the new web on the go. An overwhelming amount of activity is being seen on mobiles. Every business wants a piece of this pie and hackers are not far behind. Mobile breaches are increasing and new mobile malware is on the rise, with old malware returning deadlier than before. The cost of these data breaches is running into thousands of dollars, with immeasurable brand damage.
This makes it very important for businesses to give mobile applications security as much, if not more, importance as to web application security.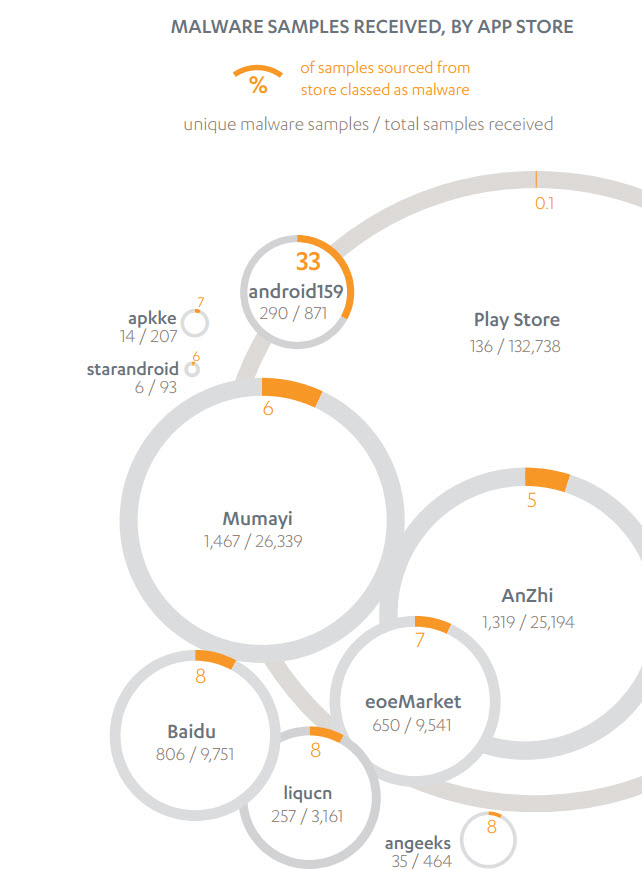
An industry report said that in the second quarter of this year, malware rose 17% to about 4.5 million. Another report disclosed that 97% of mobile apps access user’s private information and out of these, 86% of apps did not have enough security measures to protect from even basic exploits. In a race to get the apps out in the market quickly and to keep the competitive advantage, developers are more often than not sidelining the security factor. As a result, a huge increase in the app which compromises user data has been seen. And in the absence of in-depth pen testing and external audit, the enterprise remains unaware of the basic security status of these apps.
Source: Forbes
What does Gartner say?
Gartner’s research says that in 2015, 75% of mobile applications, in all Mobile OS, will be devoid of basic business-acceptable security protocols in place.
Enterprises will be most affected as this will put sensitive corporate data and networks at risk. The focus will have to be moved from looking for apps that help your employees in facilitating their work, to third-party apps which comply with your organization’s security policies and do not lead to any kind of data leakage.
Dionisio Zumerle, principal research analyst at Gartner commented, “Enterprises that embrace mobile computing and bring your own device (BYOD) strategies are vulnerable to security breaches unless they adopt methods and technologies for mobile application security testing and risk assurance. Most enterprises are inexperienced in mobile application security. Even when application security testing is undertaken, it is often done casually by developers who are mostly concerned with the functionality of applications, not their security.”
“Today, more than 90 percent of enterprises use third-party commercial applications for their mobile BYOD strategies, and this is where current major application security testing efforts should be applied,” noted Zumerle.
“App stores are filled with applications that mostly prove their advertised usefulness. Nevertheless, enterprises and individuals should not use them without paying attention to their security. They should download and use only those applications that have successfully passed security tests conducted by specialized application security testing vendors.”
Gartner has predicted that “75 percent of mobile security breaches will be the result of mobile application misconfigurations, rather than the outcome of deeply technical attacks on mobile devices,” through 2017.
What should enterprises do?
Indusface had conducted in-depth testing of key mobile applications and found that 23% of mobile apps suffered from insecure data storage vulnerability, 17% of mobile apps were suffering from unintended data leakage vulnerability and 10% suffered from weak server-side controls. This shows that enterprise mobile apps are extremely vulnerable to data leaks.
Enterprises need to start focusing on the applications that they allow in their business ecosystem.
- Mobile apps need to be tested for any kind of vulnerability, patched in event of the vulnerability being found, and only then be allowed in their ecosystem.
- Dynamic application security testing (DAST) and audit of mobile applications is the best way to know the risk. Though seeming simple, mobile app security is fairly complex and can be penetrated in multiple ways. Protecting mobile applications is tougher and more complicated than protecting web applications due to their diversity and constantly evolving mobile operating systems.
- Empower your employees with the best security practices and more information on mobile application security. This can prevent data leaks and breaches caused unknowingly by employees and save enterprises a lot of trouble.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 April 2, 2015
April 2, 2015





