2014 Browser Vulnerability Review
Earlier this year, French security firm VUPEN netted a whopping $400, 000 in the HP Tipping Point’s Zero Day Initiative as an annual hacking contest hosted by Pwn2Own. As the name would suggest, the aim for participants was to reveal zero-day vulnerabilities to win outrageous cash rewards.
Here is a breakup of how this popular security firm earned money in the contest.
-
-
-
- Code execution through bypassing IE Sandbox for Adobe Flash = $75, 000
- PDF Sandbox escape and heap overflow for code execution against Adobe Reader= $75, 000
- “A use-after-free causing object confusion in the broker, resulting in Sandbox bypass” to cripple the Internet Explorer= $100, 000
- Code execution in Google Chrome through Webkit and Blink= $100, 000
- Code execution in Firefox using unknown vulnerability= $50,000
-
-
Irrespective of the standard you measure it in; this is huge money, even for a firm of VUPEN’s stature. This contest actually resonates with the security experts’ calls about browser vulnerabilities getting difficult to locate, eating up a large chunk of research resources.
The Basics
An analogical explanation of browsers would be something like a virtual gateway, which helps users make the most out of their internet experience. They help them connect with everything else on the network. Now just like any other chunk of code, browsers are also vulnerable to maliciously written codes that find loopholes in the developer’s architecture.
As a matter of fact, cybercriminals are constantly looking for browser vulnerabilities. In 2014 alone, 653 vulnerabilities were discovered in 5 of the most popular browsers including Mozilla Firefox, Google Chrome, and Microsoft Internet Explorer, while Google Chrome remains the top used browser for 2014.
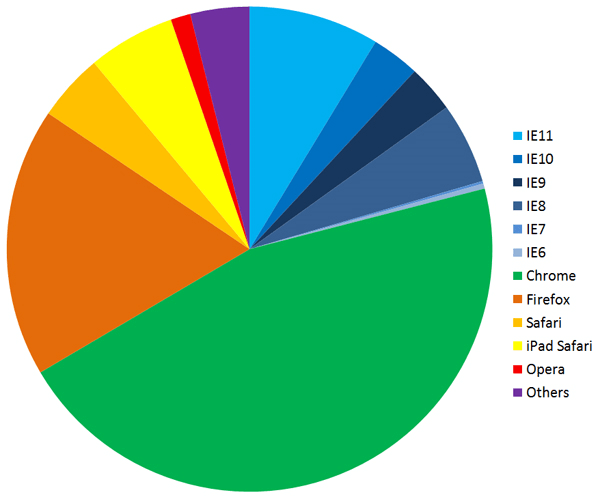
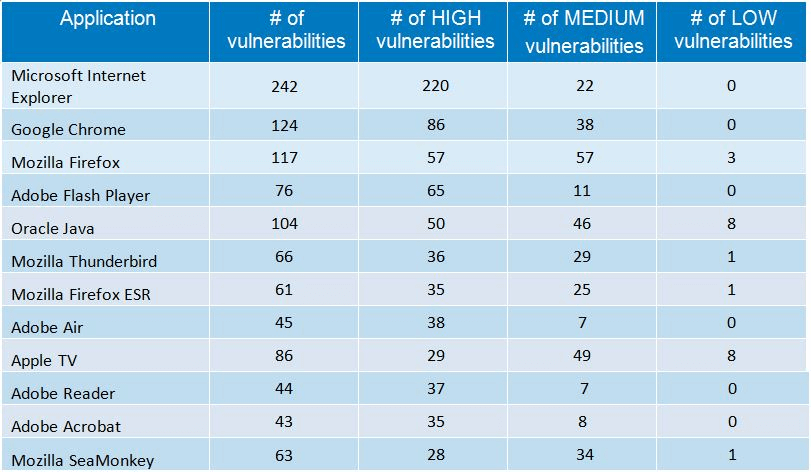
Source: GFI
Although browser developers introduce patches quite frequently, the situation is still troublesome for many organizations around the world.
- 242 vulnerabilities were found in IE as opposed to 124 in Chrome.
- Firefox had 117 flaws in 2014.
- Opera might seem secure, but with a 1% market share it’s possibly not being targeted.
- Google Chrome releases security updates in an average of 15 days.
- This figure is 30 and 28 for IE and Firefox respectively.
- IE still holds a 58.19% market share.
- In a five-year trend, the attacks have increased by roughly 47%.
The Risks
The sophisticated piece of code makes changes to the homepage, favorite pages, and even search pages. Some of them even change internet settings and block certain features or access privileges. Redirection is also common. Applications are usually at higher exploitation risk.
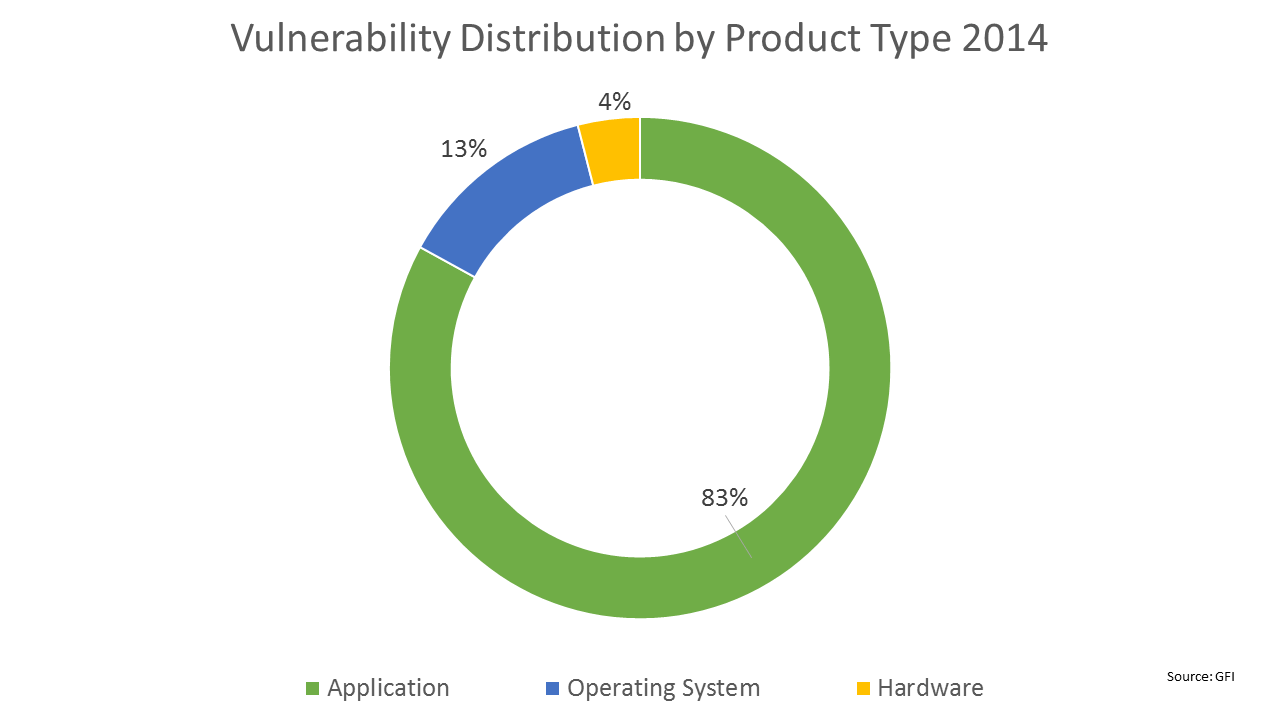
Now given the nature of these symptoms, most people do not really look into the underlying cause and that’s where they get dangerous. POODLE or the Padding Oracle on Downgraded Legacy Encryption has been the worst of all attacks in the past. This particular bug is also known as CVE-2014-3566 and it compromises protocol security level, which can be further used to penetrate SSL or Secured Socket Layer. It is something that most of us blindly trust as security assurance.
Bulletproof Browser
There are a dozen different options freely available to users, but which one of these is absolutely bulletproof against every kind of attack? Well, according to Skybox Security, there is no single answer to that question. Every browser has its own merits and demerits. Picking one is impossible. However, most security experts and users agree that IE has got the most critical security issues and is years behind others.
As for the other browsers, none of them can guarantee safety and that is where awareness comes into play. Following are a few of the tips that help with browser safety.
- A firewall should be an integral part of the system. It protects against several external attacks. Organizations should invest in Web Application Firewall options.
- Keep the software updated with patches, especially the browsers.
- Install plug-ins from reputable sources only.
- Disable Active-X is not required.
- Configure browser security and privacy settings frequently.
- Try security plug-ins.
- Sign-up for news and alerts on the topic.
Organizations vs. Individuals View
For individual users, risks are usually limited to their own data and money, but on the other hand, organizations face huge risks like defacement and data theft through browser vulnerability, which increases the need to countermeasures.
Organizations or website owners should utilize strong security audit programs, both automated and manual for enhanced security. This will ensure their safety even against client browser vulnerability like the JPEG buffer overflow experienced in the past using Internet Explorer. This vulnerability was exploited by crafting a JPEG image with an invalid header to target payload against XSS issues.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 4, 2015
March 4, 2015



