Formjacking Attacks – How They Work and How to Prevent Them
What is Formjacking?
Formjacking is a cyberattack where attackers inject malicious JavaScript code into webpages containing form fields, usually on login pages or payment forms. The objective is to steal sensitive information, such as credit card details, passwords, and other personal data, directly from users as they enter it into the compromised forms.
Formjacking attack occurs entirely on the client side—within the user’s browser—making it particularly challenging to detect. Unlike traditional server-side attacks, where data breaches occur by infiltrating the server, Formjacking capitalizes on the moment the user inputs data, capturing it before it can be securely transmitted to the server.
How Does a Formjacking Attack Work?
Formjacking is an online Man-in-the-Middle (MitM) attack that operates similarly to having your email communications secretly monitored by an unauthorized entity. In the case of Formjacking, the focus is on the data entered into website forms.
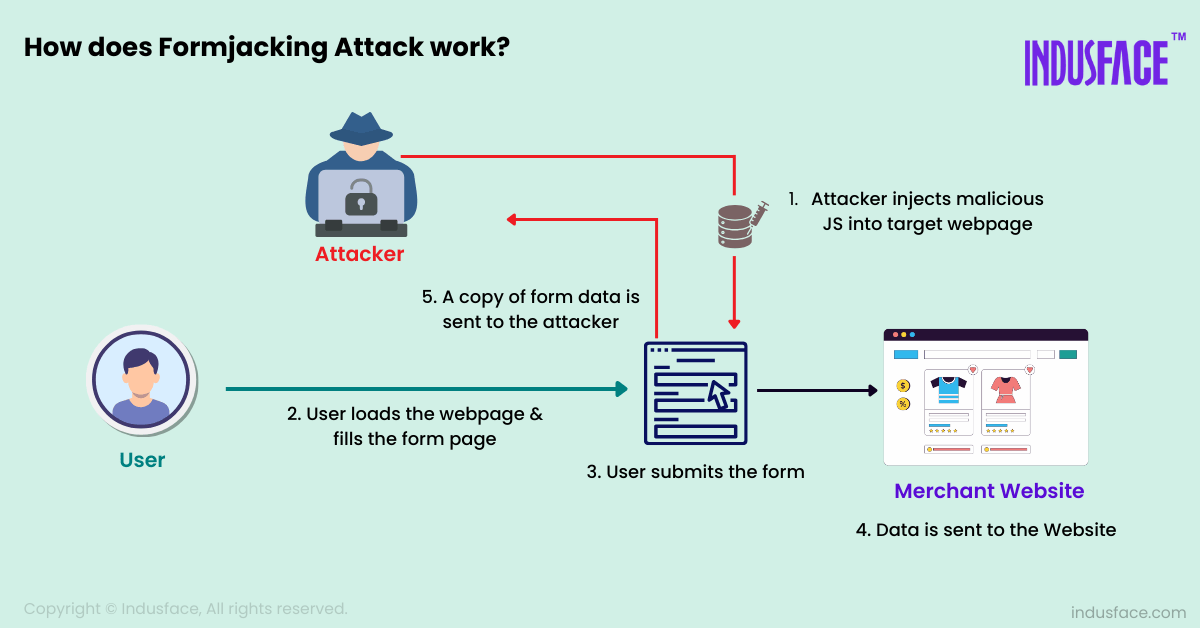
For example, suppose a user visits your website to log in to their account and enters their username and password. In that case, a Formjacking attack involves malicious code inserted into the login form.
The malicious code functions as a middleman between the user and the website, intercepting the data entered on the form.
It captures the login credentials and forwards the data to the attacker’s server. This interception occurs without altering the appearance or functionality of the form, so the customer remains unaware that their data is being stolen. The attackers then use this stolen information for fraudulent transactions and identity theft or sell it on dark web marketplaces.
Formjacking and Magecart Attack
Magecart attacks, a subset of formjacking, specifically focus on e-commerce sites, where they inject malicious JavaScript into payment processing systems to capture payment card information during transactions.
Both attacks are stealthy and can be difficult to detect, as the malicious code often blends in with legitimate form processes.
Business Impact of the Formjacking Attack
Non-Compliance Consequences: Businesses may face serious legal and financial consequences from non-compliance with data protection regulations like PCI-DSS, GDPR, or CCPA, including hefty fines.
Specifically, PCI DSS 4.0 introduces key requirements for client-side security to ensure compliance:
Requirement 6.3.2: Organizations must inventory all custom and third-party software, including payment software components and dependencies. This ensures comprehensive vulnerability management and effective patching strategies.
Requirement 6.4.3: Scripts executed in customer browsers must be authorized and documented. This requirement includes maintaining a detailed inventory of scripts and justifying their necessity, alongside implementing measures to ensure their integrity.
Section 11.6.1: Organizations must implement systems to monitor and detect any unauthorized modifications to HTTP headers and the content of payment pages in users’ browsers.
While these requirements are currently considered best practices, they will become mandatory on March 31, 2025.
Customer Behavior Change: Once trust is broken, customers may switch to competitors perceived as more secure, leading to a sustained decline in user engagement and retention. This shift can result in losing existing and potential customers who might view the company as unreliable.
Revenue Loss: A Formjacking attack typically causes an immediate drop in sales as customers question the site’s security. The long-term impact includes reduced revenue while the business rebuilds its damaged reputation.
Operational Disruption: Businesses may need to take their websites offline to address the attack, causing significant downtime and revenue loss. The costs of investigating the breach, removing malicious code, and implementing new security measures can strain resources and disrupt normal operations.
Why Is It Difficult To Detect Formjacking Attacks?
Detecting malicious code in Formjacking attacks is challenging because traditional security tools cannot oversee the end user’s behavior.
Malicious scripts are often designed to evade detection by dynamically loading or targeting a limited number of users. They may only activate in a genuine client-side environment or erase themselves from memory when they detect analysis attempts.
As a result, these scripts may go unnoticed during routine scans. Additionally, third-party scripts are subject to frequent changes and can be compromised at any point between scans or when they are executed downstream.
If a vulnerability anywhere in the supply chain leads to a Formjacking attack, your business is ultimately accountable for the consequences. Check out the best practices to prevent supply chain attacks.
Protect Your Site with AppTrana WAAP
AppTrana WAAP offers robust client-side protection by continuously monitoring all client-side JavaScript on your website. By continuously monitoring client-side JavaScript, AppTrana WAAP ensures that malicious activities, including Formjacking attacks, are detected and addressed.
It integrates Content Security Policy (CSP) headers, which restrict the sources from which scripts can be loaded, thus preventing the execution of malicious scripts and protecting against data exfiltration.
The platform also creates a comprehensive inventory of all JavaScript services, automatically discovering and tracking third-party scripts. this is the first step to comply with the new PCI DSS v4.0 requirements. The inventory offers valuable insights and controls over these services to identify and mitigate potential threats.
Other Effective Ways to Protect Formjacking Attack
To prevent Formjacking attacks, consider implementing these additional recommendations:
Regularly Audit and Update Dependencies – Regularly review and update all third-party scripts and libraries used on your website. Make sure they originate from trusted sources and have no known vulnerabilities.
Use Secure Code Practices – Follow secure coding practices to minimize vulnerabilities. This includes input validation, output encoding, and avoiding direct inclusion of external scripts without proper checks.
Conduct Regular Security Testing: – Perform regular security assessments, including penetration testing and vulnerability scanning, to identify and address potential weaknesses in your website.
Monitor for Anomalies – Continuously monitor your website for unusual activities or changes in the behavior of your forms. Implement anomaly detection systems to detect and address potential attacks early.
Implement Least Privilege Principle – Ensure that third-party services and scripts operate with the minimum level of access necessary to function. This limits the potential impact of a compromised script.
With AppTrana WAAP’s comprehensive client-side protection and these additional practices, you can effectively safeguard your website against formjacking and other JavaScript-based attacks.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 August 26, 2024
August 26, 2024




