Understanding CSRF Attacks: Risk Analysis, Protection & Anti-CSRF Tokens
Cross-Site Request Forgery (CSRF) remains a continuing threat, exposing user data and application integrity.
However, with proactive measures like anti-CSRF tokens and additional defenses, you can protect your applications against CSRF attacks.
Let’s delve into the depths of CSRF vulnerabilities and explore practical strategies to boost your web application security.
What is Cross Site Request Forgery (CSRF)?
A CSRF (Cross-Site Request Forgery) attack exploits a website’s trust in a user’s browser to perform unauthorized actions on behalf of the user. Attackers trick users into unknowingly performing unauthorized actions on a targeted website while authenticated.
This could range from transferring funds to altering account settings, posing a significant risk to user privacy and security.
A successful CSRF attack relies on various factors:
- Authentication Tokens or Session Cookies: The attacker must obtain the victim’s authentication token or session cookie, which authenticates the user to the targeted website.
- User Interaction:The attacker must trick the victim into interacting with malicious content, such as clicking on a link or visiting a CSRF exploit website.
- Target Website’s Trust in User’s Browser: The targeted website must trust the user’s browser to automatically include authentication tokens or session cookies with requests, even if they originate from another website.
- Lack of CSRF Protections:The absence of CSRF token or inadequacy of CSRF protections, such as same-site cookie attributes, makes the website vulnerable to CSRF attacks.
- Impactful Actions:The attack’s success often depends on the potential impact of the actions performed by the forged request, such as transferring funds, changing passwords, or modifying sensitive account settings.
- Social Engineering Tactics: Effective social engineering tactics, such as phishing emails or deceptive messaging, can increase the likelihood of the victim interacting with the malicious content.
- Timing and Persistence: The attacker’s success depends on timing the attack when the victim is logged in and maintaining control over the victim’s session.
By exploiting these factors, attackers can successfully execute CSRF attacks, gaining unauthorized access to users’ accounts and performing malicious actions on their behalf.
XSS vs. CSRF: How Do They Differ?
XSS involves injecting malicious scripts into web pages viewed by other users, exploiting trust between users and content. CSRF executes unauthorized actions on authenticated web applications, exploiting trust between users and the application. XSS steals data or hijacks sessions, while CSRF performs actions on behalf of users without their consent.
Preventing XSS requires input validation and output encoding, while CSRF prevention involves the use of anti-CSRF tokens.
How Does CSRF Attack Work?
Launching such CSRF attacks is possible in practice because many users browse multiple sites in parallel, and users often do not explicitly log out when they finish using a website.
Here’s how it works:
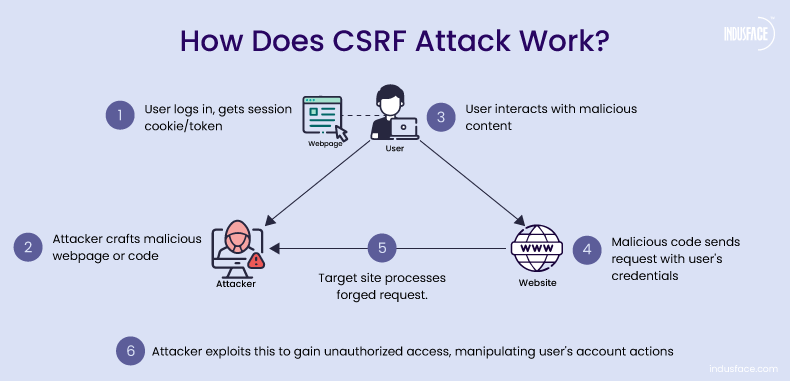
- When a user logs into a website, they typically receive a session cookie or authentication token that the website uses to recognize them as a logged-in user.
- An attacker creates a malicious webpage or injects malicious code into a legitimate webpage. This code contains a request to the target website, such as transferring funds or changing account settings.
- The attacker tricks the user into visiting the malicious webpage or interacting with the compromised webpage, often through social engineering techniques like phishing emails or malicious links.
- The malicious code in the webpage sends a request to the target website. This request includes the user’s authentication token or session cookie, which the browser automatically attaches since it’s from the same origin.
- The target website receives the request and processes it as if it were legitimate because it contains valid authentication credentials. This can lead to actions being performed on the user’s behalf without their consent or knowledge.
- The attacker gains unauthorized access to the user’s account and can carry out actions such as transferring funds, changing account settings, or accessing sensitive information.
A CSRF attack can also occur without a user visiting a malicious webpage. For instance, in a CSRF attack against residential ADSL routers in Mexico, an email with a malicious IMG tag was sent to victims.
By viewing the email message, the user initiated an HTTP request, which sent a router command to change the DNS entry of a leading Mexican bank, making any subsequent access to the bank by a user go through the attacker’s server.
What are the Impacts of CSRF Attacks?
Cross-Site Request Forgery attacks pose a significant threat, ranking at the top of the OWASP 2021 Top 10 list of vulnerabilities under Broken Access Control failures. These attacks can have severe consequences depending on the privileges of the victim and the assets targeted. Here’s a breakdown of the potential impacts:
- Account Takeover:Attackers can gain complete control over a victim’s account, allowing them to access sensitive information and carry out unauthorized actions. Learn more about account takeover attacks.
- Fraudulent Transactions:CSRF attacks enable fraudsters to initiate unauthorized fund transfers or transactions from the victim’s account.
- Data Breaches:By exploiting CSRF vulnerabilities, attackers may breach the confidentiality of data stored or processed by the targeted application.
- Financial Loss and Reputation Damage:CSRF attacks can result in financial losses for individuals and organizations, damage to their reputations, and loss of trust among users.
- Disruption of Application Functionality:CSRF attacks can compromise the functionality of the targeted application, leading to service disruptions and usability issues.
- Credential Manipulation:Attackers may manipulate account credentials, such as passwords or email addresses, through CSRF attacks, further risking security.
How to Prevent CSRF Attack?
The Role of Anti-CSRF Tokens
An Anti-CSRF token, also referred to as an XSRF or CSRF token, is a unique and secure code generated by the server and inserted into forms or requests to prevent unauthorized actions.
During form submission or request execution, the server verifies the token’s authenticity, thwarting unauthorized actions initiated by malicious parties.
Example:
<input type=”hidden” name=”csrf_token” value=”k8Dh2P9zF7s4Q”>
<!– Other form fields –>
<button type=”submit”>Submit</button>
</form>
Synchronizer Token Pattern
The synchronizer token pattern is a commonly used token-based CSRF protection technique. Here, XSRF tokens are generated by the server-side application and transmitted to the client side in a way that is included in the subsequent HTTP request.
When the user sends a request, the server-side application verifies and validates the request to ensure the expected token is included. The server-side application rejects the request if the relevant token is not included. So, only original users are authenticated to send requests in each session.
Best Practices in Token Handling
Several best practices should be followed in generating and validating tokens:
- Utilize a non-predictable random number generator with ample information to ensure that the token is unique and cannot be guessed by a third party.
- Safeguard tokens throughout their lifecycle, ensuring secrecy and secure handling.
- Transmit tokens discreetly, often within hidden fields of HTML forms, positioned early in the document for enhanced security.
- Set short expiry periods to prevent token reuse.
- Avoid transmitting tokens via cookies for heightened CSRF protection.
- Utilize secure methods like hash comparison to verify anti-CSRF tokens.
- Refrain from sending tokens in HTTP GET requests to prevent URL exposure or leakage through the Referrer header.
Choosing Between Session and Request Tokens
XSRF tokens can be generated once per session or for each request. Per-request tokens are more secure than per-session tokens as they allow attackers a shorter time to exploit them.
So, tokens are generated for each session in scenarios where a higher level of protection is necessary. As soon as it is verified, the token is invalidated.
Drawbacks and Alternatives
Despite its effectiveness, the synchronizer token pattern has some drawbacks:
- It may disrupt user experiences, especially with multiple tabs or the back button.
- It could strain server performance under heavy traffic volumes.
Alternatives such as non-persisted tokens can be used to mitigate these drawbacks. These cryptographic tokens do not require the web app to store anti-CSRF tokens in the server sessions, but they consume more resources due to encryption.
Special Consideration for Login Forms
Even during login processes, CSRF protection remains crucial to prevent user impersonation and unauthorized login attempts by attackers.
Thus, implementing anti-CSRF measures ensures comprehensive security throughout user sessions and interactions with web applications.
Beyond Anti-CSRF Tokens: Additional Steps to Prevent CSRF Attacks
Anti-CSRF tokens offer strong protection, but enhancing security with additional measures helps protect your application against evolving threats:
Content Security Policy (CSP): Implement CSP directives to mitigate the impact of XSS attacks, a common vector for CSRF exploitation.
Time-Limited Tokens: Employ short-lived tokens to limit their validity window, reducing the window of opportunity for attackers to exploit stolen tokens.
Implement SameSite Cookies: Configure cookies with the “SameSite” attribute set to “Strict” or “Lax” to restrict cross-origin requests. This prevents the browser from sending cookies in cross-origin requests, mitigating CSRF attacks.
Use CSRF Tokens in Custom Headers: Besides embedding CSRF tokens in form fields, include them in custom HTTP headers. Verify these tokens on the server side for every request, providing additional protection against CSRF attacks.
Employ Referer Header Checking: Validate the “Referer” header on incoming requests to ensure they originate from the same domain. Although not foolproof due to potential spoofing, it can provide an extra defense against CSRF attacks.
Utilize Double Submit Cookies: Implement a double-submit cookie pattern where the CSRF token is stored in both a cookie and a request parameter. To validate authenticity during form submission, compare the cookie token with the request parameter token.
Implement CAPTCHA: Integrate CAPTCHA challenges for critical actions or requests susceptible to CSRF attacks. This adds a step for users to verify their identity, making it more challenging for automated attacks to succeed.
Enforce Multi-Factor Authentication (MFA): Require users to authenticate using multiple factors, such as passwords and one-time codes sent via SMS or authenticator apps. MFA adds an extra layer of security, reducing the likelihood of successful CSRF attacks even if authentication tokens are compromised.
Employ Proper Session Management: Implement secure session management practices, including short session timeouts, session rotation, and cookie attributes like “HttpOnly” and “Secure.” This limits the window of opportunity for CSRF attacks and reduces the impact of compromised session tokens.
Regular Security Audits and Testing: Conduct regular vulnerability assessments and penetration testing to identify and address vulnerabilities in your application—test for CSRF vulnerabilities using automated scanners and manual testing techniques to avoid emerging threats.
How WAF(WAAP) Protects Against CSRF (Cross-Site Request Forgery)?
A robust WAF/WAAP solution helps mitigate CSRF risks by enforcing strict security policies, validating request integrity, and blocking unauthorized access attempts. Here’s how:
- CSRF Token Validation – WAFs enforce policies requiring valid CSRF tokens in requests to block unauthorized actions. AppTrana WAAP allows tailored custom rules to detect anomalies, such as missing or invalid tokens, and mitigate potential attacks.
- Anomaly Detection – A WAF can identify suspicious patterns, such as repeated requests without CSRF tokens, signaling a potential attack.
- Referer Header Validation – WAFs validate the Referer header to ensure that requests originate from trusted sources. If the header is missing or does not match the application’s domain, the request can be blocked.
- Content-Type Enforcement – WAFs inspect and enforce specific Content-Type headers (e.g., application/json, application/x-www-form-urlencoded) to prevent unauthorized request formats from executing CSRF payloads.
- SameSite Cookie Enforcement – Modern web security relies on SameSite cookie attributes, which restrict cookies from being sent with cross-site requests. WAF enforces SameSite=Lax or SameSite=Strict policies, ensuring cookies are not sent with requests from other websites, reducing CSRF risks.
- CORS Policy Enforcement – WAAP solutions help organizations implement Cross-Origin Resource Sharing (CORS) policies, preventing unauthorized web applications from making cross-site requests to protected APIs.
Additionally, AppTrana’s inbuilt DAST scanner and penetration testing service help identify security misconfigurations that attackers could exploit in CSRF attacks. It analyzes potential attack paths, offers actionable mitigation strategies, and provides detailed reports to streamline security integration within CI/CD workflows.
Once CSRF vulnerabilities are detected through penetration testing and continuous monitoring, virtual patches at the WAF level enables to block exploit attempts, ensuring real-time protection without requiring immediate code change.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 11, 2025
March 11, 2025



