How to Use MITRE ATT&CK to Mitigate API & Other Attacks?
With a threat landscape expanding at an accelerated pace, it is next to impossible for any organization to even keep track of and monitor the volume, frequency, complexity, and breadth of the attack techniques and tactics out there. But to effectively tackle threats and protect mission-critical assets, the knowledge of these common attack techniques, tactics, detection, and mitigation is critical. This is where MITRE ATT&CK is especially useful.
Keep reading for a deeper understanding of MITRE attack frameworks and how they work.
What is MITRE ATT&CK?
Developed by MITRE, ATT&CK is the acronym for Adversarial Tactics, Techniques, and Common Knowledge. MITRE is a not-for-profit organization established to provide engineering and technical guidance to the US government.MITRE ATT&CK is a globally accessible, documented knowledge base of malicious behaviours, techniques, and tactics leveraged by attackers across the entire attack lifecycle. The MITRE ATT&CK framework is curated based on real-world observations of cyberattacks.
What Does It Contain?
ATT&CK is like an encyclopedia of references telling organizations how attacks are orchestrated and providing recommendations for detecting and mitigating known threats with:
- Detailed descriptions of observed tactics, techniques, and procedures (called TTP)
- An extensive list of malware, open-source code, commercially-available codes, and other software that may be used legitimately or maliciously by attackers
- Known practices, characteristics, and specific attack attributes of advanced persistent threats
MITRE ATT&CK is not just a collection of data, but a tool intended to empower organizations to strengthen their security posture. It is also important to note that ATT&CK is not a threat model, unlike PASTA, STRIDE, and OCTAVE.
This knowledge base is to be used as a tool by organizations to evaluate the strength of their current defenses and build their own customized threat models to detect and prevent attacks effectively.
Who Uses MITRE ATT&CK?
The MITRE ATT&CK framework is a free, globally accessible tool widely leveraged by all organizations of all sizes and industries in the public and private sectors. It is as useful to government agencies as to a cybersecurity product company, a hospital, or small business.ATT&CK is also leveraged by red teams, cyber threat intelligence teams, penetration testers, security defenders, and internal teams looking to build secure applications, APIs, systems, and services.
Some of the key use cases include:
- Performing security gap analysis and thereon strengthening security
- Augment threat intelligence
- Bettering alert triggering and investigation
- Assess the maturity of SOC
How Does MITRE ATT&CK Help Organizations?
- A powerful tool that augments red and blue teams to build custom threat models and strengthen security.
- Enables organizations to enrich their threat intelligence by understanding different adversaries’ profiles, unique methods and techniques, and behaviours.
- With MITRE ATT&CK, organizations can compare the capabilities of security products from various vendors and their effectiveness in addressing threats, thus, identifying the right vendor for their needs.
- Equips organizations with a common language to engage with vendors and consultants.
- It helps simplify reporting for non-technical executives by providing a visual medium.
- A helpful resource for those interested in or wanting to make a foray into cybersecurity or threat intelligence.
How Does MITRE ATT&CK Work?
The MITRE ATT&CK framework offers matrices for enterprises, mobile, and ICS (Industrial Control Systems). Under each of these matrices, they are variations for different platforms. For instance, the Enterprise matrix has variations for Windows, macOS, cloud, network, containers, PRE, etc., while the Mobile Matrix offers Android and iOS variations.Each of these matrices categorizes tactics leveraged by attackers at different stages of the attack lifecycle and the techniques leveraged to accomplish specific tasks and goals at each stage.
ATT&CK Tactics
Tactics in the ATT&CK framework represent the technical objectives and tactical goals that attackers try to achieve. Tactics explain what attackers are trying to accomplish and why they use specific methods, techniques, or sub-techniques.
For instance, the Enterprise matrix has 14 catalogued adversary tactics, including reconnaissance, privilege escalation, credential access, discovery, etc.
MITRE ATT&CK Techniques
MITRE ATT&CK techniques explain the how of attacks – how the attackers are accomplishing their tactical goals by performing specific actions. For instance, if the tactical goal is credential access, the attacker may use brute force attacks or man-in-the-middle attacks as their techniques.
Each technique contains descriptions of methods, procedures, sub-techniques, detection, and mitigation.
Here is what the ATT&CK matrix looks like:
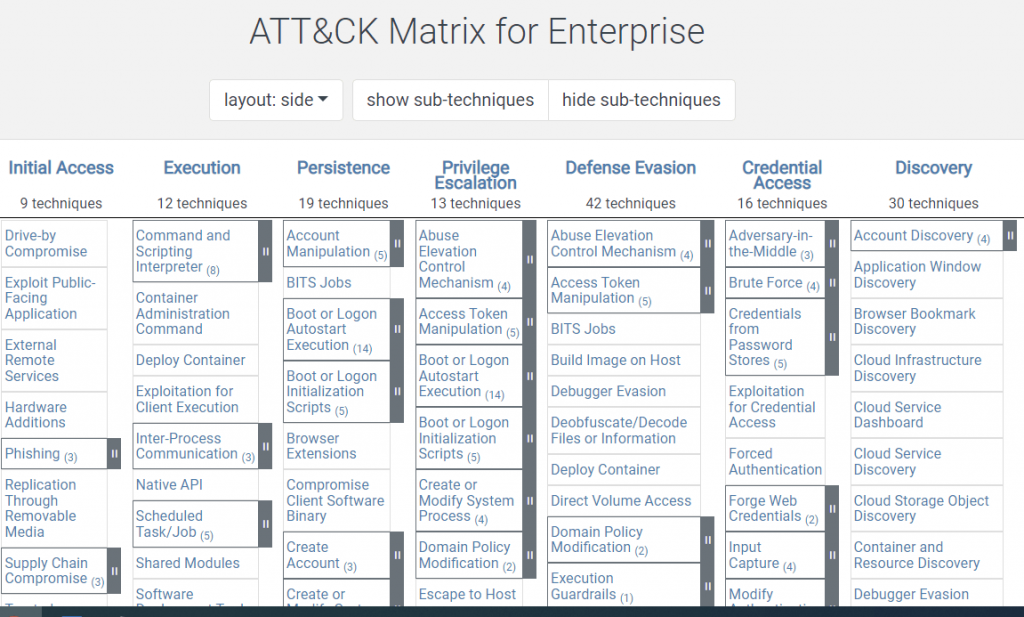
Source: MITRE ATT&CK
By referring to these tactics, you can prioritize your defense strategies.
Mapping Out MITRE ATT&CK Techniques Using API
For attackers to execute an attack, they will apply one or more of these tactics listed in the execution column. For example, let us consider Native API. Attackers target APIs as they provide direct access to critical data. Here are some example behaviours that attackers use to interact with victims’ APIs.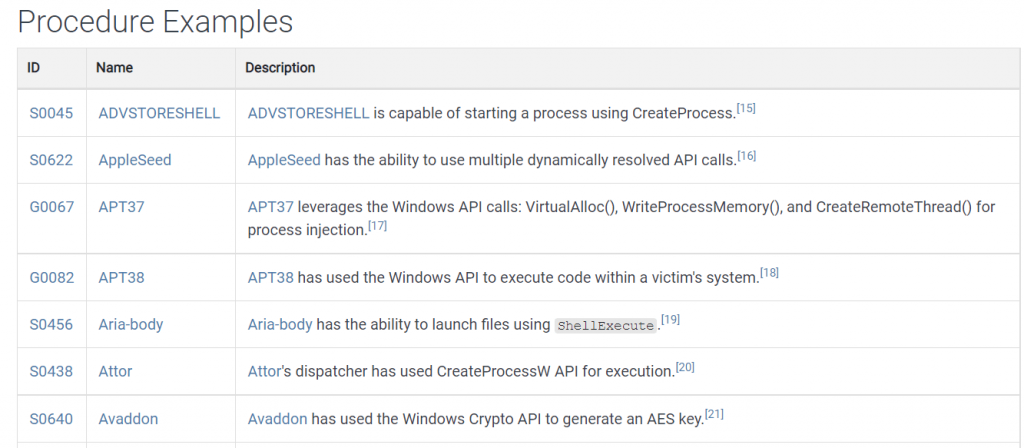
Source: MITRE ATT&CK
It lists the areas that are a potential risk for your business. If your APIs are unprotected, attackers will utilize them. Look at your threat detection capabilities by combing all these details together.
With AppTrana API protection, you can use close these security gaps. You can also enhance your security posture is secured against API and other attacks.
Where Does the Information Come From?
The MITRE ATT&CK knowledge base is built using publicly available data, threat intelligence, incident reports, and research on new techniques by cybersecurity analysts, security teams, and threat hunters.
Conclusion
Taking an attacker’s point of view, unlike other models that take the defender’s perspective, MITRE ATT&CK is a powerful tool that empowers organizations to think like attackers, simulate breach scenarios, test the strength of security controls, and thereon, effectively prevent attacks.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn


 September 29, 2022
September 29, 2022



