Indusface Web Application Scanning Product Update
On the WAS side, our effort was to build upon the new scanner that we recently released and add features that would provide
Some of the major advances made on WAS side are as follows:
SIGNATURE UPDATE
Signatures were added to find the following vulnerabilities:
- Session ID scoped to parent domain: The session cookie is scoped to the parent domain instead of a sub-domain. if a cookie is scoped to a parent domain, then this cookie will be accessible by the parent domain and also by any other sub-domains of the parent domain. This could lead to security problems.
- XML RPC Vulnerability: XML-RPC is a remote procedure calling using HTTP as the transport and XML as the encoding. An attacker can abuse this interface to brute force authentication credentials using API calls.
- HSTS Missing From HTTPS Server: HTTP Strict Transport Security (HSTS) is a web security policy mechanism whereby a web server declares that complying user agents (such as a web browser) are to interact with it using only secure HTTP (HTTPS) connections. The HSTS Policy is communicated by the server to the user agent via an HTTP response header field named “Strict-Transport-Security”. HSTS Policy specifies a period of time during which the user agent shall access the server in an only secure fashion. if this is missing then insecure agents would be able to connect.
GUIDED SCANS
Config-driven guided scan support was introduced. Guides are lists of actions that will be taken automatically when all elements defined in that set of actions are encountered during the crawl. Multiple guides can be defined per site. This will help the crawler go to pages which it could not go before because of the need for special actions. For example, say there is a multi-step wizard, where certain fields and inputs need to be provided to reach the next step unless the crawler knows what these actions are there is no way it goes further.
Now in such cases, a guided scan config can be added which tells the crawler exactly what actions need to be taken. For customers needing such ability are requested to contact our support team, they would write the necessary config for your site and add it.
SCAN CONFIGS
Also, we had enabled the ability to add certain site-specific configs which would help customers create certain exceptions like
- Exclude URI from Attack: We have seen cases where there can be certain URI’s that customers want to crawl to as it is through this that other pages can be reached but do not want the attack to happen. in such cases, customers can get certain URI whitelisted from attacks. This can be done by reaching out to support@indusface.com
- Crawl to foreign domain: By default, crawler does not crawl foreign domain, but in cases of SSO logins, etc, it becomes important to crawl certain foreign domain URI’s. Now, this can be done through a special config for a website. Please reach out to support to enable this.
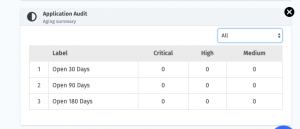
AGING SUMMARY
We have added the Aging Summary widget for AA, MM and VA scans. With this customers can easily identify vulnerabilities that are older than a certain time period. Which would help customers prioritize the fix for vulnerabilities?
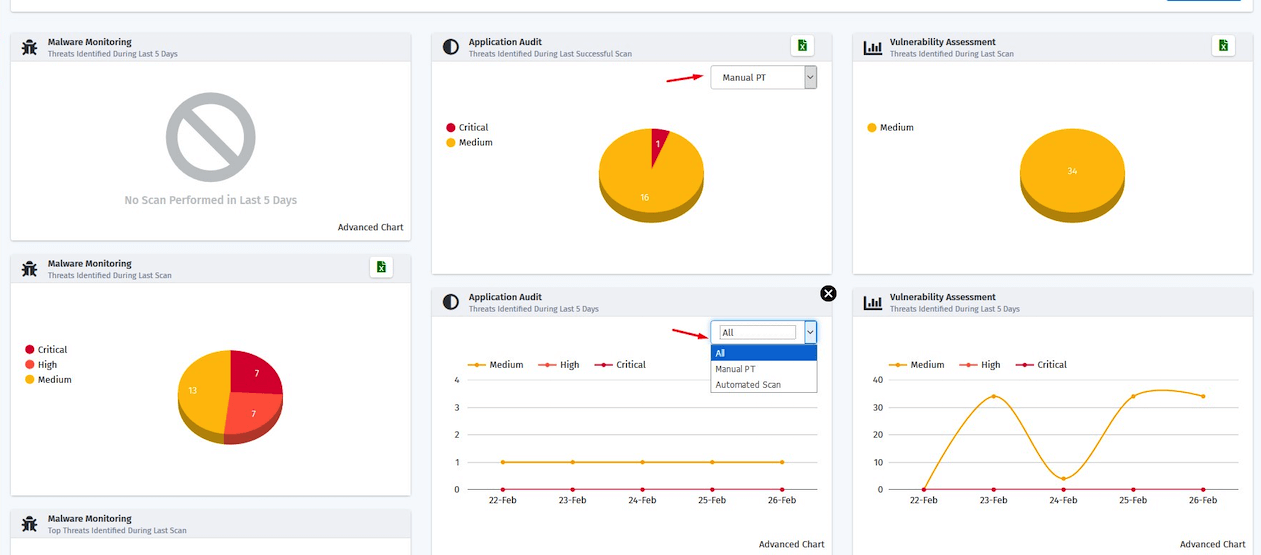
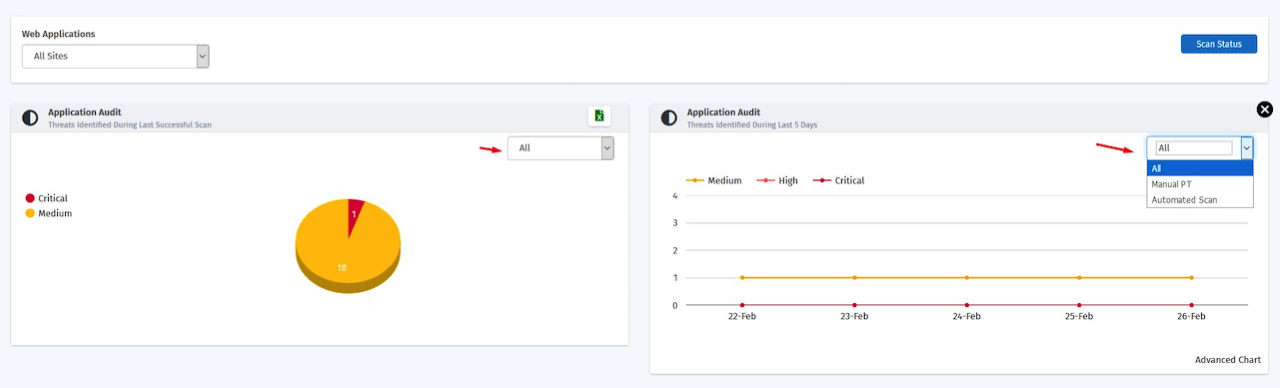
BIFURCATION OF MANUAL AND AUTOMATED VULNERABILITY AS A WIDGET IN DASHBOARD
With this customers can clearly see the vulnerabilities found through Manual PT vs Automated scans in the application audit widgets in the portal using the Manual PT & Automated scan filters available in the widgets The changes are done both in the Dashboard page and application audit page


 April 11, 2019
April 11, 2019






