DDoS Mitigation – Techniques, Features, and Choosing the Best Solution
DDoS attacks affect millions of websites every day. In Q1 2024, AppTrana WAAP successfully blocked over 8.75 million DDoS attacks, marking a 76% increase from Q1 2023.
Here is a snapshot of the DDoS attack trend over Q1 2024 across all websites.
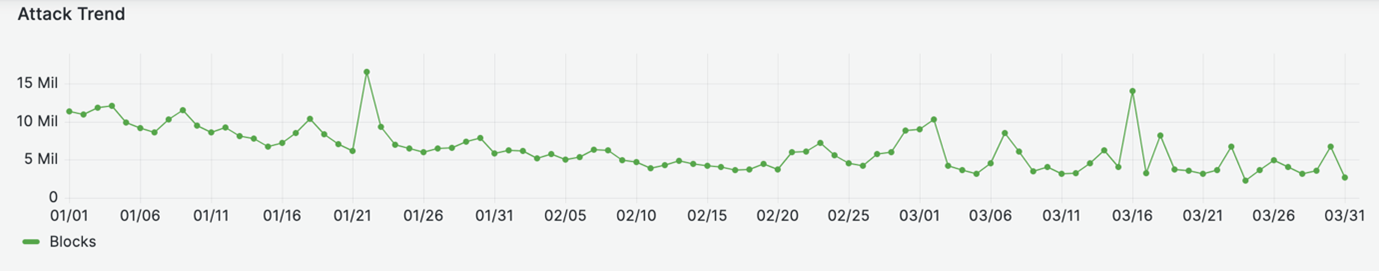
DDoS attack trends – The State of Application Security Q1, 2024
No business is immune to DDoS threats. Implementing a DDoS mitigation solution is crucial to protect your business.
However, not all DDoS protection vendors provide the same level of protection and features.
What exactly is DDoS mitigation, and what key features should you look for in a solution? How can you choose the right DDoS mitigation service provider? Find comprehensive answers to these questions in our detailed DDoS mitigation guide.
What is DDoS Mitigation?
DDoS mitigation is a comprehensive approach to defending against DDoS attacks, which aim to disrupt the normal functioning of a target (usually a server, network, or web application).
The process involves a combination of detection, response, and prevention strategies designed to maintain service availability and performance even during and after an attack.
DDoS mitigation solutions encompass specialized cloud-based services, and software solutions tailored to effectively identify, mitigate, and recover from DDoS attacks immediately and efficiently.
Why is DDoS Mitigation Important?
Cybercriminals are gaining the edge in tactics to deny the service through DDoS attacks. These attacks can take your business offline for minutes, hours, or even weeks resulting in substantial financial and reputational damage.
On average, DDoS attacks cost enterprises over $2 million, according to Kaspersky’s findings.
Tangible Costs of DDoS Attacks
Restoration Costs
The immediate need to get applications back online involves significant expenditure on technical resources, including personnel, software, and hardware.
Lost Revenue
Downtime results in a direct loss of sales and business opportunities as customers are unable to access the services. This lost revenue can be substantial, especially for e-commerce businesses and other online services.
Ransom Payments
In some cases, attackers demand a ransom to stop the DDoS attack, adding another layer of financial strain on the affected business.
Intangible Costs of DDoS Attacks
Brand Reputation
Prolonged downtime can damage a company’s reputation. Customers may perceive the business as unreliable, affecting long-term trust and brand loyalty.
Loss of Customer Trust
Customers losing access to services can lead to dissatisfaction and a decline in future sales. Restoring customer trust after such an incident can be challenging and time-consuming.
Implementing a DDoS mitigation solution can significantly reduce the risk of damage from DDoS attacks. Here are some key benefits:
- Ensure continuous service availability and quick recovery from attacks, minimizing disruptions to your business operations.
- Lower the costs associated with web security without sacrificing quality, providing robust protection in a cost-efficient manner.
- Keep your website and applications running smoothly during attacks by filtering out malicious traffic and prioritizing legitimate users.
- Utilize advanced security rules to protect against current threats and adapt to new ones as they emerge.
- Stay ahead of evolving attack methods with regularly updated security policies, ensuring comprehensive and effective mitigation against DDoS protection.
How does DDoS Mitigation Work?
DDoS mitigation works by identifying and blocking malicious traffic through methods such as rate limiting. The solution absorbs and filters attack traffic before it reaches the target network or website, often redirecting it to a scrubbing center for analysis and filtering.
To understand the details of DDoS mitigation, watch this short clip from my recent webinar, “Fundamentals of DDoS Risk Mitigation.”
The Four Stages of DDoS Mitigation
1. Absorption
The first step in countering a DDoS attack is to absorb the attack, so the application doesn’t go down. Whatever solution you choose, it is critical to understand how much testing has been done on requests per minute and concurrent IPs.
Ideally, cloud-based DDoS protection solutions are better as they have autoscaling available. On-premises DDoS protection fall short as the number of servers limits them.
2. Detection
The next step is to detect that it is a valid DDoS attack. The solution should be able to tell:
- How many requests coming at a URI level?
- How many requests from an IP?
- How many requests are at a session/host level?
- How many requests are in the overall domain?
3. Prevention
The next step is to prevent the attacks from being passed on to the application. The DDoS mitigation software identifies attack vectors and blocks requests made with those attack vectors. Then it detects diverse multi-vector attacks.
AI plays a big part in DDoS attack mitigation techniques. The DDoS attack mitigation solution should ideally be able to use past data and predict site behavior.
At any point, the solution should be able to recommend and apply “rate limits” as granularly as possible. These include URI, session/host, IP, and domain rate limits.
4. Retaliation
Retaliation is where “managed services”, or DDoS protection services offered by WAF vendors shine.
While AI can recommend rate limits and even apply “blocking rules,” having managed service will largely reduce false positives. After all, fundamentally, DDoS attacks look like legitimate requests.
A DDoS mitigation service works in two phases:
1. Monitoring: The managed services team monitors all incoming alerts. For example, let’s say that an image file usually accessed once a minute is suddenly accessed 100 times a minute. Overall, at a site level, there is a small increment in requests. However, the AI will alert the managed services team and the application owner.
2. Mitigation: The second step is mitigation. After analyzing all trends, including requests per minute, malicious IPs, and so on, the solution provider team should be able to add surgical rate-limiting rules. Other mitigating mechanisms should also be added, including tarpitting, CAPTCHAs, and more.
Key Features of DDoS Mitigation Solutions
Here are the advanced features of the DDoS protection platform that provide ultimate protection against sophisticated attacks.
AI/ML based Rate Limiting
Rate limiting is a standard technique of the DDoS attack mitigation method. It enables you to limit the traffic coming from certain IPs. It helps block the apps, users, or bots from overusing your resources.
In addition to static rate limiting, the solution should be able to configure policies based on the application’s behavior. In case of an anomaly, the solution should be able to trigger an alert.
Most DDoS attacks are sub-saturating and short attacks. These attacks will likely last less than 5 minutes and under a network range of 1 GB/s. These minimalistic attacks are prone to evading scrutiny and detection by static rate-limiting techniques.
Such configuration ignores shorter attack activity. Thereby creating weaker detection thresholds.
Implement a solution that uses AI driven behavior analysis of application traffic patterns. This approach helps establish recommended detection threshold values, reducing false positives and enabling faster anomaly detection.
Granular Level Controls
DDoS mitigation solutions enable you to add granular configurations to prevent attacks with custom policies. Users can define policies based on Geo, URI, IP headers, and source and destination IP.
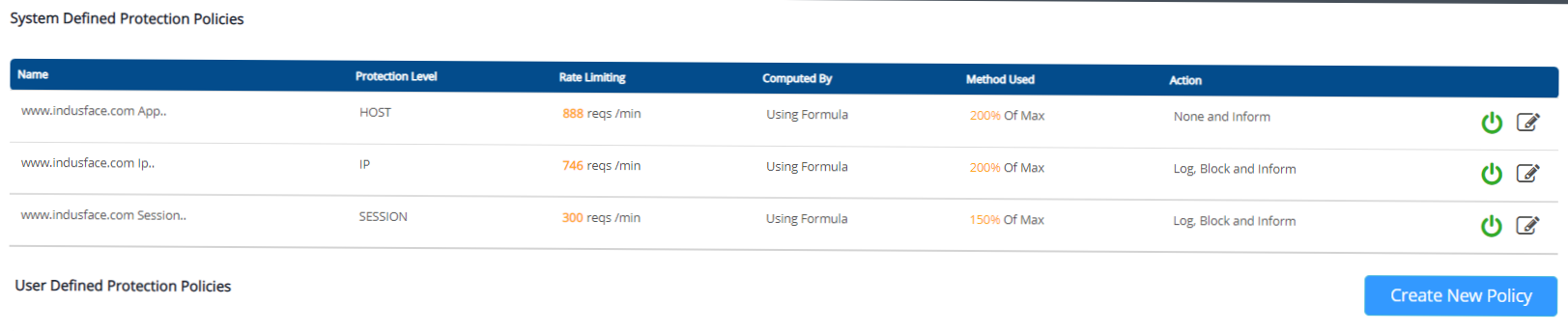
The threshold for these policies should ideally be auto-configured via behavior-based traffic profiling.
That said, marketing campaigns could generate bursts of requests, and leveraging the managed services team for DDoS mitigation will help reduce false positives.
Global Controls
IP whitelisting and blacklisting play a critical role in managing internal server requests and requests that come from actual users.
Blacklisting and Whitelisting specific IP addresses or countries is very important for the following reasons:
- You do not want some parts of your application to work for specific countries
- You do not want to make some parts of your application available for public access
- You want to allow good bots to access your application
- You have internal servers that make abnormally high requests to your production server; neither should they be blocked by WAF, nor should they alter the behavioral DDoS rate limiting policy
Given the list of IPs to be managed, it becomes challenging for the security administrator to manage the blacklisting and whitelisting records in multiple files for each application.
With global controls, the user can view the status of all blacklisted/whitelisted IPs or countries in a single dashboard and modify the same status.
AppTrana also goes a step further; it allows you to make bulk entries of IP addresses/countries to blacklist/whitelist across all your applications instead of expecting you to make them.
It also allows you to override these global rules and modify some for specific applications.
Not just IPs but IP ranges
In AppTrana, you do not even have to enter all IP addresses individually; if you have a set of IP addresses that need to be blacklisted/whitelisted, you can enter the series of such IP addresses by simply mentioning them.
For example, 192.168.1.1/24 will block all IP addresses from 192.168.1.1, 192.168.1.2, 192.168.1.3….till 192.168.1.24, no rule will be applied on the IP 192.168.1.25 from the above selection.
Not just that, AppTrana also allows the security admin to review all the blacklisting and whitelisting actions and help debug any security loopholes.
Auto Scalability
Most DDoS attacks create a large traffic volume to exhaust the resource capacity. Sometimes when the traffic and network size expand, the prevention goes out of control. Thus, failing the mitigation process.
Highly scalable infrastructure is one of the key DDoS protection requirements. Thereby the solution can ramp up in line with the traffic that must be handled.
AppTrana, for example, is built to absorb the largest DDoS attacks. It leverages AWS infrastructure to block large attack traffic. While autoscaling is enabled, we assessed DDoS attacks of up to 2.3 TBps over 10,000 concurrent IPs.
Monitoring and Alerting
The security tool should be able to constantly monitor for potential attacks that target your resources. Then, it should be able to send out real-time alerts to the application owners and/or managed services team to monitor the attacks and take any corrective action if needed.
The alert should highlight the domain being attacked, the attack’s protocol, session details, user agents, geography, IP, and any other information that can help differentiate valid from invalid requests. This feature limits the time it takes to detect and block a DDoS attack.
Content Delivery Network
The DDoS mitigation service can take the load off your origin server by enabling CDN. When a request is received, the CDN server will respond with the cached version of the requested page.
In the case of a DDoS attack, the CDN can be used to absorb and distribute the attack traffic by redirecting it to multiple servers. This can help to prevent the attack traffic from overwhelming the origin server and causing the website to become unavailable.
BOT Protection
Hackers often create bot armies to launch DDoS attacks. The multi-layered architecture of advanced DDoS protection is equipped with bot protection policies to defend aganist DDoS Botnets.
Today bots are using crafty techniques to masquerade as Googlebot. Hackers know Googlebot is a bot that every business is going to whitelist.
The BOT Pretender Policies, for instance, help detect and block malicious bots which pretend to be helpful bots.
Broader Visibility
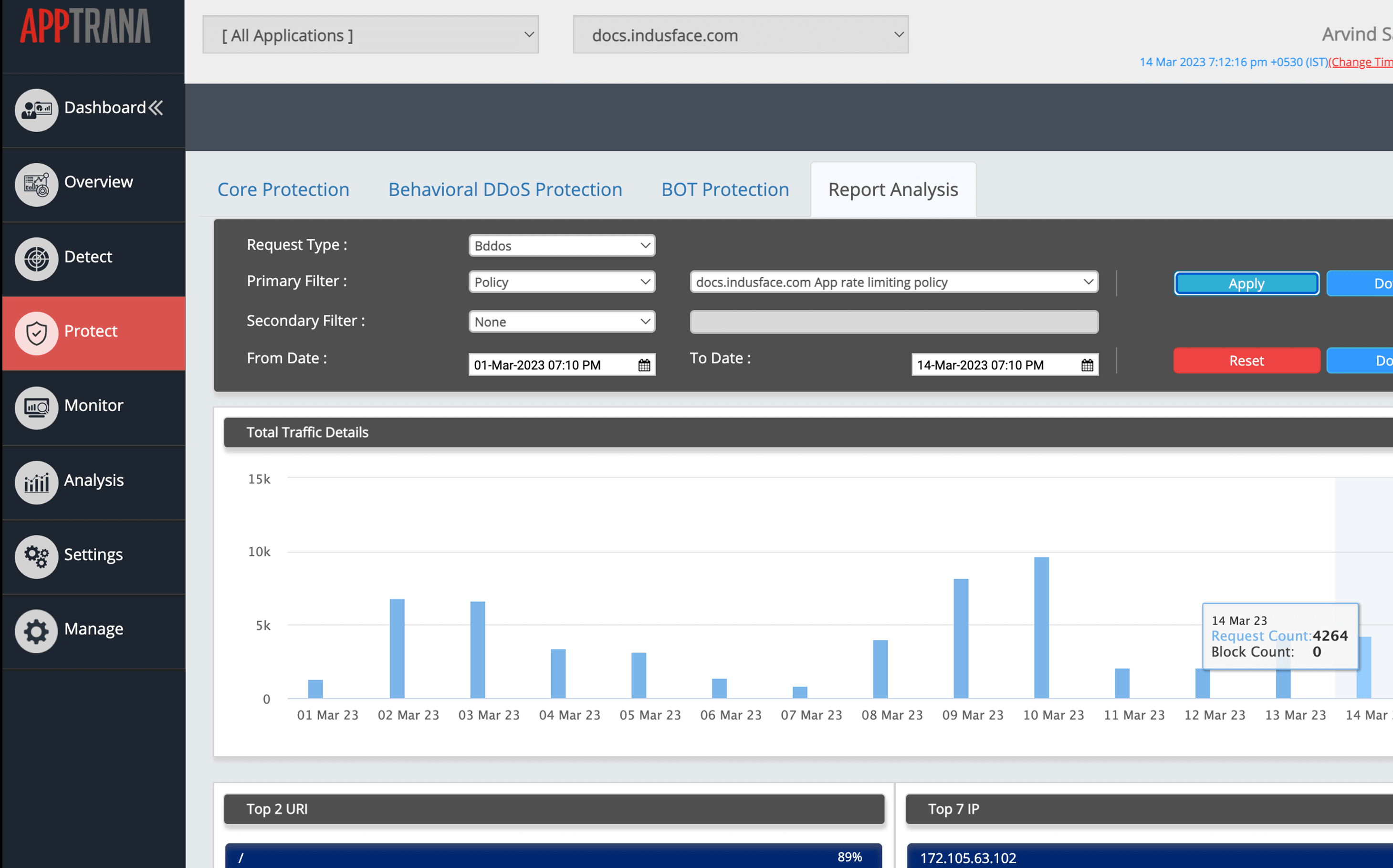
DDoS protection is not just for blocking attacks. The solution must provide users with important insights and analytics about the attacks. You can view the attack statistics categorized by IP and URLs.
The mitigation reports include traffic statistics, top 5 IPs, top 5 countries, and top 5 URI. The in-depth visibility simplifies forensics and ensures accurate DDoS mitigation.
For more detailed guidance on preventing DDoS attacks, check out our comprehensive blog on DDoS prevention best practices.
DDoS Monitoring Service
Every attacker leaves behind a unique fingerprint, which can be used to detect and prevent attacks. However, effectively leveraging this requires a robust solution capable of pattern identification and skilled experts to craft precise policies. This is where a DDoS monitoring service becomes crucial, enabling rapid response and mitigation. Solutions such as AppTrana deliver this level of service to customers.
False Positive Monitoring
Inaccurate security rule thresholds might wrongly identify legitimate login attempts as attacks, with normal users potentially triggering alerts due to specific behaviors. For example, repeated login attempts by users who forget their passwords could mistakenly be flagged as a brute-force attack.
To minimize false positives, choose a DDoS protection vendor that includes false positive monitoring as part of their service.
Origin Server Protection
Attackers often use tools like dnstrails.com to uncover legacy DNS settings that reveal the origin server’s IP address, allowing them to launch direct-to-origin DDoS attacks.
A robust DDoS protection tool should offer an origin server protection to stop attackers from directly targeting your origin server.
How To Choose A DDoS Mitigation Provider?
DDoS mitigation services use advanced methods like analyzing, filtering, and redirecting traffic to keep legitimate users accessing resources smoothly. This helps maintain business operations without interruptions, protecting against revenue loss, brand damage, and data breaches caused by DDoS attacks.
When evaluating DDoS mitigation providers, several key factors should be considered to ensure comprehensive protection tailored to the specific needs and risks of your organization.
Narrow Down your Risk Profile
The first step in choosing the right DDoS mitigation vendor is identifying your organization’s specific needs.
- How much bandwidth do you need?
- What is the cost of downtime for your organization?
- What kind of attacks are you most worried about?
- Do you want a preventative or reactive solution?
If you have already been a victim of such an attack, consider the factors that caused that past attack. Based on this analysis, gauge the unique needs of your website/ web application. Accordingly, research the different options and choose the best-fit solution.
Always on DDoS Protection
Suppose an attack occurs when the protection isn’t activated. Your business may not have enough time to turn the protection on before the DDoS attack causes significant damage.
Always-on DDoS protection is a constantly active service that monitors for attacks. If an attack is detected, the solution will automatically respond and try to mitigate the damage.
On-demand DDoS mitigation activates protection only when an attack is detected or requested, offering flexibility but potentially slower response compared to always-on solutions.
Always-on mitigation quality minimizes the latency penalties. It scans the traffic constantly for potential attacks. As it is not dependent on human awareness, this approach reduces the mitigation time.
Customization
Every business has unique needs and risk/ threat profiles. The DDoS mitigation platform should enable you to customize rules based on your workflow and specific requirements.
For instance, your business may not be focusing on Asian markets. So, your website could blacklist user requests in those countries, thereby reducing the attack surface.
Flexibility
Flexibility is also valuable in preventing DDoS attacks. Your solution must be intelligent and flexible enough to start any of the following actions:
- Quickly change rules/ policies based on real-time insights and traffic pattern analysis
- Throw in a CAPTCHA challenge to the user to ensure they are not bots
- Trigger rate-based rules if a user exceeds the pre-set threshold of requests from a single user
DDoS Attack Mitigation Capabilities
DDoS mitigation service comparison should evaluate the vendor’s mitigation capabilities by examining the following questions:
- How quickly can they identify and block an attack?
- How many attacks can they handle simultaneously?
- What protections do they have to prevent attacks from taking down the entire system?
- How will they assist my team in reducing false positives?
Additionally, consider these factors when evaluating an anti-DDoS solution:
- Does the provider offer worldwide coverage?
- Do they have sufficient scrubbing capacity to manage multiple attacks simultaneously?
- How rapidly can they mitigate an attack?
- What kind of reporting and analytics do they provide?
Attack Coverage
Many DDoS attack mitigation software only offers protection against layer 3 and 4 attacks. They require you to subscribe to expensive add-on services to obtain application layer protection.
Neglecting layer 7 DDoS protection exposes you to low-and-slow DDoS and HTTP flood attacks. Modern DDoS protection should detect and protect against all types of DDoS attacks.
Price
Don’t pay for bad traffic. The traffic volume you purchase from a DDoS protection vendor should only be billed on legitimate traffic.
Suppose you pay for all traffic reaching your site, legitimate or attack traffic. When you are DDoS-ed, your infrastructure costs will go up severely. Especially in the case of SMBs, this could greatly impact working capital.
In such a case, you will be paying hundreds of thousands of dollars per attack. To protect from such surcharges, it is vital to have an unmetered DDoS protection model.
SSL Mitigation
Many organizations do not need such attacks to be mitigated. Hence providers may still be acceptable if they do not offer SSL mitigation. However, any organization reliant on SSL-based transactions and traffic will need to know if this capability is supported by a service provider and how.
The DDoS mitigation vendor needs to support in-line decryption and the re-encryption of traffic. This capability ensures that your network keeps the data with intact security policies.
If the mitigation is delegated to a different network, the provider’s decryption and re-encryption process should meet your organization’s goals in terms of service and security.
DDoS Scrubbing Center
Different DDoS attack mitigation providers work with varying capacities across their scrubbing centers, and the overall net capacity across all centers may not accurately reflect the attack mitigation capabilities in the specific geographic region where your data center is situated.
Therefore, when choosing a DDoS mitigation software, it’s crucial to consider the provider’s localized scrubbing center capabilities in your region of interest to ensure effective protection tailored to your operational needs.
Managed Services for DDoS Protection
Security experts available 24×7 is beneficial. So that the security crew can immediately get involved in any attack on your network. If any alert on the attack is received, they will take instant remedial action.
The time saved with immediate assistance can prevent a complete collapse of your network and applications, rendering the attack a minor hiccup.
This guide is based on Indusface’s practical experience in proven DDoS mitigation solutions for different attack scenarios.
If your DDoS protection solution does not have the above-discussed capabilities, it will be ineffective against the latest DDoS attacks. And your IT infrastructure will be left open to highly damaging attacks!
Explore our comprehensive guide comparing features, pros, and cons of leading DDoS mitigation software in the market to help you make an informed decision.
Fully Managed DDoS Mitigation with AppTrana
AppTrana’s managed DDoS Protection offers a comprehensive behavioral-based solution. It uses a multi-layered technique to detect and mitigate DDoS attacks in real time, and it provides real-time monitoring and reporting.
With flexible deployment options, it can protect applications and websites of all sizes. The combination of AI and human intelligence is one of the key features that sets AppTrana apart as a DDoS protection solution.
AppTrana uses AI-based advanced traffic analysis algorithms to detect and identify the source of DDoS attack traffic. It also employs a team of security experts that monitor the network and analyze the data in real time, providing a multi-layered defense.
It provides a comprehensive defense against DDoS attacks and adapts to new and evolving threats, ensuring that the application is always protected.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 June 21, 2024
June 21, 2024



