Key Features of The Best Vulnerability Scanning Tools
Cybersecurity is the most challenging issue facing businesses today. Each year, security breaches cost enterprises millions of dollars. 99% of all security attacks result from faulty misconfigurations and known vulnerabilities. With a myriad of operating system, network, and application-related vulnerabilities, businesses are increasingly realizing the need to assess as well as manage their security risks. This necessitates an efficient approach to protect the enterprises – Vulnerability Scanning with the best vulnerability scanning tools.
What is Vulnerability Scanning?
Vulnerability Scanning is the process of detecting and prioritizing security risks which allows intelligent planning of activities and technologies to manage business risk. It is a common practice across the organization and is often instructed by industry standards and regulations to enhance the security posture.
At the simplest level, vulnerability scanning can be achieved with the use of a vulnerability scanner, the automated tools, which allow you to check if your systems, networks, and apps have any security weakness, which could expose them to a security breach. The top vulnerability scanning tools in the market allow security policy customization, automated vulnerability analysis, and top-notch report for effective communication of vulnerabilities discovered.
How Vulnerability Scanners Secure Your Network?
The foundation of a vulnerability scanner rests upon the vendor’s vulnerability database, which contains details on every known security vulnerability. The security research team of vendors frequently updates the database with information on new vulnerabilities. The vulnerability scanners typically begin by executing a network asset inventory, which gathers information from an existing asset management system and identifies each system running on the network. Then it performs a baseline scan to identify applications and the operating system running on that host to detect possible vulnerabilities.
Once the vulnerability scan completes, the results may overwhelm the security professionals with thousands of configuration flaws. The real power of the top vulnerability scanning tools resides in its capability to support security teams in sorting through the chaos of information and prioritize the actions, which have the highest impact on the company’s security posture. They do this by combining the knowledge about the severity and impact of the discovered security weaknesses, the system’s priority as well as compliance issues if any exist in the given environment.
This vulnerability scanning best practice is what transforms a simple scanner into the best vulnerability management platform. The scanner helps you prioritize the process as per the risk level and suggest remediation to alleviate the risks.
Want to go beyond scanning? Explore the must-have features of a strong SaaS Vulnerability Management Platform to reduce risks effectively.
Benefits of Using the Best Vulnerability Scanning Tools
It is significant to find the best vendor who can give you abundant services as well as cover a wide range of security protection. An organization can get the below benefits through choosing the best vulnerability scanners:
- Identify possible security weaknesses before attackers exploit them
- Define the level of security risks, which exist on the network
- Make an inventory of all the systems in the organization which is mandatory for the planning and future upgrades
- Perform a better assessment on what requires to be fixed
- Constant monitoring saves the business time – When comparing the time company spend on addressing huge risk, which is detected too late, little attention every day can be a great time saver
- As it saves time, it should save business money as well. Yes, it does – the best vulnerability scanner saves you from costly security breaches.
What Are the Types of Vulnerability Scanners?
There are various types of vulnerability scanners and cover off a wide range of attack scenarios with their powerful features. A hacker could enter your network by exploiting web server vulnerabilities or through unpatched software. As such, different attack vectors could be addressed by different vulnerability scanner features and use-cases. It is worth considering the potential risks to your businesses and choose the best vulnerability scanning tools, which are suitable. The three main types of vulnerability scanners are:
- Network-Based Vulnerability Scanners – As its name implies, network-based vulnerability scanners scan the system across the network, by sending inquiries searching for all open services and ports, and then examine each service further to identify known vulnerabilities and configuration weakness.
- Agent-Based Vulnerability Scanners – This type of vulnerability scanning tool involves installing a lightweight scanner on each machine, runs vulnerability scan locally on the device and reports the results back to the server.
- Web Application Vulnerability Scanners – This specialized type of vulnerability scanners focuses on finding security gaps in websites and web applications. Many top vulnerability scanners are purely offering web application scanning while others include this as part of their offerings.
We can also classify the vulnerability scanners into these types:
External vulnerability scanner vs internal vulnerability scanners – External scanners perform the vulnerability scan from outside the network whereas internal scanners aid you to strengthen the security scan from inside of your network.
Unauthenticated vulnerability scans vs authenticated vulnerability scan – Unauthenticated vulnerability scans offer visibility into what a hacker could gain access to without obtaining login credentials whereas authenticated scans perform vulnerability scanning with privileged credentials and dig deeper into your network to detect threats around malware, weak passwords, and configuration issues.
You May Also Read : Penetration Testing vs. Vulnerability Scanning : What’s the Difference?
Key Features of The Best Vulnerability Scanning Tools
Some vulnerability scanners may serve your security requirements better than others based on the features they offer. To equip you with the right view towards the best vulnerability scanners, here we have come up with some critical vulnerability scanner features:
1. Coverage
The core strength and effectiveness of the scanning relies on the breadth and depth of coverage.
- Can it Provide scanning with credentials?
- Can it be customized and guided to include and crawl specific pages and or exclude specific pages from scanning?
- Can it be guided and do more advanced scanning with plugins and feeds and intelligence from manual security assessment?
2. Accuracy
Automated scanners can provide the flexibility to do frequent scans, but does the vendor also include POC (request for Providing proof of evidence) along with their support services so that you can act. This is a huge productivity boost to businesses to ensure, they can get more detailed evidence and false-positive checks when in doubt before assigning the reported vulnerability to a developer to fix.
3. Remediating Reports
Vulnerability scanning reports are vital. They offer a better overview of the security status of your assets and share detailed information about the identified vulnerabilities.
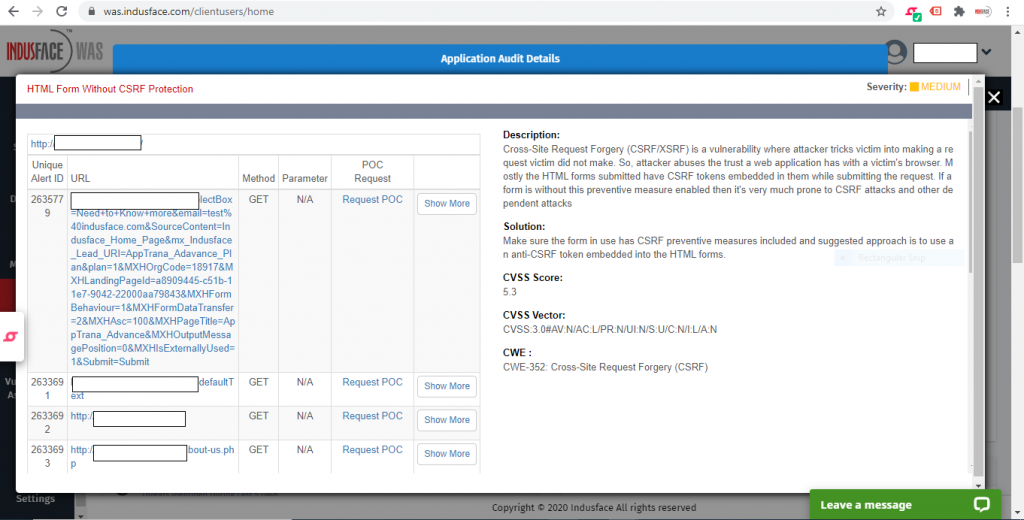
The reporting features highlights how many scans were completed, how many loopholes were identified, and remediation action that you can take to address most of the risks. The reporting feature of the vulnerability scanning tools highlights the following information:
- Total number of scans
- Overall scan summary
- Top 10 vulnerabilities
- Overall system summary
- Security issues by vulnerability
- Security issues by asset
- Recommendations for remediation
With these insights, businesses can continuously work to reduce risk and boost resource utilization.
4. Overall Risk Score
Scanning organizational assets aid businesses to understand where vulnerabilities exist. However, taking action to address them is a difficult balance between risk priorities and existing resources.
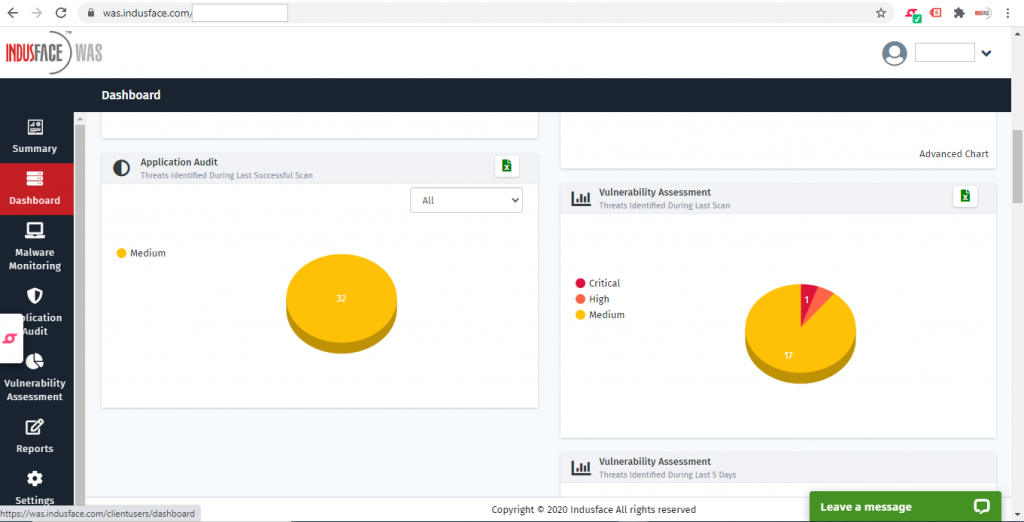
You can leverage the overall risk score feature, which highlights the risk scores as low, medium, and critical for all discovered vulnerabilities. It assigns the risk score based on the volume as well as the severity of the vulnerabilities identified in your applications, networks, and devices.
5. Policy Assessment
Hardening your network has been just as crucial as detecting and fixing vulnerabilities. Vulnerability scanning includes integrated policy, which helps you benchmarking your security posture against industry standards like OWASP Top 10, SANS 25, NIST, WASC, and more. Further, you can also add custom checks to mitigate risks particular to your environment.
6. Advanced Authentication Functionality
While non-authenticated scanning detects expired certificates, backdoors, weak passwords, unpatched software, and poor encryption protocols, some of the top vulnerability scanning tools come with authentication scan functionalities. This module scans the password-protected websites and web applications without recording login macros.
Authenticated scans can help you to identify 2X more vulnerabilities than the regular unauthenticated scans.
To fully capture these vulnerability scanner features, you should invest your time to evaluate the best vulnerability scanning tools out there.
Going Beyond Scanning with Indusface WAS
While leveraging various types of vulnerability scans is vital for mitigating security risks, deep and intelligent vulnerability scanning goes beyond that.
With automated scans and expert’s manual pen-testing, Indusface WAS eliminates the uncertainty and guesswork that false positives bring.
Indusface WAS is a comprehensive DAST Scanner that helps you find application and infrastructure-level vulnerabilities and malware in a single report.
It is the only DAST in the market that comes with salient features like asset discovery, provision for running authenticated scans, a zero false positive guarantee, and 24*7 support.
Experience the maximum benefits of vulnerability scanning features like pre-built policies and templates, real-time monitoring and updates, customizable report, business logic vulnerability checks, and comprehensive coverage.
All together WAS makes vulnerability scanning intuitive and brings light to many sections of progress within your organizational security posture.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 December 15, 2020
December 15, 2020



