Magecart Attack – Techniques, Examples & Preventions
What is a Magecart Attack?
Magecart attacks are a form of digital skimming that targets insecure websites to steal payment information.
These attacks involve injecting malicious JavaScript code into e-commerce websites to steal sensitive information such as credit card details during the checkout process.
The term “Magecart” originates from the attackers’ initial focus on Magento, a popular e-commerce platform, though their methods have since expanded to target various other platforms.
How Does a Magecart Attack Work?
Magecart attacks typically follow a multi-step process:
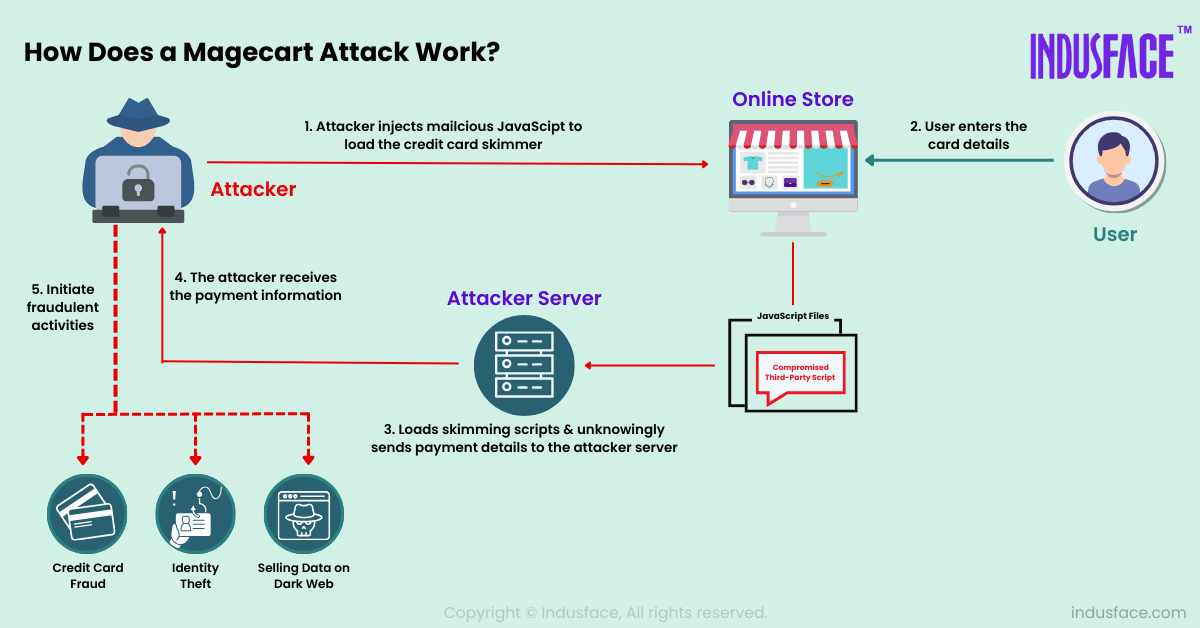
- Vulnerability Exploitation: Attackers identify vulnerabilities in an e-commerce website, such as outdated plugins, weak security configurations, or third-party integrations. They exploit these weaknesses to gain access to the website’s codebase.
- Injection of Malicious Code: Once access is obtained, the attackers inject malicious JavaScript code into the payment or checkout page. This code is designed to capture and exfiltrate payment data entered by customers.
- Data Skimming: As customers enter their payment information, the malicious script skims the data and sends it to a remote server controlled by the attackers. This process is often invisible to both the website owner and the customer.
- Monetization: The stolen data is then used for various nefarious purposes, including selling it on dark web marketplaces or using it for fraudulent transactions.
Techniques Used in Magecart Attacks
Magecart attacks have evolved, with attackers employing various techniques to maximize their success:
Supply Chain Attacks
Supply chain attacks involve compromising third-party services or components integrated into e-commerce websites. Attackers exploit vulnerabilities in these external elements, such as plugins or payment processors, to deploy malicious code across multiple sites that use the compromised service.
Example: The Ticketmaster attack of 2018 involved breaching a third-party chatbot service used on the Ticketmaster website. The attackers injected skimming code through this service, leading to data theft from thousands of customers.
Domain Shadowing
Domain shadowing is a technique where attackers hijack legitimate domains or subdomains to host malicious scripts. This method leverages the trust associated with the primary domain, making it more difficult for security systems to detect the attack.
For instance, attackers might create a subdomain like secure.example.com under a trusted domain and use it to host their skimming code. Since the subdomain appears to be part of a reputable domain, it can evade detection and blend with legitimate content.
Script Obfuscation
Script obfuscation involves altering the appearance of malicious code to make it harder for security tools and analysts to detect. Attackers use techniques such as encoding, encryption, or minification to disguise the true nature of their code.
For example, they might encode JavaScript functions or use complex variable names to obscure the skimming code’s purpose. Some attackers also use dynamic code generation, which creates obfuscated scripts at runtime, further complicating detection efforts.
Data Exfiltration
Data exfiltration is a critical step in Magecart attacks, where stolen information is transferred from the compromised site to the attacker’s server. Attackers set up remote servers to receive the captured payment details and often use encryption or legitimate-looking HTTP requests to hide their communications.
Browser Injection Techniques
Browser injection involves embedding malicious code directly into the web pages that users interact with. This code is designed to capture sensitive information, such as credit card details, as users enter it during the checkout process.
For instance, attackers might inject JavaScript into the payment form on a checkout page, capturing the entered data before it is sent to the legitimate payment processor. In some cases, attackers also hijack user sessions to steal session tokens or cookies.
Since Magecart attacks operate on the client side, they often go undetected by standard web security measures. Consequently, without effective Magecart detection, these attacks can remain unnoticed for extended periods, allowing customers to unknowingly enter their credit card information on a compromised website, exposing their sensitive data to significant risk.
Examples of Magecart Attacks
British Airways (2018)
The British Airways Magecart attack is one of the most damaging incidents. The breach affected around 380,000 customers and led to the theft of payment information, including credit card numbers, expiration dates, and CVV codes.
Attackers injected malicious JavaScript code into the British Airways website and mobile app, targeting the payment page. The code was designed to capture customer payment details as they were entered and send the information to an attacker-controlled server. The breach went undetected for more than two weeks, allowing attackers to collect a large amount of data.
Newegg (2018)
In 2018, the popular electronics retailer Newegg was targeted in a Magecart attack that lasted for over a month. This attack was particularly notable due to the complexity of the malicious code used.
The attackers inserted a skimming script into the Newegg checkout page, which captured payment information as customers entered it. The script was designed to closely mimic legitimate code used by the site, making it difficult to detect. The stolen data was then sent to a domain controlled by the attackers that was cleverly designed to resemble a legitimate Newegg domain.
Forbes Magazine (2019)
In 2019, Magecart targeted the website of Forbes, one of the leading business magazines. Although Forbes is not a traditional e-commerce site, this attack demonstrated that Magecart groups are willing to target various types of websites to harvest sensitive information.
Attackers injected a skimming script into the Forbes website, aiming to capture payment information from subscribers and advertisers. The code was hidden within the site’s legitimate scripts, making it difficult to detect.
Segway Store (2022)
Malwarebytes reported a Magecart attack on Segway, the manufacturer of self-balancing vehicles. The attack potentially exposed up to 600,000 visitors to malicious code embedded in Segway’s web pages. Hackers injected malicious code into the favicon image, making it undetectable by standard security tools.
How To Protect Against Magecart Attack?
Implement Content Security Policy (CSP)
A Content Security Policy (CSP) restricts the sources from which scripts can be executed on a website. By defining a strict CSP, you can prevent unauthorized scripts from running, reducing the risk of malicious code injections. For example, you can whitelist trusted domains and block all others, making it more difficult for attackers to inject malicious code.
Regularly Audit and Update Third-Party Services
Since Magecart attacks often exploit vulnerabilities in third-party services or plugins, it’s crucial to regularly audit and update these components. Ensure that all third-party services are from trusted providers and keep them up to date with the latest security patches.
Magecart detection involves monitoring and analyzing client-side scripts in real-time to identify any unauthorized changes or suspicious behavior.
Monitor for Code Changes
Implement continuous monitoring of your website’s codebase for unauthorized changes. Automated tools can be used to detect any alterations to the JavaScript on your site. By identifying and investigating unexpected code changes quickly, you can detect and remove malicious scripts before they cause significant harm thereby strengthening your Magecart protection.
Use Real-Time Threat Intelligence
Leverage real-time threat intelligence feeds that alert you to new and emerging Magecart-related threats. These services can provide updates on known malicious domains, IP addresses, and scripts associated with Magecart groups, helping you stay ahead of potential attacks.
Deploy Subresource Integrity (SRI)
Subresource Integrity (SRI) is a security feature that ensures the integrity of scripts loaded from third-party sources. By using SRI, you can specify a cryptographic hash that the browser checks before executing a script. If the script has been tampered with, the browser will not execute it, preventing the injection of malicious code and supporting effective Magecart attack mitigation.
Implement Security Scanning Tools
Use web application security scanning tools that can identify vulnerabilities in your site, such as outdated software, weak configurations, or vulnerable third-party components. Regular scanning helps you spot and fix security gaps that could be exploited by Magecart attackers.
How Does AppTrana WAAP Prevent Magecart Attacks?
AppTrana WAAP’s client-side protection is designed to protect websites from Magecart and other client-side attacks by leveraging Content Security Policy (CSP) features. By injecting a CSP header, AppTrana ensures that only authorized JavaScript is executed while blocking all others, effectively preventing malicious script execution and enhancing Magecart protection.
AppTrana enables you to continuously monitor all JavaScript running on your website, providing real-time insights into their origins and behaviors. This detailed visibility helps to quickly detect and block unauthorized or suspicious activities that could indicate a security breach. The solution also provides granular control over script execution, enabling you to block malicious scripts effectively.
By integrating these features, AppTrana WAAP protects your brand reputation and helps maintain compliance with data protection regulations.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 August 23, 2024
August 23, 2024



