Everything About Mobile Application Security Testing
Mobile application security is all set to be a major security headache in the years to come. Take these stats from various industry sources for instance:
- 40% of the companies do not scan their mobile app code for vulnerabilities
- 1 billion personal data records were compromised in 2014 affecting 11.6 million mobile devices
- 95% of the top Android apps were hacked in 2014
- 60% of the mobile malware specifically targeted financial info
With smartphone usage set to reach 1.91 billion globally this year, mobile applications will become more important than ever. It has been estimated that large enterprises will move towards prioritizing apps even over websites, more like what Flipkart has planned for its last year acquisition Myntra.
Logically and technologically, it’s a step forward towards getting closer to the customers and users, who are already using apps fanatically. However, in the absence of any authority or governance on security (apart from submission guidelines from app stores) mobile app security hangs in uncertainty.
Mobile Application Security Risks
Mobile malware and botnets are the top threat, especially for Android. According to a report published in Forbes, 97% of all mobile malware target Android phones, a large chunk of which comes from unregulated app stores. Attackers often replicate or repackage official app store apps to inject malware and then roll it out through third-party sources. That’s exactly what happened with people who were eager to get WhatsApp calling feature and ended up accepting and downloading fraudulent requests for it.
However, Play Store applications do not guarantee absolute security either. Malware is often found on official app store applications that were used for spamming, website attacks, data stealing, and fraudulent purchases. Similarly, attacks on iOS, Windows Phone, and BlackBerry based apps have also increased in recent times. In fact, last year we’ve already talked about presumably the most ‘secure’ sector banking in our post 90% of Mobile Banking Apps Are Vulnerable.
From a business point of view, mobile applications have vulnerabilities that can be exploited to breach into the app server. Simply put, it’s hacking through mobile. When we say that 40% of the companies do not scan their mobile app code for vulnerabilities, it means that the practice puts both the company and its customers at attackers’ mark.
The risks are far greater for public sector institutions and banks that lag behind in-app security testing far more than others. The fact that breaches into such government-associated applications provide direct access to their databases and servers makes things even more serious.
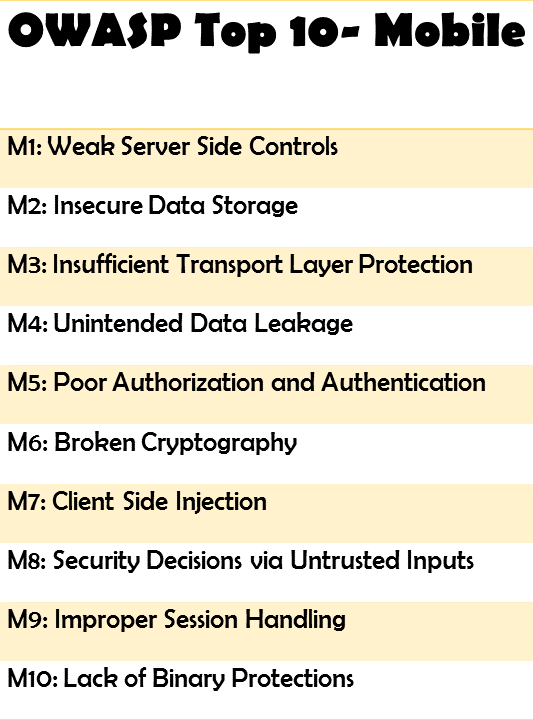
To deal with such risks, the Open Web Application Security Project or OWASP, known for its community contribution in web and mobile app security, has listed top 10 risks and explained how they can be managed to reduce risks. Still, it’s important to find out vulnerabilities in the first place, a task at which most organizations fail.
Developers rarely think that their code can be vulnerable, but with tight deadlines and no security testing standard to comply with, there will be security loopholes at every stage of development. From undesired, insecure permission requests to malware instances, everything needs to be tested at every stage of development.
Solution: Penetration testing or dynamic application security testing for mobile applications with third-party security partners ensures discreet reports on how your app can be breached. This process involves mimicking real-life attack scenarios for thorough security posture analysis especially against OWASP Mobile Top 10.
b) Frequent Updates and No Assessments
How long does the code security last? Is it enough to test mobile applications once? On average, applications are updated once in a month to stay ahead in the competition and roll out the best user experience. However, these updates also bring in new risks that most companies fail to foresee. Every new line of code is a potential risk and should be treated that way only.
Solution: One-time app testing is insufficient. Apps should ideally be tested periodically and after major changes for defense posture against major threats including OWASP Top 10.
c) No or Poor Encryption
Applications do not work on their own, they need to send data and receive data continuously. Eavesdropping or snooping around the information during communication through the internet is one of the most popular breach techniques. Even veteran CISOs overlook the importance of encrypted communication, which leads to sensitive data leakage.
Solution: SSL (Secure Sockets Layer) protocol is currently the stronger cryptography technology securing mobile device and server communication. Get SSL certificate installed if you are not already using it currently to secure web browser communication.
d) Insecure Data Storage
Often developers assume that mobile devices file systems will inaccessible to users or malware. As a result, they assume that storing critical data on the device is harmless. However, in reality, it’s comparatively easier to breach data, especially on weakly encrypted or jail-broken mobile devices. Such a security lapse leads to stolen authentication info, usernames, cookies, passwords.
Solution: An audit through penetration testing or DAST for mobile applications helps analyze the phone memory checking all data stored by the application on a mobile device.
Key Takeaways
- Mobile applications are prone to hacking but most companies never scan them for vulnerabilities
- Even the tested apps can have vulnerabilities after updates
- Dynamic app security testing or pen testing is the only way to ensure protection against OWASP Top 10
- Apps should be tested frequently especially after updates
- Encryption is critical for app-server communication

 April 17, 2015
April 17, 2015