Best Vulnerability Assessment Scanner Online
Hackers are getting smarter; are you?
According to the Open Web Application Security Project (OWASP), a vulnerability is a hole or a weakness in the application, which can be a design flaw or an implementation bug, that allows an attacker to cause harm to the stakeholders of an application.”
While most companies understand what is vulnerability is, there seem to be misunderstandings on what to look for and how to prioritize security.
- 80 – 90% of applications are built from 3rd party components that often contain critical vulnerabilities [ State of Software Supply Chain Report]
- 57% of respondents have no clue whether their applications were ever breached [Ponemon Report]
- Unpatched vulnerabilities were the source of 60 % of data breaches [Ponemon Survey]
- Only 4% of the vulnerabilities are low in severity and business impact [Security Trends & Vulnerabilities Review]
- 18,325 new vulnerabilities and exposures were identified in 2020 [Statista]
The numbers are conclusive. If your business is online, hackers will find these vulnerabilities. Both customers and stockholders do not like hearing about security elapses. Security breaches besides just causing damages and hurting revenues due to down-time also has an intangible and larger impact of hurting reputation of the business and reducing customer trust on the business. These are larger consequences business has to face due to a breach.
Security analysts recommend finding vulnerabilities before the hackers and suggest that you repair issues to avoid exploitations. Here are the guidelines to help you pick the best vulnerability scanner online.
| What | Why |
| 1. Recognize Vulnerabilities | To identify type and impact |
| 2. Follow Scan Methodology | To ensure thorough vulnerability tests |
| 3. Categorize by Severity | To set website priorities |
| 4. Zero-Day Detection | Cover all threats |
| 5. Online Pen Test | For business logic flaws |
| 6. Effective Reporting | To convey issues efficiently |
| 7. Remediation Guidance | To fix issues |
Contents
1 Recognize Vulnerabilities
There are several types of vulnerability detection tools online. Some scans for the top three issues, while others follow a specific list like the OWASP Top 10 or SANS Top 25.
You should look for a online vulnerability scanner that can identify most of the security loopholes that hackers target. This includes the likes of SQL Injection, Cross-Site Scripting, Cross-Site Request Forgery, and other OWASP 10 and SANS 25 weaknesses.
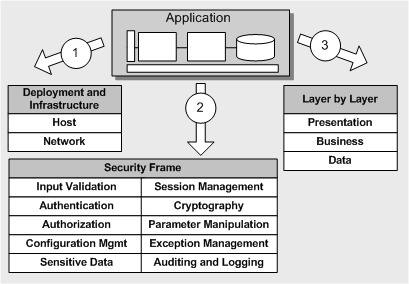
OWASP 10
- Injection
- Broken Authentication and Session Management
- Sensitive Data Exposure
- XML External Entity
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting
- Insecure deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging and Monitoring
SANS 25
Insecure Interaction Between Components
| CWE ID | Name |
| CWE-89 | Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) |
| CWE-78 | Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) |
| CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) |
| CWE-434 | Unrestricted Upload of File with Dangerous Type |
| CWE-352 | Cross-Site Request Forgery (CSRF) |
| CWE-601 | URL Redirection to Untrusted Site (‘Open Redirect’) |
Risky Resource Management
| CWE ID | Name |
| CWE-120 | Buffer Copy without Checking Size of Input (‘Classic Buffer Overflow’) |
| CWE-22 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) |
| CWE-494 | The download of Code Without Integrity Check |
| CWE-829 | Inclusion of Functionality from Untrusted Control Sphere |
| CWE-676 | Use of Potentially Dangerous Function |
| CWE-131 | Incorrect Calculation of Buffer Size |
| CWE-134 | Uncontrolled Format String |
| CWE-190 | Integer Overflow or Wraparound |
Porous Defenses
| CWE ID | Name |
| CWE-306 | Missing Authentication for Critical Function |
| CWE-862 | Missing Authorization |
| CWE-798 | Use of Hard-coded Credentials |
| CWE-311 | Missing Encryption of Sensitive Data |
| CWE-807 | Reliance on Untrusted Inputs in a Security Decision |
| CWE-250 | Execution with Unnecessary Privileges |
| CWE-863 | Incorrect Authorization |
| CWE-732 | Incorrect Permission Assignment for Critical Resource |
| CWE-327 | Use of a Broken or Risky Cryptographic Algorithm |
| CWE-307 | Improper Restriction of Excessive Authentication Attempts |
| CWE-759 | Use of a One-Way Hash without a Salt |
Resource: Cheatsheets OWASP and SANS
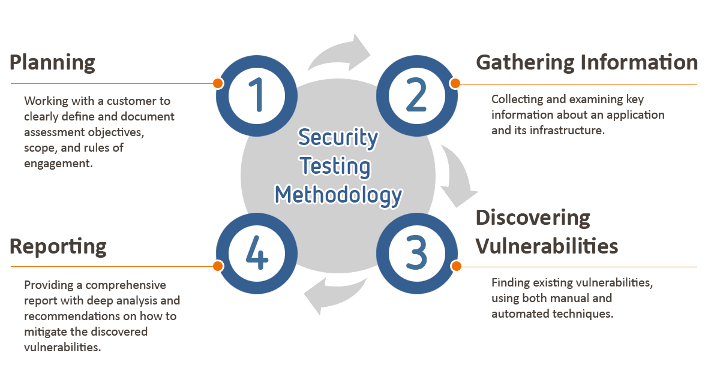
2 Follow Testing Methodology
Whether it is automated, online vulnerability scanning, or manual penetration testing, it is crucial that the vendor follows the standards laid down by leading web application security bodies. It is a complex 12-step process that includes application logic mapping, configuration, and proper documentation before publishing results.
The following diagram will serve as the context based on which you can educate a business to take more proactive steps for security
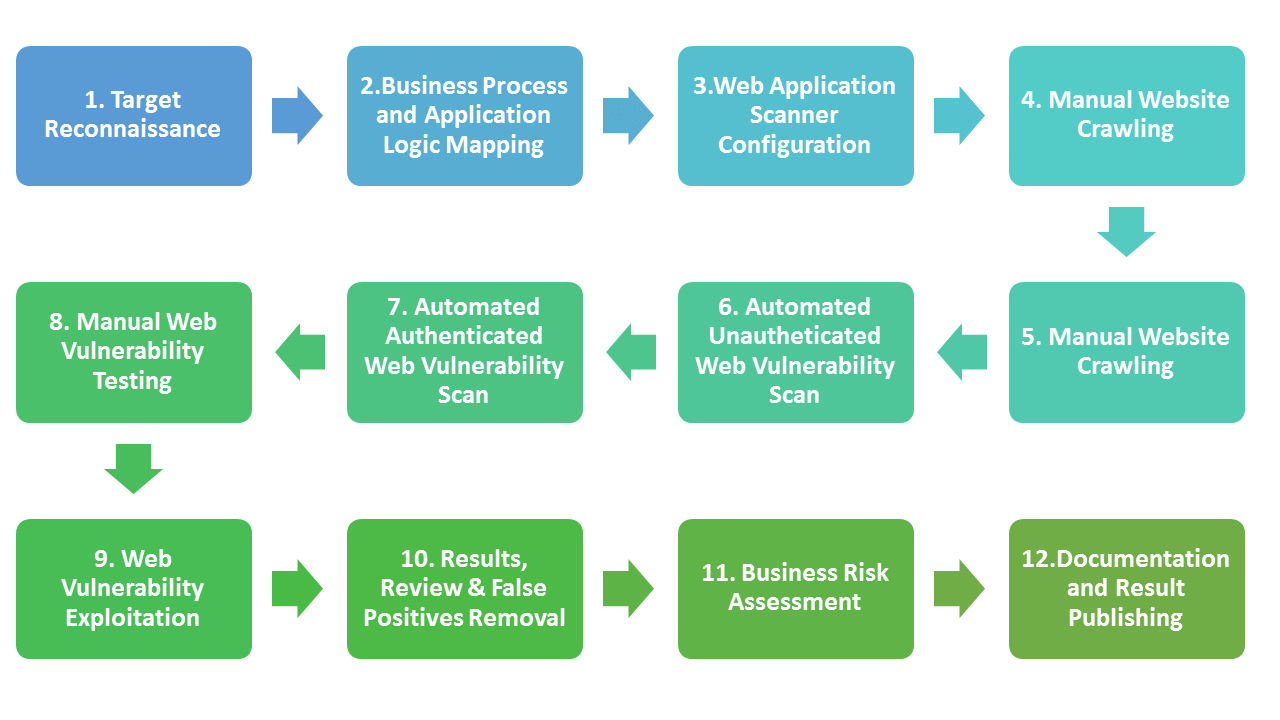
3 Categorize by Vulnerability Severity
The most important application security metric that everyone should have. Independent of using automated vulnerability scanning tools, penetration testing/ethical hacking, or a hybrid combination of both being used the report should highlight the risk in detail.
A more comprehensive view of these vulnerabilities will also emphasize the risk severity and business risks of each vulnerability.
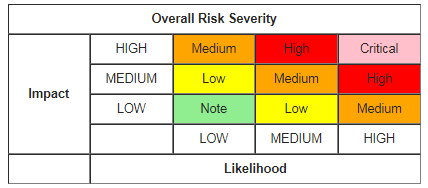
It will help your business to prioritize what’s more critical and what should be fixed first.
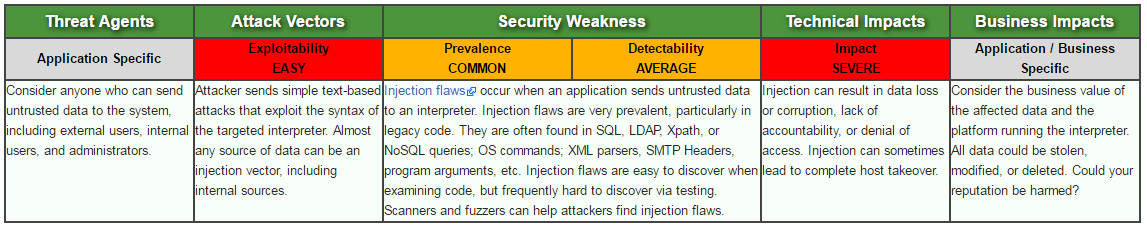
Your online vulnerability scanner should be able to discover vulnerabilities based on the business impact.
4 Zero-Day Detection
A zero-day vulnerability is a disclosed weakness in a software that is unknown to the party or parties responsible for patching or otherwise fixing the flaw.
Most vulnerability scanning tools are not efficient to look for new vulnerabilities. They often will run on code and logic wrote years ago. Hence it is imperative to find a security assessment vendor who in their offering not only reports zero-day issues but also quickly updates their signatures and policies to find them in their assessment (Both automated and manual) and back it up with 24×7 support team to help answer queries around these new threat vectors.
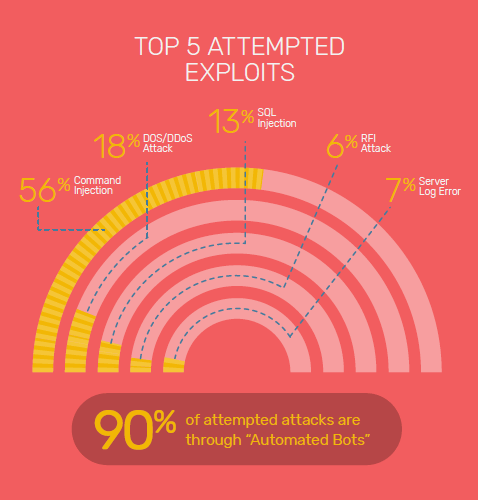
5 Pen Testing
Any serious web application would need a combination of regular automated test and periodic manual assessment for enhancing their security posture. While automated vulnerability scanning tools are quick in uncovering common issues, you will also need periodic penetration testing to ensure that business logic issues are also detected.
Often applications have security gaps that are exclusive to their business. The following are some notable examples.
-An e-commerce site allows users to add items to cart, view a summary page and then pay. What if they could go back to the summary page, maintaining their same valid session and inject a lower cost for an item and complete the payment transaction?
-Can a user hold an item infinitely in the shopping cart and keep others from purchasing it?
-Can a user lock an item in a shopping cart at a discounted price and purchase it after several months?
-What if a user books an item through a loyalty account and gets loyalty points but cancels before the transaction could be completed?
Ensure that your online vulnerability scanner provider uses a pen testing team that can help you out when needed.
6 Effective Reporting
Simply publishing the vulnerabilities found during scanning is not the best way to conduct reporting. Often business managers and developers look for insightful reports that lay down the essential points and help them to understand what’s wrong and what the risk is.
An ideal web scanning report should include the following points:
- Number of vulnerabilities
- Types of vulnerabilities
- Criticality of vulnerabilities
- Business impact
- Observations from the tester
- Analysis
7 Remediation Guidance
Efficient scanning companies do more than state the problem; they offer detailed suggestions on how vulnerabilities can be mitigated. For instance, AppTrana has an end-to-end remediation workflow function integrated with all its scans. Security analysts thus send their mitigation guidelines to developers.
Instant Protection with Indusface
It’s vital to look at other mitigation options such as a Web Application Firewall to virtually patch vulnerabilities to evade hackers from exploiting them.
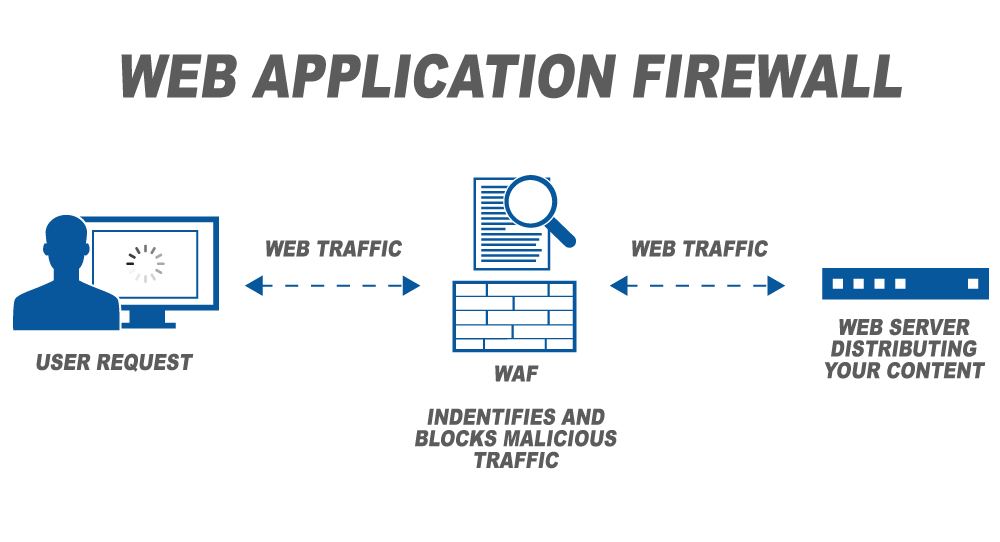
The tightly-integrated WAF and vulnerability scanner modules ensure that there is constant learning which is shared across both, improving the efficacy of detection & protection for all types of attacks. Look for application scanning vendors that offer integrated plans such as Scanning + WAF as your security needs grow.
Found this article interesting? Follow Indusface on Facebook, Twitter, and LinkedIn to read more exclusive content we post.


 May 7, 2018
May 7, 2018




