Open Source Code Vulnerabilities
The open-source community influences our lives in more ways than we think. It is believed that such programs power more than 60% of the total websites available today, a figure that’ll grow in the coming years.
Although open-source development might look like a new trend where programmers give away source codes for the greater good, the practice has been into existence long before the days of the internet.
But clearly, the internet built the never-seen-before communication channels across the world, inviting everyone with skill and knowledge to be a part of their creation.
Why Everyone Loves the Open Source?
From the consumers’ point of view, it is the perfect way to get functional and useful programs that otherwise cost a lot of yearly licensing money. Take an example of the difference between the Microsoft Office and its open-source alternative the Open Office.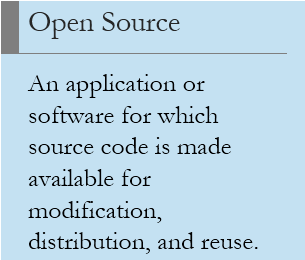
On the other hand, organizations, businesses, and governments are increasingly opening up to open source applications for diversity, simplified solutions, and cost-efficiency. While the general understanding does not go beyond server-based applications like MySQL and Apache, there is a huge world of available options.
Industry experts say that the Open Source Era has a huge potential to grow from a business’ point of view and it will soon be powering almost every big company by the end of this year. Powered by the cloud, SaaS, and mobile, organizations will find it easier to work on preexisting codes and molding it according to requirements rather than starting from scratch.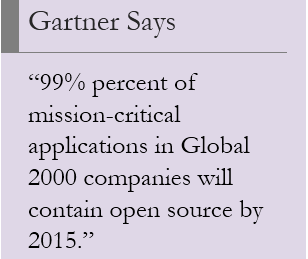
Wendy Nather, from 451 Research, talks of the open-source as a building material. He says that it provides a competitive edge to enterprises that want to bring blocks together using the cloud in forms of Platform-as-a-Service (PaaS) Infrastructure-as-a-service (IaaS) without spending a fortune on licenses for a myriad of web applications.
Open Source Security Concerns
Although there is no doubt that open source web applications are efficient and economical, organizations cannot shy away from the fact that such application comes with a myriad of vulnerabilities that often go unnoticed. Further in the absence of a license and service level agreement, support, update, maintenance, and documentation for use is minimal.
- Multiple vulnerability issues
- No update or patch guarantee
- Minimal support
- Absent SLA
In fact, companies pick chunks of codes from the open-source and then maneuver the application for the desired functionality, which leaves room for several loopholes when not backed by proper auditing. In fact, the Open Web Application Security Project (OWASP) top 10 list has a special slot for it named ‘Using Components with Known Vulnerability’, which perfectly covers the open-source exploitation risks.
Though enterprises think that input from several developers equals better security, known vulnerabilities in the popular application will make them reconsider the perception.
Apache Tomcat and Apache Hadoop are the known offenders of log forging and cross-site scripting. Similarly, the Zen Cart, WordPress, and phpMyAdmin have also had frequent cross-site scripting issues in the past.
At the same time, it’s not easy to find out vulnerabilities on open source projects due to the shared nature. Both in-house and open-source coders are more curious about fixing UI and UX bugs due to their inclination towards improving the functionality of apps rather than digging deep into the security factor. Additionally, with shorter turnaround times and frequent changes, things don’t get any easier.
3 Ways to Secure Open Source Usage
Insecure web applications can lead to catastrophic effects, not just in terms of money but also in business processes and brand image. Exploitation and data breach information get viral, making prospects and customers question the entire security structure of an organization.
So, what is the solution then? For one, restrict open source code usage entirely, but given that it’s not very logical, businesses and government should sweat on their open-source acceptance and management policies. Developing a strong open source usage policy backed by app security testing is the only possible solution, which has been explained in the following points.
1) Identify Vulnerabilities
Whether you’ve built an entirely new application or have to use unknown components in it, a web application scanner can prove to be handy to highlight vulnerabilities. It is basically an automated tool that looks for security loopholes and reports it to the admin.
In fact, security vendors also provide more advanced options backed by human intelligence to penetrate the application manually. It’s called dynamic application testing (DAST) and is specifically designed to audit web applications with real-attacker-like actions. Such services might also include business logic vulnerability detection within the app, which cannot be detected through automated tools.
2) Define Adoption Policies
Organizations of all sizes should work on policies that can define the adoption and usage of open source web applications and their components. It takes management and development teams’ inputs and strong adherence to ensure that rules are followed at every level of the organization.
Further, to make sure that such policies do not pull down the development process, work on every step as a part of the process. You can even make a list of approved component sources and keep a track of them during the complete development cycle.
3) Patch Proactively
Finding vulnerabilities is simply knowing your risks. In no way, it will make your secure unless you code the patches for them. However, developing patches remains to be a major thorn in the flesh for most companies as our research shows that organizations take more than 30 days to develop a patch for the single reported vulnerability on an average. During this period, websites remain open to data breaches, defacement, manipulation, resource misuse, and other kinds of threats.
Understandably, businesses have to look after other important matters, rather than sending every developer to bug-fix race.
A much smarter policy would be to patch vulnerabilities virtually in real-time with a web application firewall. It’s different from network layer firewalls and has especially been designed to shield vulnerabilities from attacks without any code changes.
Organizations have accepted it as the next layer of defense, which when fully managed through security analysts can even fix business logic flaws and limit attacks on the basis of acceptable user behavior policies.
Conclusion: Open Source Smartly
In the years to come, open-source web application components are expected to save billions to organizations across the world. It has undeniably grown synonymous with efficiency and adaptability, but only when the risks are evaluated and managed intelligently. Open-source security is eventually based on steps that you take to protect application structure from vulnerabilities and also the ability to mitigate attack attempts if somehow these vulnerabilities cannot be patched immediately.


 May 14, 2015
May 14, 2015



