March 28, 2014
March 28, 2014 5 min Read
5 min ReadOffline, yet still exploited
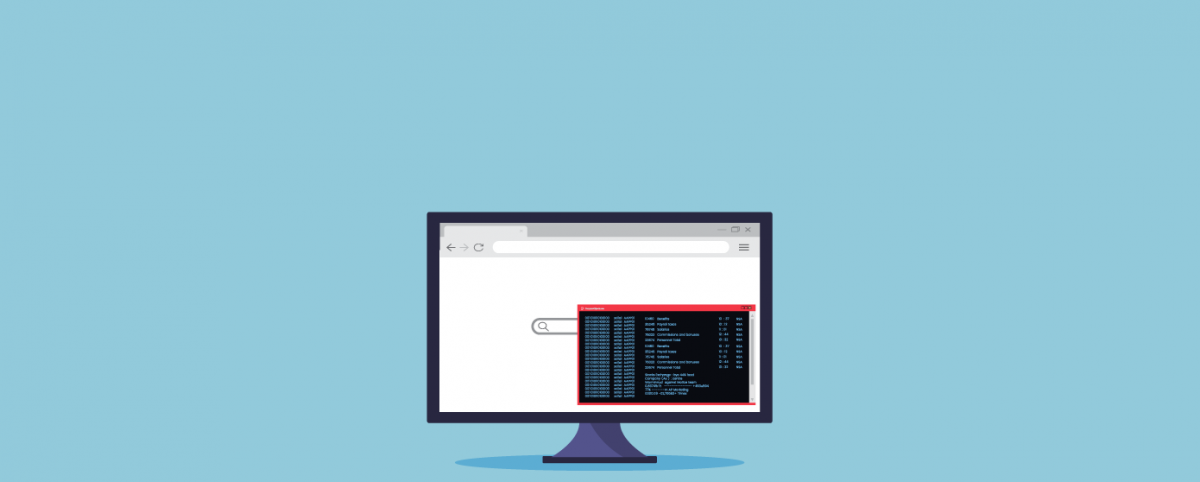
The Hacker Series By Bhaumik Merchant, Information Security Research Consultant, Indusface Introduction: This article demonstrates a unique kind of communication technique between an attacker machine and a victim machine during.