Poor Firewall Implementations Pave Wave for DDoS Attacks
Organizations often tend to heavily and exclusively rely on firewalls, load balancers, and VPNs, among others, to prevent DDoS attacks, secure their mission-critical assets, and protect their IT infrastructure. But attacks have become more lethal and severe; attackers have modernized their attack methods and leveraged the best-in-class technology to orchestrate distributed denial of service attacks. Firewalls are known to have vulnerabilities, especially those arising from implementation failures, that render them ineffective in protecting the application and make them easy DDoS targets for threat actors.
So, what are these implementation flaws that make firewalls susceptible to DDoS attacks? What can organizations do to fortify their security posture and effectively prevent these attacks? Read on to find out.
What is a Firewall?
A firewall is a hardware or software-based system that secures the assets of a private network against unauthorized access by users from external networks. They are placed on the network gateway or perimeter, examining all incoming and outgoing packets, and filtering out those that don’t meet security policies. They lack flexibility, scalability, agility, and transparency. They can only secure local area networks from unauthorized access and are ineffective against advanced threats.
On the other hand, next-gen WAFs are positioned between the users and the web application to scrutinize, monitor, and filter all requests to the server. This is especially useful in the age of cloud computing and IoT when the networks do not have fixed, rigid boundaries. WAFs analyze all HTTP communications to decide whether to allow, block, flag, or challenge each request. Malicious requests are filtered out before they reach the server, and the application stays protected and available.
Next-gen WAFs also leverage the latest technology, including self-learning AI systems and analytics, and infuse greater accuracy, flexibility, agility, and transparency into the equation. So, WAFs are better equipped to stop zero-day threats, application-layer DDoS attacks, and a wide range of modern-day advanced threats.
How Does Poor Firewall Implementation Pave Way for DDoS?
1. Weaknesses in TCP Implementation in the Firewall
Attackers leverage the poor implementation of TCP protocols in the firewall to orchestrate reflected amplification DDoS attacks. Traditionally, amplification attacks use the connectionless nature of the UDP protocols to overwhelm targeted servers (which are usually open, misconfigured ones) with numerous spoofed requests/ packets, rendering the server inaccessible. They use UDP protocols mainly owing to the challenges and complications created by the three-way handshake required by the TCP protocol to establish TCP/IP connections over the IP-based network.
However, many firewalls do not always conform to these TCP standards and are prone to poor implementations, thus, paving the way to reflected amplification attacks.
One kind of bad TCP implementation is the way in which sessions are established. Usually, the destination host sends an SYN request to the TCP host that responds with an SYN/ACK and waits for an ACK response from the client. Threat actors flood the TCP host with session requests but don’t return the ACK responses. This leads to what is called an SYN Flood.
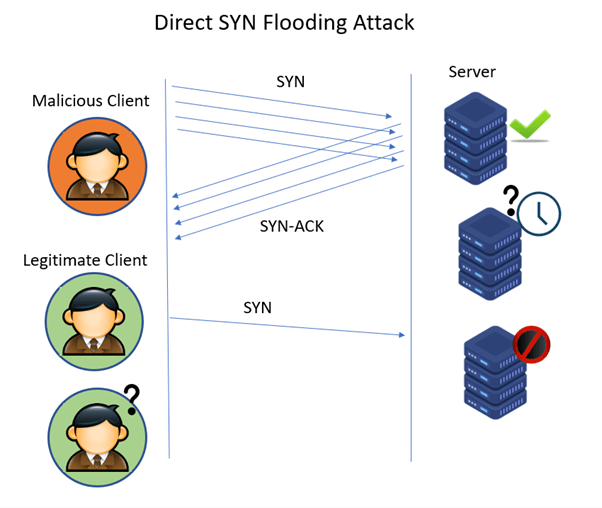
With these massive numbers of incomplete sessions open, the host’s buffers are filled, and it cannot accept new session requests from legitimate users, leading to a denial of service.
2. Use of Only Stateful Inspection
Traditional firewalls inspect the network traffic using Stateful Packet Inspection, understand the risks from the incoming traffic, and make decisions on whether to allow resource requests. While everything within the data packets is inspected and risks identified, stateful solutions do not look at other important parameters such as the source, destination, etc., based on predefined rules.
So, malicious actors could trick the firewall into responding to spoofed censored requests even without a valid TCP handshake and return large block pages. They also do not offer full visibility into the DDoS traffic and do not integrate and communicate well with other cloud-based solutions to stop attacks.
3. All Traffic is Routed Through the Firewall
The firewall itself can be exhausted by protocol and volumetric attacks if all traffic flows through it. Most modern DDoS services back the firewall with Content Delivery Networks (CDNs). CDNs, given their global network of edge servers, are capable of seamlessly handling thundering herd surges in traffic without overwhelming the origin server or the firewall with voluminous requests to process. Only requests for un-cached content are routed to the origin server through the firewall.
4. Improper Activation of Controls
When organizations do not activate security controls or do it improperly, they tend to erode firewall security and make the application susceptible to DDoS attacks. For instance, not turning on anti-spoofing controls in the security solution will open the application to various threats, including DDoS, malware, etc.
Other Firewall Implementation Failures
- Missing/ incorrect firewall policies
- Outdated firewall software
- Using a firewall security solution that is incompatible with the tech stack
- Unnecessary ports, features, and services available on the firewall
Conclusion
To ensure your application is always available, you must choose a next-gen, managed WAF solution like AppTrana that is easy to deploy and provides robust security against DDoS and a whole host of threats.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 July 12, 2022
July 12, 2022



