Lessons from Poor Vulnerability Protection by Silicon Valley Companies
In recent months, data breach stories concerning Silicon Valley companies have dominated the new- so what can you learn from these businesses?
Poor standards of vulnerability protection affect more than just the core business. It impacts customers, employees, clients, vendors, and the entire reputation of the company. Additionally, when the news goes public, companies could be looking at millions in settlement costs. Here are some of the numbers from the Ponemon Institute and Net Diligence report that you should consider:
- $574,984: Average cost of defense of a data breach lawsuit
- $258,099: Average settlement for a data breach lawsuit
- $3,324,959: Average lost business costs per breach
- $5.85 million: Average cost per data breach for U.S. company
- $509,237: Average notification cost per breach
![]()
Let’s review some of the major data breaches and see what you can learn from their mistakes to improve vulnerability protection on your business’s website.
Uber Breach- Untested Open Source Code
In 2016, a 20-year-old Florida man successfully breached the Uber servers and stole the personal data of 57 million users, including 600,000 drivers in the United States. What did Uber do when they came to know about the breach? They paid the hacker $100,000 to delete the information, which he did not.
The breach was officially confirmed in 2017, for which Uber was heavily fined by the court being in violation of multiple breach notification laws. [You can read details of the breach here].
However, this data breach at Uber technologies Inc. contains a lesson for every company – big or small. Developers will use third-party code, repositories and other services, but it is critical to test this code for vulnerabilities before the release.
If developers are using third-party APIs, open source code, and code repositories, test the application systems (backend/frontend servers, APIs, etc.) after every release and update. This may help to prevent a hack.
Equifax & Alteryx: Backdoor Entries
The Equifax and Alteryx breaches were the biggest stories of 2017, affecting over 260 million US consumers. In total, there were 248 different data fields for each household, according to the researcher who uncovered the leaked data this week, which included names, addresses, hobbies, interests, ethnicity, income, and even mortgage rates.
While the official statements led us to believe that hacks were a result of brute force attacks, security experts believe otherwise. According to security investigators, attackers found a backdoor exploiting a security vulnerability in one of its online applications and exploited it to install 30 web-shells, which gave hackers unrestricted access to the database.
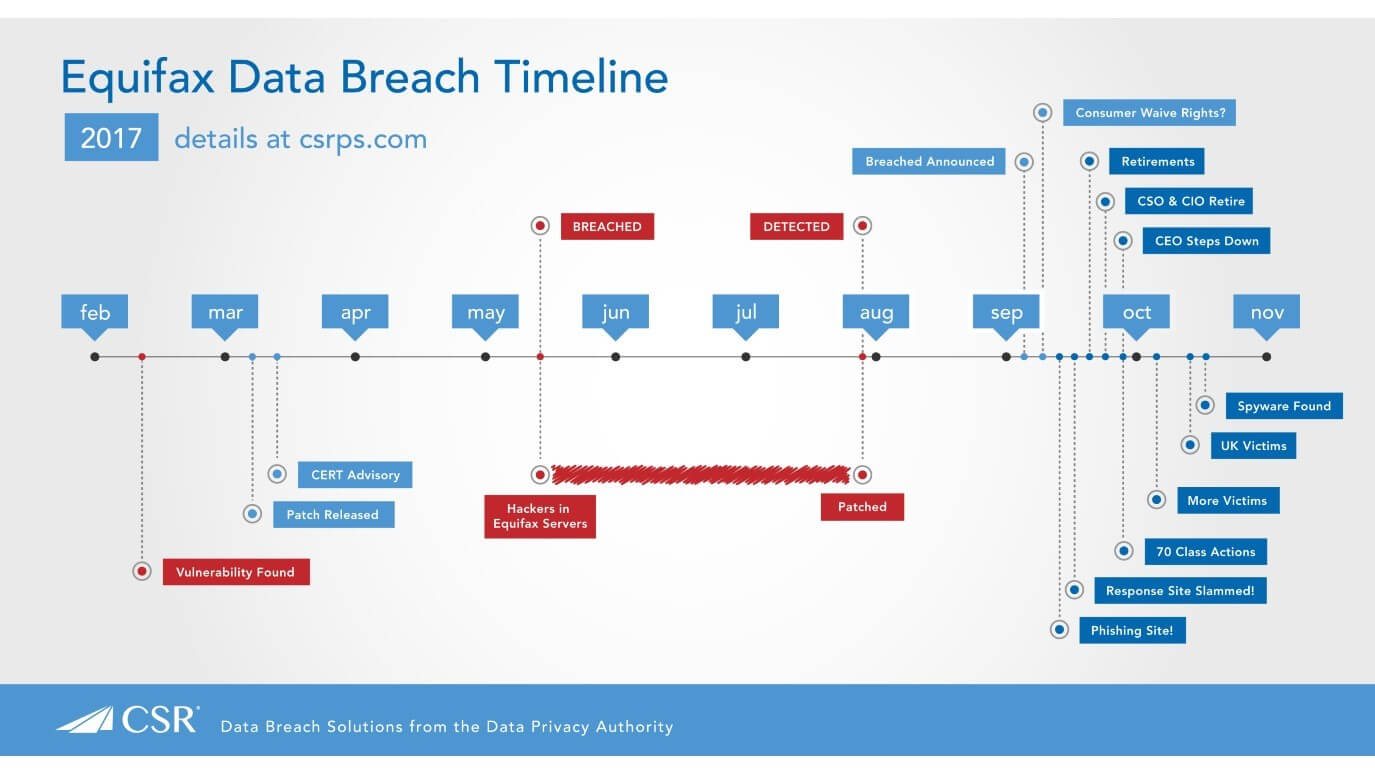
What could have prevented the hack: In a bid to rapidly grow the company, CEO Richard Smith had acquired over 20 companies while expanding to 25 countries. With thousands of applications catering to consumer needs, companies like Equifax and Alteryx need manual penetration testing that can understand business flow and test accordingly.
Yahoo: Top Management Involvement
There never has been a more massive breach than Yahoo. Over 3 billion accounts were affected over the span of four years; and the company failed to learn. The company disclosed that over 1 billion accounts were hacked back in 2013 and yet top management did not know about it until recently.
Security researchers concluded that most of the breaches at Yahoo happened due to SQL Injection (SQLi) vulnerability. SQLi is one of the most common vulnerabilities and could have been detected and patched from the beginning highlighting a communication gap between the security team and top management.
CEO-level engagement is essential in all cybersecurity concerns. Top management should actively understand risks and how security teams are managing them. A weekly overview report of the security posture is advisable. All this could be used to prevent future hacks at Yahoo.
Vulnerability Detection, Protection, and Monitoring
Organizations looking for comprehensive application security need to not only consider identifying vulnerabilities in web applications and APIs but also protect against the attack vectors. Here are some pointers that will help you improve application security.
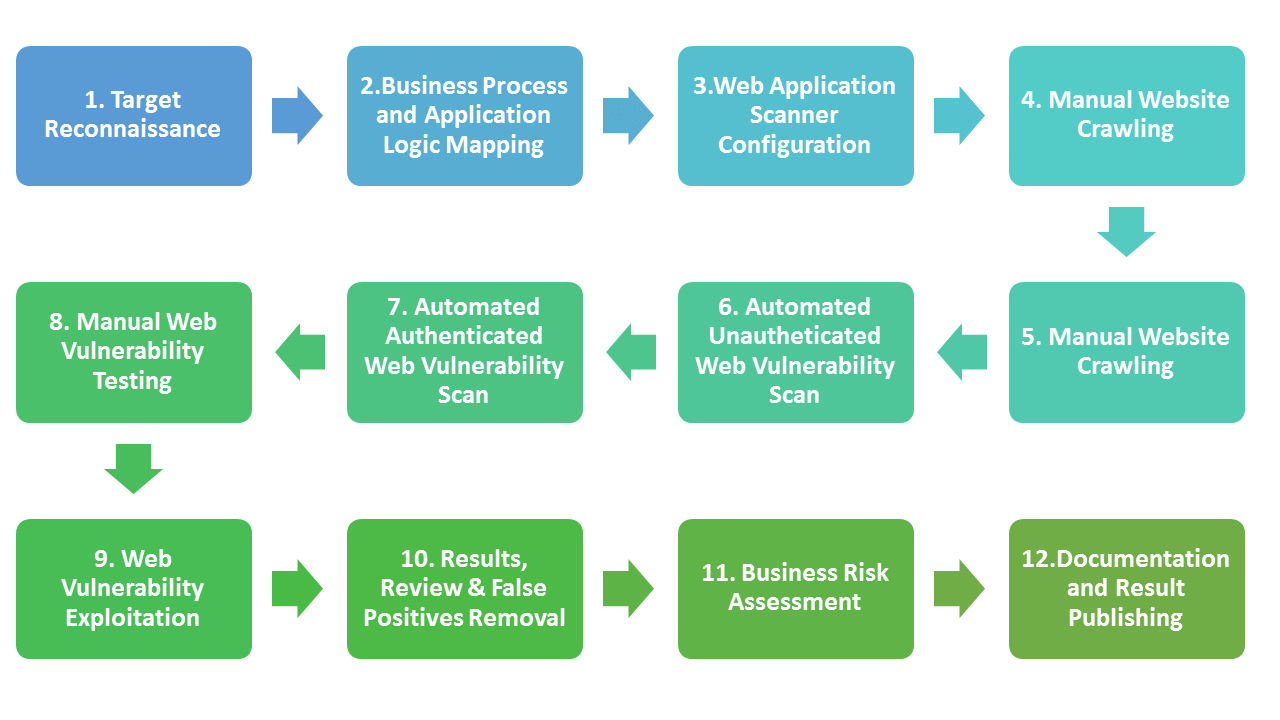
- Sign up for the latest security notification from your vendor to protect your applications from known vulnerabilities.
- Conduct penetration tests on a quarterly basis. Start for free here
- Organizations need to conduct business logic tests on all applications. If expertise is not available, AppTrana offers a complete end-to-end solution to protect your website and applications from vulnerabilities, 0-day threats, and automated application attacks. Specific WAF rules can be created to not only block attacks (via virtual patching) but can also track malicious behavior.
- Send weekly security reports to the top management. You get a free test and report on any of your websites here.
- Sometimes it’s prudent to track the malicious behavior of an attacker initially versus simply blocking the attack. Gathering information such as IP address, User ID if authenticated, GEO location, navigation/user behavior, and machine fingerprint can help gain intel about the attacker’s methodologies so that you can use that information to create more aggressive blocking rules from these attackers.


 February 2, 2018
February 2, 2018



