Preventing WAF Bypass: How AppTrana Protects Origin Servers with Resilient Architecture
A recent discovery by Zafran.io reveals critical vulnerabilities in web application firewalls (WAFs) from providers like Akamai and Cloudflare.
Misconfigured origin validation allows attackers to bypass WAF protections and directly access backend servers, creating opportunities for data breaches, DDoS attacks, and more.
While most WAF vendors offer IP whitelisting as a solution, implementing it presents significant challenges such as:
- Extensive and Dynamic IP Lists – Many WAF vendors also serve as CDN providers, leading to vast and frequently changing IP lists for customers to whitelist. This complexity increases the likelihood of errors and creates a maintenance burden.
- Operational Complexity – Whitelisting ties customers to the WAF vendor’s architecture. In emergencies requiring WAF bypass, the customer must undo and reconfigure the whitelisting—a time-intensive process that can delay response and increase exposure to attacks.
- Whitelist Bypass Risks – For vendors like Cloudflare, which also provide workers, IP whitelisting may not be a secure option. Attackers could exploit workers to launch attacks, bypassing the whitelisting. In such cases, customers must exercise extra caution and consider alternative validation methods, such as header validation. However, this approach is more complex to implement and still less secure.
How AppTrana Ensures Origin Server Protection
At Indusface, we’ve addressed these issues head-on with AppTrana, a platform designed to eliminate the risks of misconfiguration while maintaining security and ease of operation:
1. Mandatory Origin Server Protection
AppTrana incorporates origin server protection into the onboarding process. All traffic to the backend is restricted to a whitelisted, controlled IP pool, minimizing the chance of exposure due to dynamic IP lists or manual errors.
2. Dual-Layer Architecture for Simplified Security
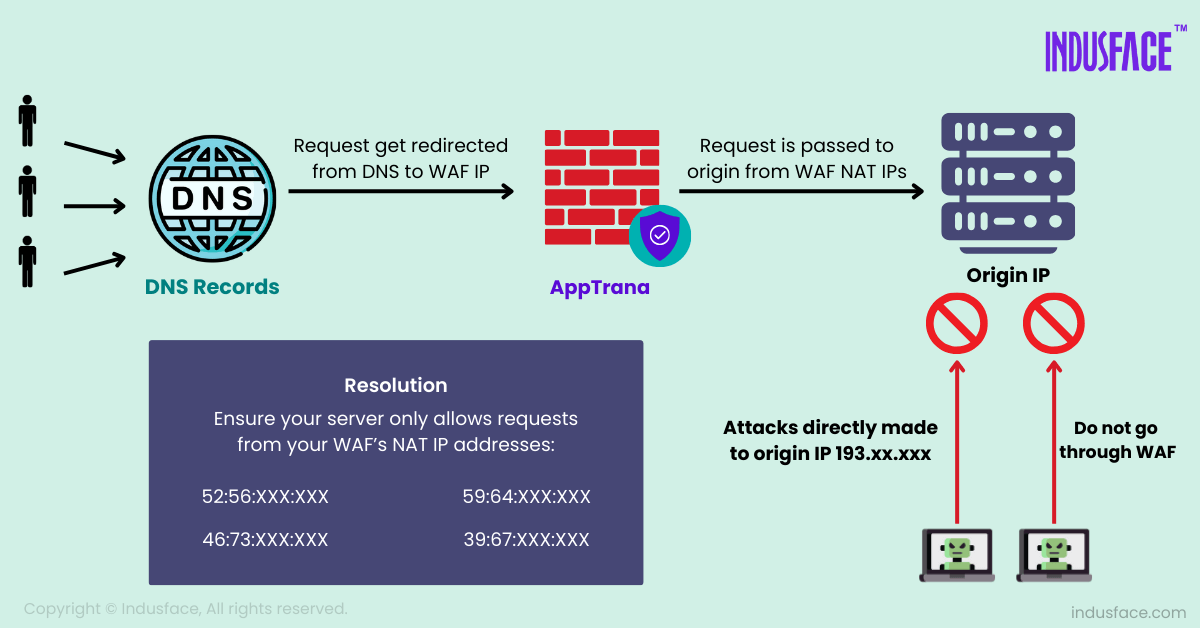
Unlike providers combining CDN and WAF into one layer, AppTrana’s two-layer architecture separates these functionalities. This simplifies origin server validation and reduces operational complexity, ensuring only secure traffic flows between the WAF and the backend server.
3. “Design for Failure” Philosophy
By adhering to the “design for failure” principle, AppTrana ensures resilience and high availability, even in adverse conditions. Its bypass fleet provides an additional layer of reliability during emergencies.
When the WAF is bypassed, traffic is still routed through the same trusted IPs, ensuring security and continuity. This eliminates the need for customers to undo whitelisting during crises, resolving a key operational challenge faced by other WAF providers.
Its built-in safeguards ensure customers remain protected against vulnerabilities highlighted by Zafran.io.
Why AppTrana Stands Out
The WAF bypass vulnerabilities revealed by Zafran.io show that even top-tier providers fail to adequately address origin server misconfigurations. AppTrana’s proactive design, mandatory safeguards, and streamlined architecture eliminate these risks, ensuring robust protection for all customers.
For many WAF providers, origin server protection is offered as an add-on feature, requiring additional configuration and costs. AppTrana includes this protection by default in all its plans. This ensures every customer benefits from robust security without any extra effort or investment.
Conclusion
The challenges of implementing IP whitelisting and maintaining origin server protection are common when using a single provider for CDN and WAF. With AppTrana, Indusface delivers a solution that overcomes these hurdles, providing reliable, easy-to-manage protection against direct to origin attacks.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 December 10, 2024
December 10, 2024






