How to Secure WordPress Website from Hackers?
Today, 21 million websites use the top 20 Content Management Systems (CMS) with access to more than 67 thousand free plugins. WordPress is by far the most popular content management system with 51% of the market share according to the BuiltWithTrends.
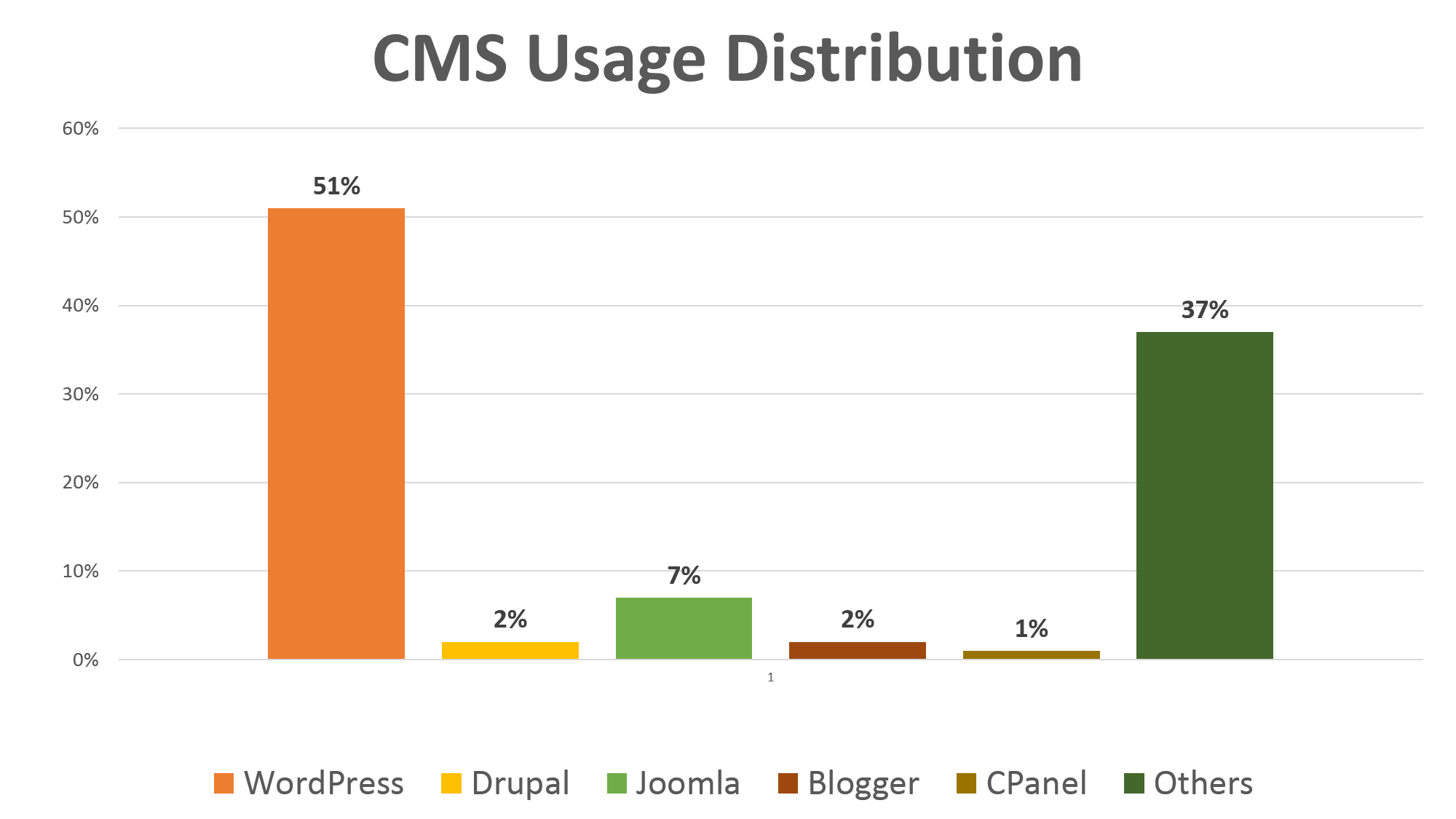
Are these CMS secure for businesses dealing with customer credentials and financial transactions? We’ll get to that after understanding what a CMS essentially does.
What is a Content Management System?
A content management system is a group or suite of applications that allows adding, updating, and publishing digital content. It is your structured tool to change the website design, update product details, upload images or videos, and to make the other changes.
A few decades ago, businesses had to build websites from scratch without design templates or apps. And for content management, they rely on the developers for updating the HTML every time there was a change.
Public or open-source or free CMS such as WordPress and Drupal revolutionized how websites were created and managed. They allow businesses to control the website without having to write the code for simple functions such as updating the product description. Anyone from the marketing or sales team can do it today.
And for custom application requirements, they can use the free plugin apps or ask the development team to create a new one and upload it to the CMS. Simple
Inherent Vulnerabilities in the Content Management Systems
According to Data Breach Today, 800,000 banking credentials were stolen using hacked WordPress sites in 2014. On November 20, the same year, WordPress pushed a security patch for Cross-Site Scripting (XSS) vulnerabilities.
Similarly, just four months ago, attackers exploited a 2-year old SQL Injection vulnerability in Drupal. They installed web-based ransomware and hijacked website admin accounts using CVE-2014-3704, which was patched later by Drupal.
While CMS is widely used, it is widely exploited too.
Since the open-source community manages these CMS, one cannot trace the origin of the code and what vulnerabilities it might have.
Even if you find the vulnerability using automated scanning or penetration testing, there is no way you can push WordPress or Drupal to patch it in the system. So essentially, one can only pray that their site isn’t hacked until the CMS is fixed.
On average, WordPress, Drupal, and Joomla release security patches in 42, 51, and 36 days respectively. That’s the average number of days websites are vulnerable to exploits if the vulnerability is known. For other vulnerabilities for which the commercial exploit is not announced, creating and deploying patches can take months.
Security Vulnerabilities in Third-Party Apps
Moreover, three major CMS offers 70,000+ plugins available today, which anyone can upload or download.
Since WordPress hosts the maximum number of third-party apps (40,000), let’s find out what it takes to write code for new apps and upload them to the CMS.
- -Zero publishing fee
- -Zero security checks
- -Basic API
- -Supports PHP
Basically, anyone who knows how to code can add a plugin to the WordPress architecture and we have no idea where the code came from.
The Open Web Application Security Project (OWASP) A9 gives a general idea of this security loophole with plugins. A9 represents ‘Using Known Vulnerable Components’.
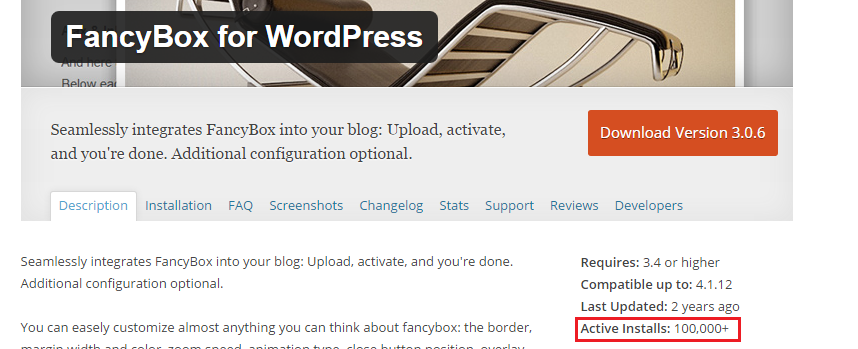
So, if a plugin ‘FancyBox for WordPress’ is vulnerable to SQL Injection, all the websites using this plugin will be vulnerable, which in this case is over 100,000 websites.
Checkmarx ran automated tests on WordPress plugins a few years ago and found out that 20% of all plugins were vulnerable and open to attacks like SQL Injection. Moreover, seven out of the top 10 plugins were vulnerable to application attacks.
This means that every website using these plugins will be open to attacks too.
Is exploiting these vulnerabilities difficult?
A simple ‘View Source’ will tell you the plugins a website is using on their CMS. If one of the plugins is vulnerable, hackers can use it to exploit the website.
For larger automated attacks, hackers first find vulnerabilities in a plugin and then find millions of sites using that particular third-party app.
Securing Your CMS Independently
Unknown code components, third-party applications, and delays in security patches make public CMS vulnerable to several kinds of application attacks.
Although finding vulnerabilities is the first step towards security, you can never patch it since your developers don’t own the CMS or the plugin. Even with deep penetration testing, you will only be looking at the vulnerabilities without any fixes. That is where IndusfaceTotal Application Security helps you. It can find the vulnerabilities and patch them virtually.
A virtual patch means that you do not have to change anything in the app code but a WAF applies a specific policy or rule that doesn’t allow attackers to exploit that particular vulnerability. It is like automating attack mitigation without updating the software.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 November 10, 2016
November 10, 2016



