SIEM Integration on the Indusface WAS
Indusface WAS integrates with all major Security Information & Event Management (SIEM) providers that integrate with Amazon S3.
With this integration, you can push logs from Indusface WAS into leading SIEM providers like SumoLogic, RSA, Splunk, and McAfee.
Given the complexity of modern architectures encompassing multiple security devices and environments, organizations increasingly rely on SIEM solutions. These solutions enable data aggregation, analysis, and visualization across diverse security systems.
Indusface’s AppTrana WAF has been offering SIEM integration for an extended period, and we are excited to introduce a seamless integration feature that allows you to feed vulnerability data from our web application scanner directly into your SIEM solution.
Forwarding WAS Log Data to SIEM
Indusface WAS sends the following logs into SIEM tools:
Scan Logs
Scan logs refer to the records generated during the scanning process of a web application. These logs typically contain information about the scans performed, including details such as the date and time of the scan, the target URL or IP address and scan configurations, and any detected vulnerabilities or anomalies.
Vulnerability Logs
Vulnerability logs capture information related to identified vulnerabilities in a web application. These logs provide details about the specific vulnerabilities discovered during scans, such as the type of vulnerability, severity level, and affected components or systems. They serve as a valuable resource for monitoring and addressing security weaknesses in the application.
Indusface WAS sends a wide array of log data. Listed below are the key data that are common across all assessments:
| Scan Logs | Vulnerability Logs |
| ScanlogId ServicType ServiceId URL SealStatus TotalFoundVulnerabilities ScanStatus ScanDate |
UniqueAlertId Title Severity OpenStatus FoundOn – “URL” FoundDate |
Benefits of Integrating Indusface WAS with SIEM Tools
- Enhanced threat detection and response: Real-time monitoring and analysis of vulnerability scan results enables you to identify and respond to potential threats faster.
- Centralized visibility: You also get a centralized view of vulnerability data alongside other security events, facilitating comprehensive analysis and correlation for better decision-making.
- Streamlined incident management: By combining vulnerability scan data with SIEM, you can prioritize, and address vulnerabilities based on their potential impact, leading to more efficient incident management processes.
- Compliance and audit readiness: Integration helps you in meeting regulatory requirements by providing a holistic view of security events, vulnerabilities, and remediation efforts.
Steps to Integrate Indusface WAS with Your SIEM Tool
Step 1: Indusface WAS Setup
Indusface WAS customers who want to enable the SIEM log feature must set up the integration with the S3 method on the Indusface WAS >> Settings >> SIEM Configuration.
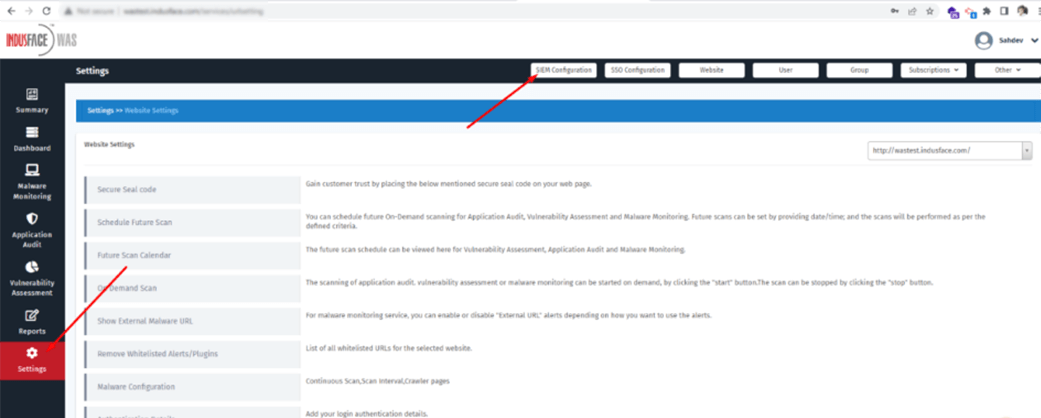
Click on the toggle button to Enable SIEM S3 Logs
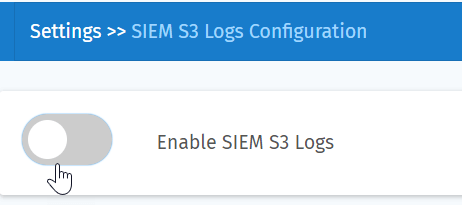
The setup process for SIEM log integration entails SIEM AWS Account ID and SIEM External ID to set up a role-based access account in the Indusface AWS account:
You can get these details from SIEM tools where you want to integrate S3 logs. For instance, the following steps describe creating a collector in Sumo Logic.
Step 2: Create a Sumo Logic Collector
In Sumo Logic, go to Manage Data >> Collection >> Collection and click Add Source
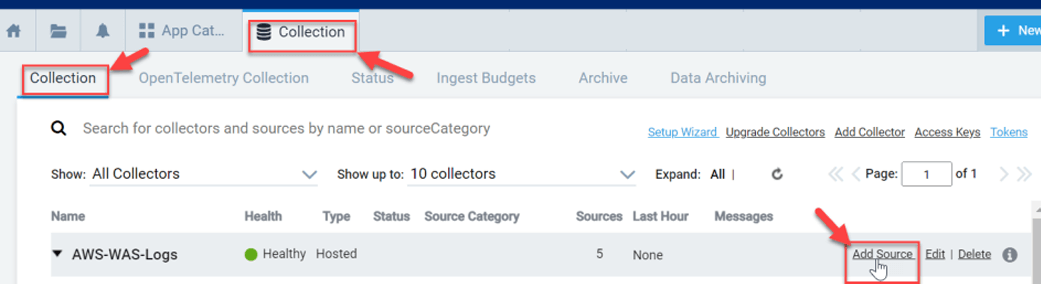
This can be an existing hosted collector or one you have created for this task. Here, we have selected our AWS source type – Amazon S3.
From Amazon S3 > > AWS Access >> Access Method, you can find the Account ID and External ID details.
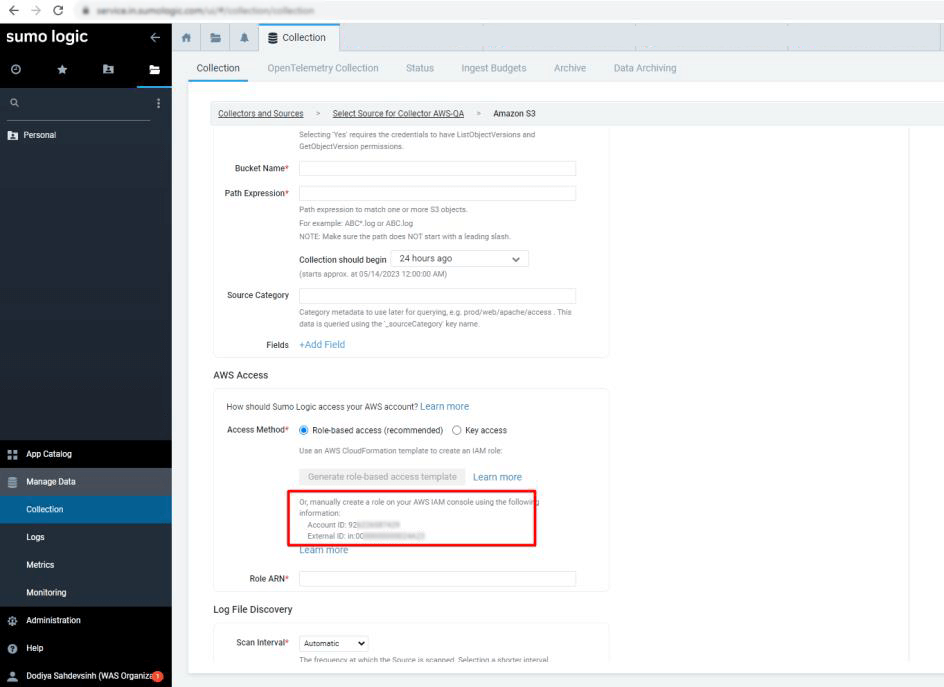
Use the Account ID and External ID in the respective fields of the Indusface WAS (Showed in Step: 1) and then click on the Submit button.

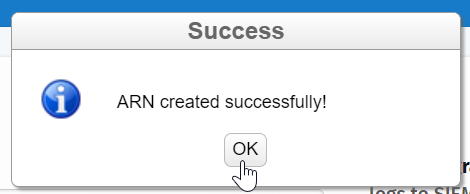
Once the ARN is created successfully, WAS will automatically display the details to integrate S3 logs into SIEM.
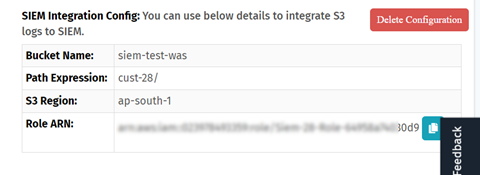
Step 3: Configuring Integration with Sumo Logic
To strengthen security measures, you must connect to your S3 bucket by using AWS Amazon Resource Name (ARN) authentication and an Identity and Access Management (IAM) role.
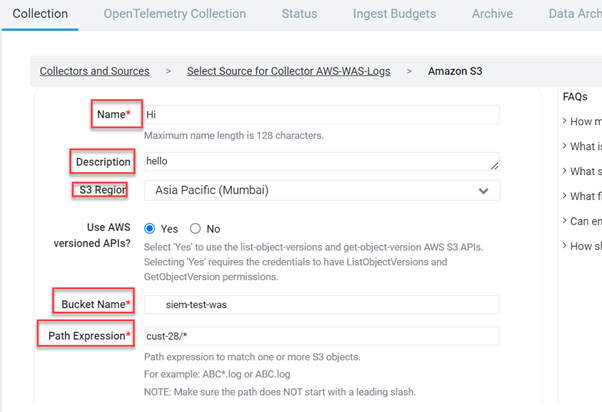
Go back to the Sumo Logic configuration page, and complete the integration form by filling in the appropriate details:
- Provide a Name for the newly created Source. You may optionally include a Description.
- Choose an S3 Region corresponding to the S3 bucket created in your Amazon account.
- Enter the exact name of your organization’s S3 bucket in the “Bucket Name” field.
- For the “Path Expression” field, enter the wildcard pattern that matches the S3 objects you intend to collect. You may utilize a single wildcard (*) in this string.
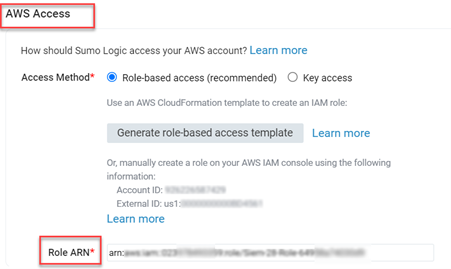
- When selecting “AWS Access,” choose one of the two Access Method options, depending on the AWS authentication you provide. We recommend going for Role-based access.
- In the “Role-based access” field, enter the Role ARN that AWS issued upon role creation. [This was completed in Step 2 – Create a Sumo Logic Collector]
- In Log file discovery, you can specify a referred scanning frequency for your S3 bucket to detect new data.
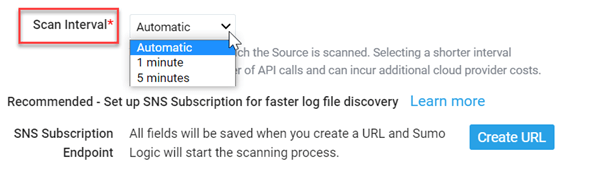
After you have finished the Source setup, remember to click Save to save your configurations.
View WAS Scan Logs on SIEM
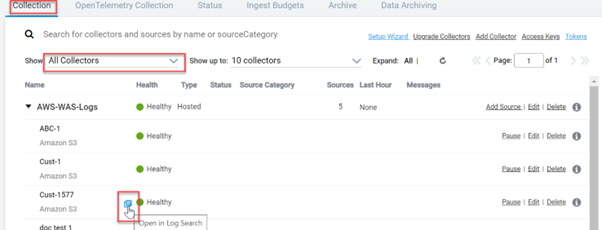
Once the configuration is completed, you can view the Indusface WAS scan logs in your SIEM tool as shown below:
- In the Collection page, hover over your collectors’ name, and a blue icon will be displayed, click on the icon.
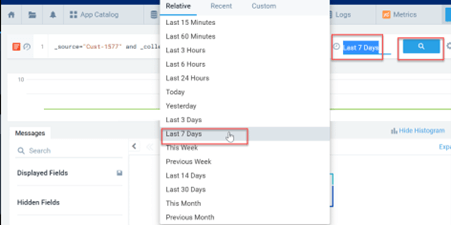
- Once the source collector is opened, select a time span, and click on the search icon to fetch the log record.
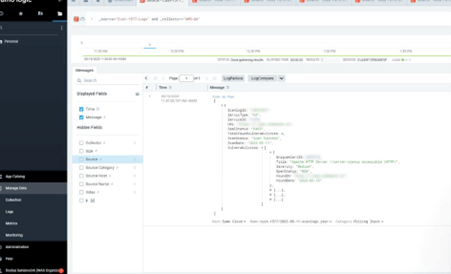
- Scan log details for the selected collector are displayed.
SIEM Integration Use Cases on Indusface WAS
| Configuration | Description |
| Enable SIEM S3 Logs | If the button is enabled, logs will be stored. |
| Disable SIEM S3 Logs | You can disable storing logs temporarily. If the button is disabled, logs will not be stored until you enable it. |
| Update | You can update configuration details with new details |
| Delete Configurations | You can delete the whole configuration |
SIEM is an essential tool for any SOC, and integrating DAST scanners with SIEM tools is a best practice that world-class SOC teams follow. Leverage the integration today, and for any questions, write to support@indusface.com.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 July 13, 2023
July 13, 2023



