How to Stop Data Breach At Your Startup?
Eleven dollars and 39 cents. That is the exact amount by which Sony Corporation’s stock price plunged after a data breach and DDoS attack on their servers in 2011. The stock eventually crashed by 36%.
Target also lost 16% of its earnings post data breach incident in 2014. Not only this, but there was also a considerable drop in Gen-X shopper visits pointing towards how our informed generation feels about hacking incidences.
But do these stories, or any other breach story for that matter, tell us about how startups and new-age cloud businesses suffer from information security lapses? Everyone just talks about losses in billions of dollars for large organizations when a much larger part of the problem is with smaller companies.
Take this data for instance. According to the U.S. Census Bureau, out of all the employers in the United States, 99.7 percent have less than 500 employees. If you break down that data a bit more, 89.8 percent of these businesses have less than 20 employees. The data resonates with most countries in the world including Australia, Brazil, India, France, Italy, and Japan. That’s the strength of startup businesses and that is why it’s a chunk of the security process.
Why Is Security Critical for Startups and New-Age Businesses?
Can an average company suffer data breach costs just like Sony or Target? A global data breach analysis by the Ponemon Institute reveals these crucial pieces of information.
- The average cost of a data breach is $3.79 million.
- There has been a 23% rise in data breach costs in the last two years.
- Every stolen record from the database costs $154 on average.
- India stands second in the average number of breached records by countries.
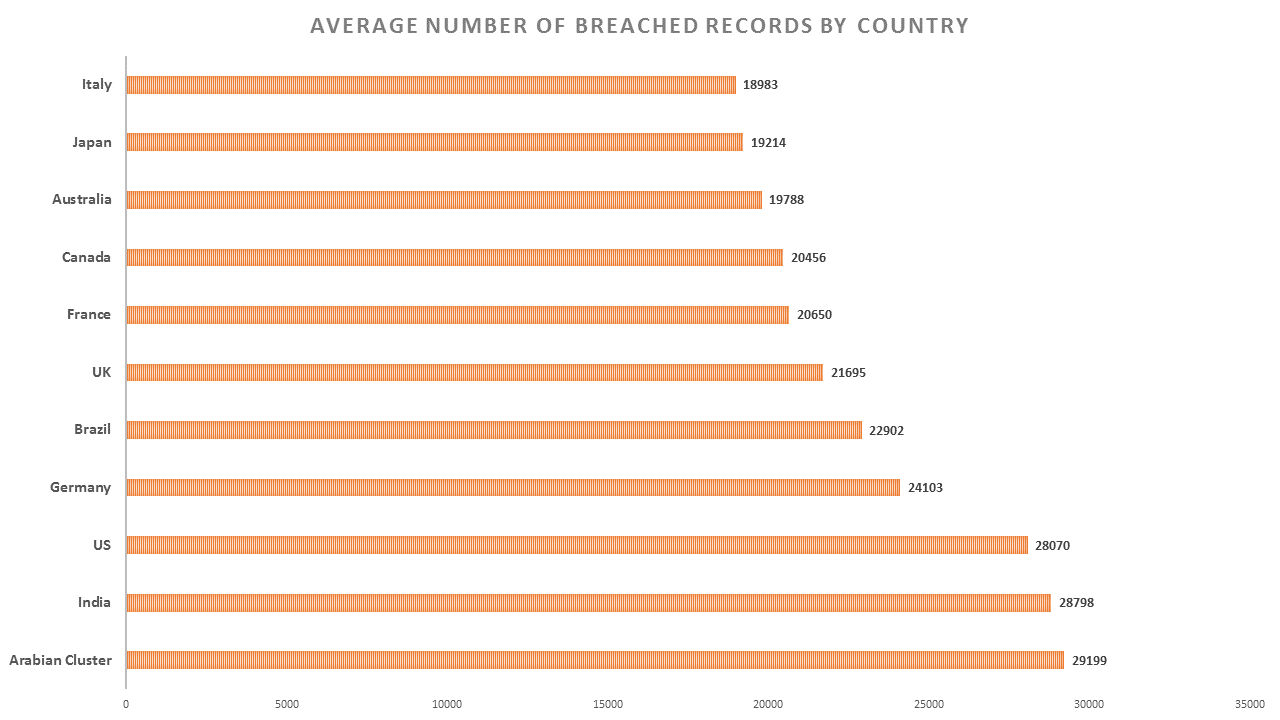
Although the financial repercussions are huge, startups and new-age cloud companies also need to be wary of reputation damage. Their battle for existence and preference over competition depends solely on what customers and prospects presume about the business. And a single data breach or website outage incident can damage that for years to come.
Effective Security Intelligence in Business Model
It’s understandable that information security is not a priority for small businesses focused on raising capital, promoting products, and managing people. However, it cannot be ignored either. Hackers continuously look for weak websites and databases to hold them for ransom or breach sensitive information to be sold in the black market. Additionally, competitors also use dirty techniques to bring a rival website down to its knees.
The big questions are: Can you afford security? Does the security model for startups need to be different from enterprise ones?
Let’s take a look at following India-centric data from Ponemon before getting to those questions.
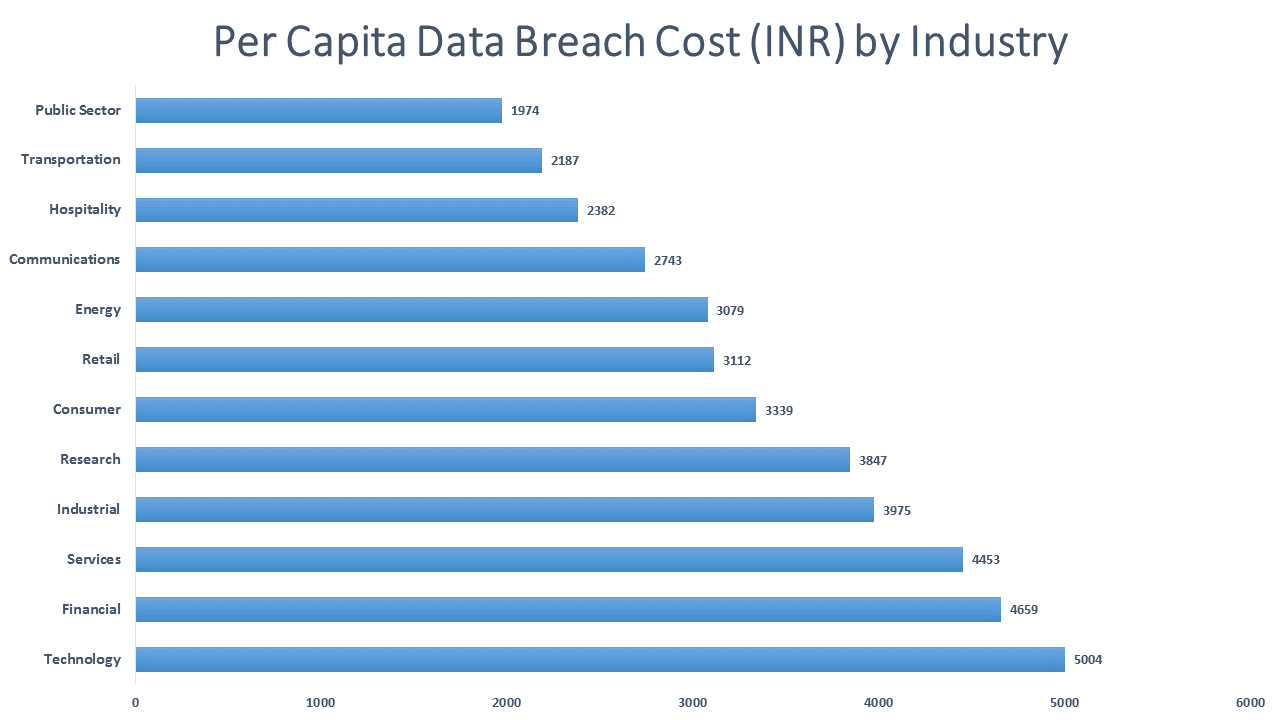
So can you afford security? The average per capita cost (total cost of breach divided number of stolen or lost records) for data breaches outweighs security expenses by huge numbers even when we have not calculated the loss of reputation and drop in traffic and business.
Does the security model for startups need to be different from enterprise ones? Not necessarily. They should also get enterprise-grade security models that are comprehensive but not overly complex. That’s what we have tried to achieve with Total Application Security that empowers websites with security that does not need to be micromanaged.
Adaptive Detection and Protection
What are the key obstacles to website security? One, startups do not know if their website can be hacked or not. Even if they test it once, applications are updated frequently and there is no way to get vulnerability updates on that.
Two, vulnerabilities should be patched. It takes time and resources. And till that happens, the website is open to all kinds of threats.
Three, bad people are just waiting to launch distributed denial-of-service attacks with these fancy bots and machines that send so much traffic to the website that the server crashes.
Four, hiring and maintaining a separate security team is a huge responsibility. It’s not just about the money, it takes time too, which takes away the focus from key business objectives.
The ‘Total Application Security’ idea is to overcome all four of these obstacles, at once. It packs web application scanning that looks for website vulnerabilities continuously. It doesn’t matter if you make application code level changes or update the website frequently, once scanning finds an OWASP weakness or malware injection it will report it immediately.
Total Application Security also provides a web application firewall that blocks exploitations. In simpler words, it prevents attacks from hackers that use OWASP vulnerabilities or malware on your website with the help of a dedicated security expert team that monitors and analyzes traffic and attack vectors continuously to improve your security model accordingly.
In fact, Total Application Security even blocks those bots that send spam traffic to bring the server down with application-layer distributed denial-of-service.
Don’t know what security model will help you? Start with a free website security check with us.

 September 18, 2015
September 18, 2015






