Who Should Take The Blame for Failed Cybersecurity
Did you know that 55% of security professionals think that general staff is an easy target to hack in the company servers?
Hackers often look for the weakest links in the cybersecurity of an organization and exploit it to get to whatever they seek. But, do the organizations really believe that the problem lies at a lower level?
Whenever security is breached, someone has to take the fall for these surprising and unexpected events, which usually come down to top security professionals in the company.
It happened with Target (Beth Jacob resigning as CIO), Utah’s Department of Technology Services, Sony and Chase (CISOs explicitly blamed for breaches), and it happens every once in a while whenever there is a security failure for whatever reasons.
The question is: Is it really reasonable to shoulder everything on security professionals?
Loopholes in Security
The World Wide Web and its communication ways is a nexus of complex mechanisms. We presumably strive to withhold absolute control over its ways but fail to learn that it’s a free and dynamic platform. Variables change frequently and it’s not always humanly possible to safeguard all 7 layers of communication through manual practice.
Additionally, application security remains a stepchild for many companies, which is single-handedly responsible for most major breaches across the world. Still, companies fail to anticipate this risk and do not devise necessary testing, patching, and mitigating measures. And when it comes to accountability, there is just one team to blame, i.e. the cybersecurity cell.
However, senior cybersecurity experts and reporting journalists jointly believe that it’s wrong to blame CIOs and CISOs only. They say that no matter how many best practices CIOs follow, how many communication models they encode, how many applications they test, there will always be a vulnerability in software, operating system, or application that coders do not know of. In fact, with aggressive spying and social engineering, hackers can get hold of critical information through any layer of the OSI communication model.
The Shared Accountability Model
When it comes to cybersecurity, it is important that everyone shares the responsibility of keeping information secure and designing protocols for it. And before we move ahead, take a brief look at the finding from a survey last year.
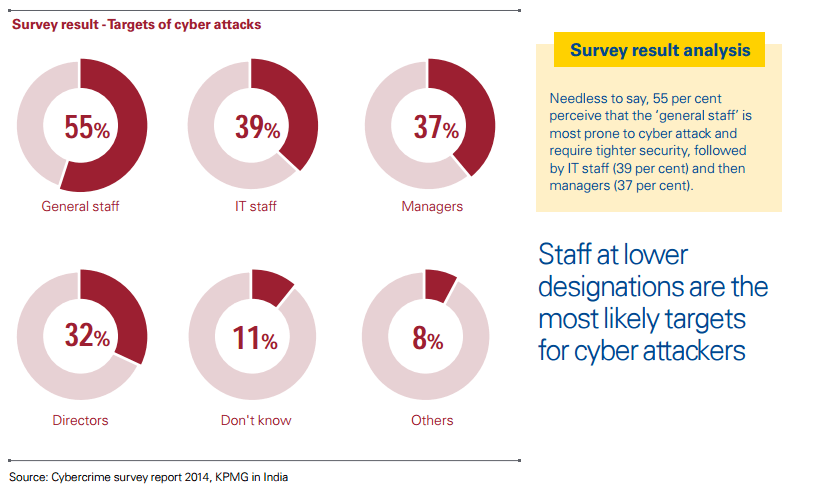
Staff at lower levels (as opposed to presumed notions that CIOs and CISOs are the most targeted staff) are more vulnerable to leak information outside. It can be deliberate, miscommunication, or simply negligence, especially in the case of IT staff who is actively involved in the development and maintenance of critical website assets including web applications that are more targeted than anyone else.
So, does the answer to all your cybersecurity problems lie in securing the lower levels of organizations? Do CIOs have nothing to do with data breaches? How will you ever know that data is secure within your servers? How can you measure the efficiency of security officers?
The problem in itself is grave, but sacking CIO or CISOs after a breach is a pretty bad idea to start with. They understand your security protocols better than anyone else in the organization and probably they have the best chance of looking into what went wrong. As for their efficiency, it’s an ongoing process that requires consistent inputs and steps to make security better. Here’s a guide on how to deal with data breaches and attacks while strengthening overall security protocols.
1) Immediate Protection
If you have been attacked recently or still under attack it is critical to look for problem areas and start securing assets at the earliest. Physical and network layers are most important in the case of data breaches. Your organizations might also want to seek third-party help for securing Layer 1 and 3.
At the same time, given that approximately 7.5 attacks out of every 10 happen at the application layer, auditing web applications is important too. Indusface also recommends immediate web application firewall deployment to block OWASP and business logic exploitations immediately.
2) Detailed Auditing
The next logical step is to look for vulnerabilities that could have compromised your information security. It’s a detailed and lengthy process, which will take a lot of time for your security team. Make sure that you know what has been stolen and exploiting what vulnerability.
If you don’t have a separate application audit team, use security vendor services to penetrate into your network and test for loopholes using web application scanning and manual testing.
3) Resolve Inherent Issues
Often security audit reports underscore grave issues within the organizations, but management chooses to overlook them for the time and money changes would cost. Quite understandably, it is not always feasible to follow every suggestion, but make sure that you at least follow the best practices.
For instance, make sure that the open-source code chunks are tested thoroughly before use. Also, frame policies to stronger security inside the network and make sure that important processes are monitored.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 May 21, 2015
May 21, 2015




