Under the hood of Behavioural DDOS Protection
Blog Series 2 out of 2
In the last blog, we saw why static rate limits do not work and why behavioural DDOS is required.
Now, let’s investigate how these policies work. As mentioned, when a site is onboarded, there are 3 policies that are configured by default. We call them System defined Protection policies-
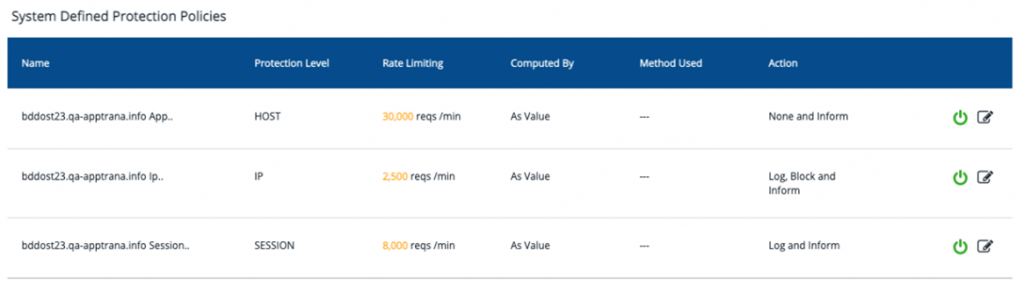
Host level Policy:
This is an informational policy that will notify when requests goes beyond a certain level. By default, it is configured to trigger when requests go above 200% of normal max. Max is the maximum requests seen on the application in a minute in last 7 days. This max is calculated every day and adjusted based on application behaviour. So if there is natural variance in the site, it will automatically be accounted for and tuned. By default, notification goes to the website admin and if website admin is not configured then mail is sent to super admin.
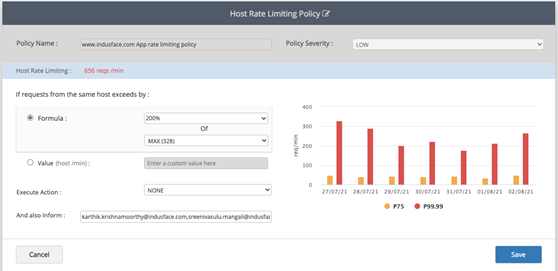
This is a good informational level settings that can be used as early warning on increase on load to the system. It should be noted that this does not block any requests at any point, it just tells you that considering the site behaviour in 7 days, the request volume seems to be unusual. It can be used for automating scaling of origin. This notification is also shared to Indusface managed service team who will monitor the site traffic and see if any further action are required.
IP Level Policy.
This policy is a IP level behaviour rate limiting rule. By default, policy is configured to block requests from an IP if the volume of requests from that IP is more than 200% of last 7 days maximum of any IP. For example, suppose the application normal max seen is 100 requests per minute, and all of a sudden we see 200 requests in a minute from 1 particular IP then it will be blocked.
Get URI-Based DDoS Protection for your Applications
This IP level policy will only apply when the requests do not honour cookies and requests are not tracked at a session level. So if there are 1000 requests from an IP, but 800 requests honour cookies then those requests are not considered in the IP level policy. By default these are configured to block and notify website admin. This can be changed as per customers need.
Session Level Policy.
For requests which honour cookies, session level rate limits will be applied. Here, the default configuration is to block if number of requests from a session increases beyond 150% of last 7 days maximum. If typically a user sends 20 requests per minute but all of sudden starts sending 31 requests per minute then they will be blocked.
Session rules and IP rules work together, one is not a replacement of another , both should be enabled for an application to get maximum protection.
User Configurations:
Users are provided various controls.
- Users can also create new policies at any level, IP, session or host level. This is essentially for users to configure multiple level of alerts and actions. So customer can choose to be alerted when requests go 120% of max of last 7 days and block at 150% giving additional controls to customer.
- Users can
- Change the settings and configure when the policies should be triggered. 2 options are available
- By Formula (Recommended)
- Set % above (Max or Median) of last 7 days when the policy should be triggered
- By Value
- Set static value at which rate limit should be triggered.
- Change the person who should be notified when policies are triggered
- More than 1 email address can be configured.
- Change the action to be taken on the policies
- No action – typically used with notify option
- Log
- Block ( Block option is not available for host level policy)
- Disable any system configured policy
- Delete any user defined policy.
- By Formula (Recommended)
- Change the settings and configure when the policies should be triggered. 2 options are available
Additional Behaviours:
- If block is configured, the IP/session will be blocked for 2 minutes.
- If attack continues, the block will be extended until AppTrana does not see any request from the IP/session for a 2 minute period.
- If notification is triggered for an IP/session/host , then notification won’t be repeated for next 10 minutes for same IP/session/host. So notification will be sent every 10 minutes while attack continues.
- The max /median values for any level (IP/session/host) are adjusted every 24 hours. So any changes in a particular day will reflect the next day
This is a very user friendly effective feature that would help customers block DDOS effectively. This is just a start and we will be adding more features, controls and actions that will enable even more granular configuration of DDOS protection.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 August 9, 2021
August 9, 2021





