CSV Injection with CVS Export Feature
Banking, eCommerce, and a number of other websites increasingly offer spreadsheet export functionality within their applications to help users download.XLS and .CSV files to be used with Microsoft Excel and OpenOffice Calc.
These spreadsheets often contain inputs from untrusted sources. Did you know that transactional details, survey responses, and other user-supplied fields in these files can be used to attack your website?
“Download as a CSV” feature sometimes does not properly “escape” fields. This allows an adversary to turn a field into active content so when a response team downloads the CSV and opens it, the active content gets executed. Vulnerability also is known as “Formula Injection”.
Here is the scenario to reproduce this issue:
Suppose there is a web application where one can add the company’s branches and locations. End-user can view the list and can also download the entire list as a CSV file. See the screenshot below:
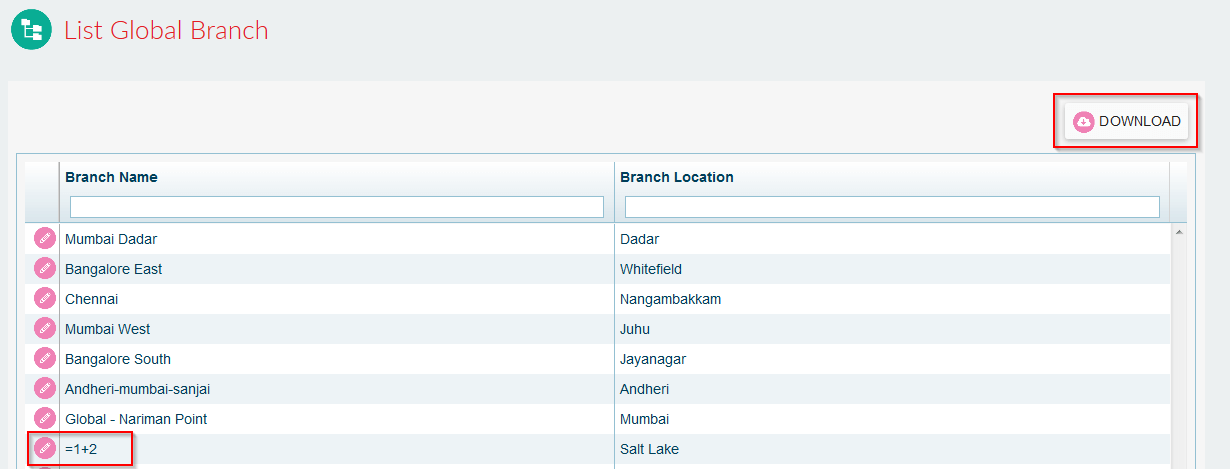
- Attacker can add a branch name and location with value “=1+2”
- Victim can see the list, can download it as a CSV file.
- Cell containing the branch name “=1+2” is displayed as “3” which means the code is executed. Check this screenshot:
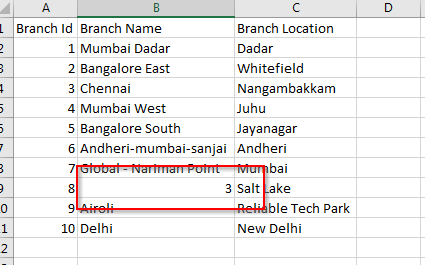
Exploitation:
Insert calc payload in “Branch name”.
Payload: -2+3+cmd|’ /C calc’!A0
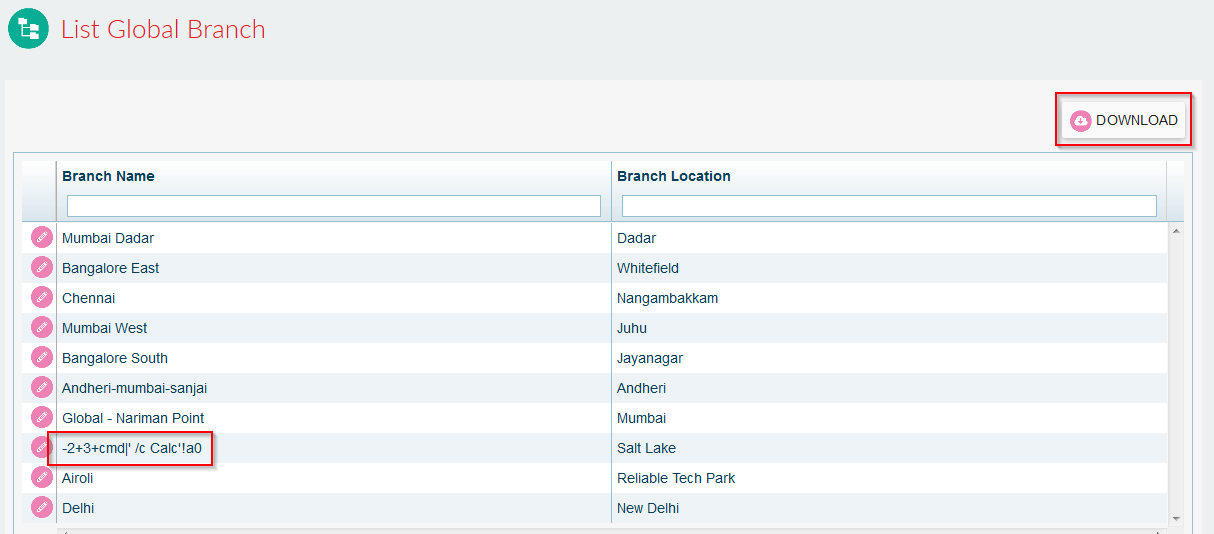
Payload code executed successfully:
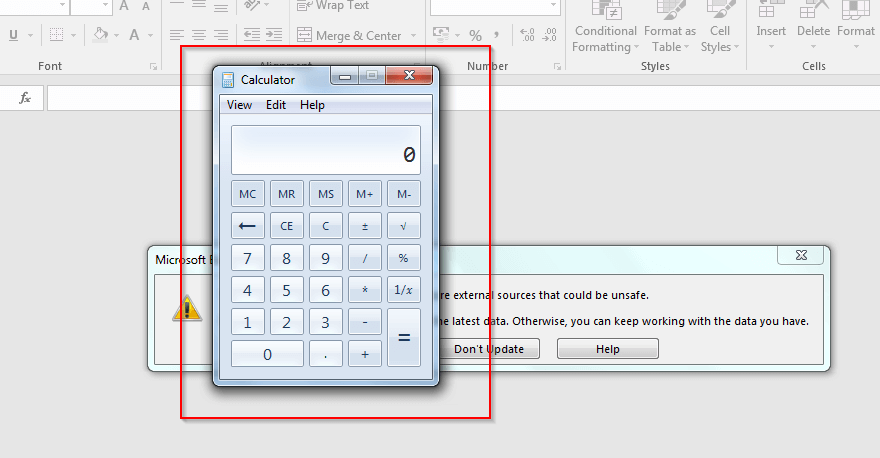
Protection with the Indusface AppTrana:
Given that the ‘comma-separated values’ are widely used and are an important part of the business process, you need to secure the server against malicious intents hidden in the file fields. Our security experts can create a custom rule to ensure that all fields are properly “escaped” before returning the CSV file to the user.
If you are an existing Indusface customer, request for the custom rule through our TAS Portal. And if you aren’t, find out how Indusface AppTrana can help you detect, protect, and monitor for this issue and many others at our Guided Product Tour. We also continuously gather reputation data based on IPs, machines, and other parameters to identify people violating the rule and use the observations to correlate the data with other possible attacks on your website.


 May 31, 2016
May 31, 2016



