WannaCry Ransomware Attack: How to Protect Your Business?
Last Friday, the world witnessed one of the largest cyber-attacks ever affecting 150 countries. Known as the WannaCry ransomware attack, it crippled 42 National Health Service trust centers in the United Kingdom, hundreds of computers at the Russian Interior Ministry, and many university networks in China.
Tens of hundreds of computers at private companies have also been affected including German rail operator Deutsche Bahn, international shipper FedEx Corp, car manufacturers Renault and Nissan, and Spanish telecommunications company Telefonica. The attack is still in progress and we suspect that it will continue to affect businesses across the world in the coming days.
Malware Spread Timeline
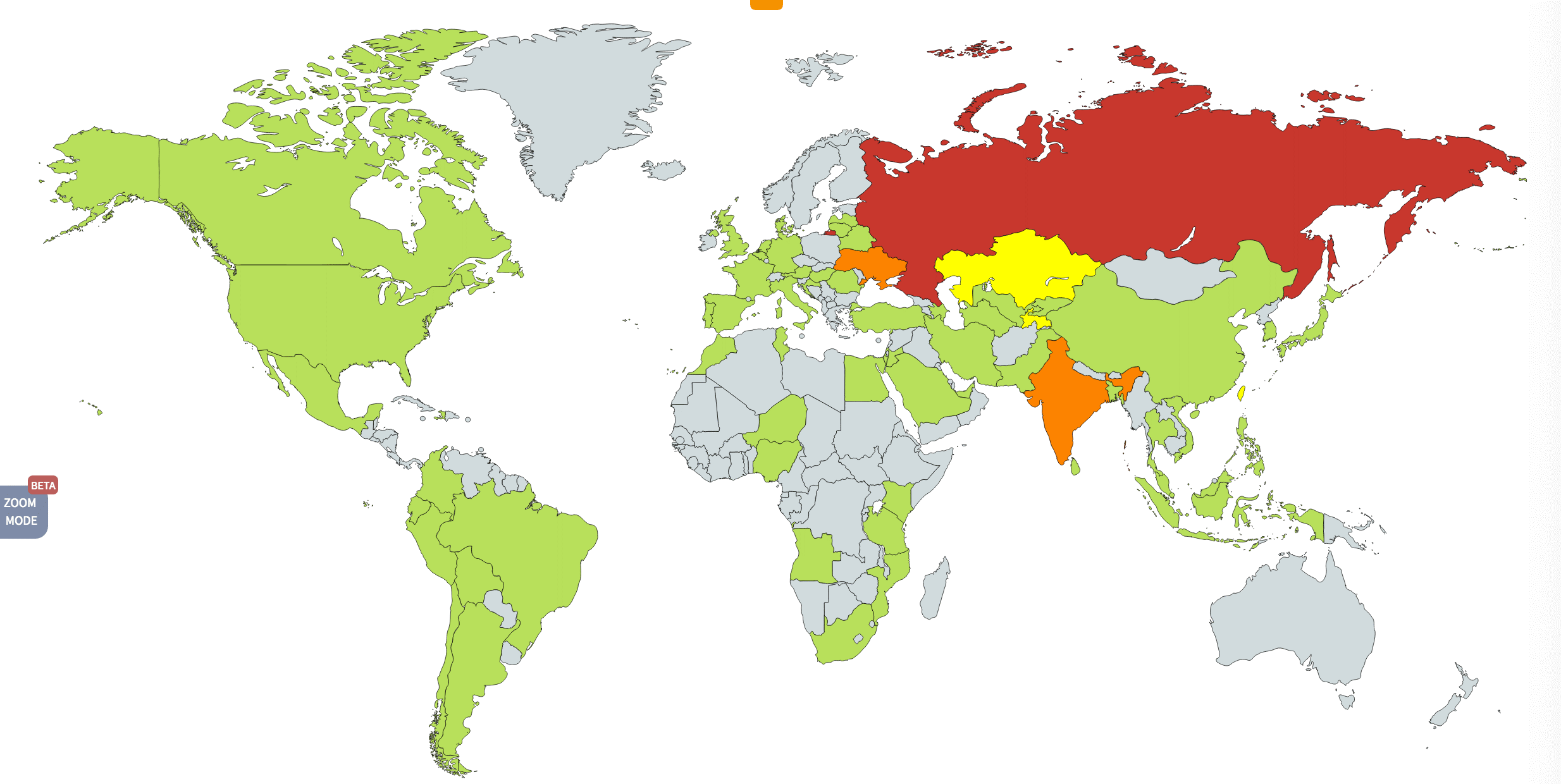
Source: Kaspersky Blog
Phase 1: On Friday, in some parts of Europe, a computer user opened an email with a malware attachment. This compressed file allowed the WannaCry malware or virus attacked the machine’s hard drive.
Phase 2: WannaCry encrypted all the data stored on the hard drive. Later, it asked for $300 to $600 in bitcoins to decrypt the data.
Phase 3: Meanwhile, this malware communicated with new machines, eventually spreading to 200,000 Windows computers at banks, hospitals, and oil companies through emails.
Phase 4: By Sunday, WannaCry had disrupted services of Spanish mobile operator Telefónica, carmaker Renault in Germany, mobile phone provider MegaFon, and Sberbank in Russia, and FedEx in the US.
Phase 5: Although the attack has slowed down by Monday, WannaCry’s creators continue to ask for ransom for decrypting data. It is possible that many companies haven’t noticed the attack yet.
WannaCry Behavioral Analysis
Although this malware primarily targets PCs and laptops that still use Windows XP, more recent Microsoft systems, including Windows 8 and 7, can also be infected. There hasn’t been any reported exploitation in Windows 10 yet.
Once a user clicks on unsuspecting links or email attachments, WannaCry downloads itself on the system and uses strong, asymmetric encryption, employing the RSA 2048-bit cipher to encrypt all the files.
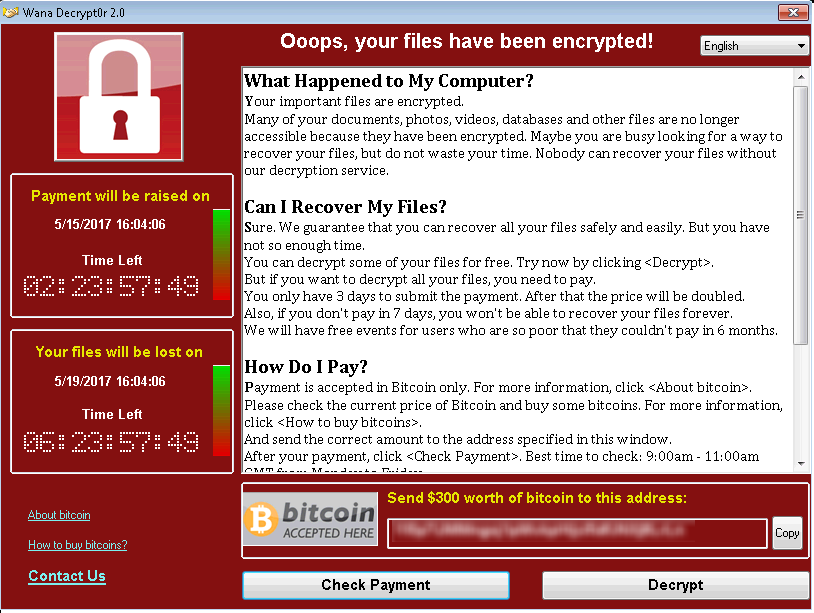
Source: SecurityIntelligence
Hackers are believed to be exploiting the stolen NSA tool EternalBlue released to the world last month by a group known as Shadow Brokers. The attack exploits the vulnerability found in SMB that was patched Microsoft security bulletin MS17-010.
Since the architecture of this malware is modular (complex), security experts believe that creators are a part of an organized gang.
“If I was a betting man I would say this was most likely an organised criminal group. They are going to be found. They’ve just put themselves on the top of everybody’s dinner plate,” said the Fidelis software expert John Bambenek.
Secure All Your Computers at Work
Security Patch: No business would want critical documents locked out of reach; until the ransom is paid. If any of your systems are still using Windows XP, upgrade it to a more recent operating system on priority. For other Windows operating system versions, install this security patch by Microsoft.
Issue Internal Warning: Microsoft has advised users to avoid downloading random attachments and click on links from email senders they do not recognize. You should send out a warning email to all the employees about it.
Patch Alternative: If you can’t patch immediately, temporarily disable SMB on your system. Here’s a brief guide on that.
-
- Search for Windows features-> Open settings
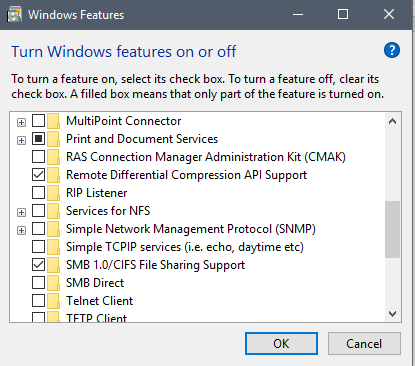
- Uncheck SMB and restart the system. Please note that disabling SMB might affect shared services. Hence, assess before disabling.
- Ensure that the Microsoft Malware protection engine is also patched.
Last version of the Microsoft Malware Protection Engine affected by this vulnerability – Version 1.1.13701.0
The first version of the Microsoft Malware Protection Engine with this vulnerability addressed – Version 1.1.13704.0
You can find further details here.


 May 15, 2017
May 15, 2017



