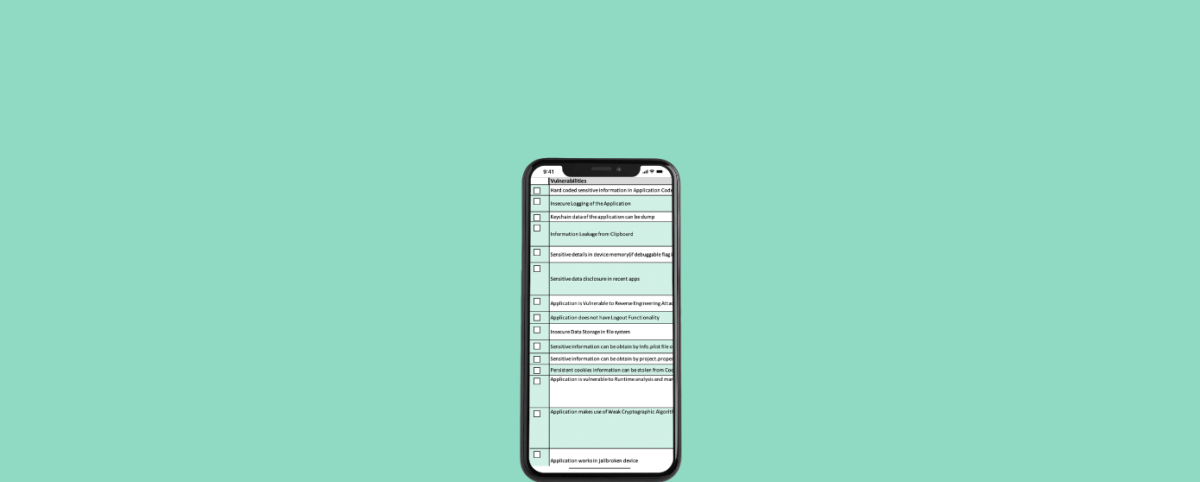
Web Application Penetration Testing Checklist
The proverb, “A stitch in time saves nine,” encapsulates the core of web application security. Businesses must always be one step ahead of attackers and malicious actors to identify vulnerabilities, weaknesses, and misconfigurations in web applications and ensure they are patched and/or fixed before attackers can find and leverage them to orchestrate attacks.
One of the critical measures in such a web app security solution, apart from security tools such as vulnerability scanners and WAF is web application testing or penetration testing.
What is Penetration Testing?
Penetration testing (Pen-testing) enables businesses to check and understand the strength of web application security by simulating a real-time cyberattack under secure conditions.
Every web application has several components and assets publicly exposed and vulnerable to attacks. It is quite a challenge for most businesses and developers to figure out which application parameters and components need to be included in the web applicaiton penetration testing checklist and how to proceed.
Web Application Penetration Testing Checklist
Gathering Information
Pen tests cannot be randomly or blindly done. The first and most important thing you must do is collect all possible information about your web application, its potential threats, weaknesses, and risks involved.
This introductory step is called ‘Reconnaissance’ and is actively used by hackers to choose easy targets.
Passive Reconnaissance: Ethical hackers use a combination of tools and research about the application. Every piece of information is handy. Information on DNS, WHOIS databases, and web server types provides preliminary information on how a tester should perform the attack simulation.
Ensure to include comments and metadata, third-party apps/ services on the application, metafiles, and all entry points while gathering intelligence about how different parts of the web application/ target work.
Active Reconnaissance: Once a penetration tester or hacker has all the basic information about the target applications, he moves to the next stage by sending packets to the target system. This can be a manual or automated task to look for vulnerabilities, firewalls, and DDoS protection tools.
Vulnerability Scanning
As mentioned earlier, web applications contain several components and vulnerabilities that need to be tested. Using automated tools such as web vulnerability scanners, you can scan for known vulnerabilities such as SQL injections, XSS, file inclusions, and another OWASP top 10.
Onboarding on services like Indusface WAS, you will be able to customize scanning and tune policies based on the unique requirements of your business. With the help of the security analytics that is made available, you will be able to understand vulnerabilities, the nature of attack attempts and attack patterns.
You can then validate the scanning findings to see what is exploitable and the risks involved.
Develop a Robust Security Strategy and Pen-testing Plan
Based on the information/intelligence gathered and the site map created, draw up a robust security strategy by defining the scope, objectives, and expected outcomes/ deliverables of penetration testing and prioritizing critical problem areas & high-risk components over others.
High priority should be given to parts of the application where users can add, delete, or modify content (comment section, contact forms, etc.), third-party services hosted, entry points, etc.
You should also include testing as different users – an unreliable external source with minimal or no privileges and a user with all possible privileges and authorizations.
You must define the methods and tools you will use for web application testing. If you are not doing the pen-testing and onboarding of a security service, ensure it is entrusted only to trustworthy & certified security experts.
They can combine their intelligence and technical skills with creative thinking and innovative approaches to uphold the highest levels of web application security.
Actual Exploit: What to Include?
At this stage, the security professional or ethical hacker attempts to leverage vulnerabilities and weaknesses discovered during the previous phases (such as information gathering, scanning, and enumeration) to gain unauthorized access to a system or network.
This phase aims to simulate a malicious attacker’s actions and demonstrate the potential impact of a security breach.
Pen tests must be used for testing the following.
- Misconfigurations in deployment and configurations of the network, app platform, framework, file extensions, etc
- Loopholes in access control, privileges, authentication, authorization, and identity management that allow malicious actors to steal sensitive data
- Pen testers keep altering the privileges and access control levels to see if and which vulnerabilities can be exploited. They also check the impact of prolonged access and privileges on the system and data
- Session management weaknesses – logout functionalities, session timeout, CSRF, session hijacking, etc
- Input/ data validation flaws to see if the application allows un-sanitized user input
- Error handling by the application to see if cyber-attackers can gather enough data to orchestrate attacks
- Data encryption and data transmission loopholes
Business Process and Application Logic Mapping
Attackers no longer target OWASP Top 10 vulnerabilities; they look beyond the usual vulnerabilities and dig into the application’s logic to uncover business-specific loopholes.
The following are examples of business logic flaws that automated tools would miss:
An e-commerce site allows users to add items to a cart, view a summary page, and pay.
- What if they could return to the summary page, maintain their same valid session, inject a lower cost for an item, and complete the payment transaction?
- Can a user hold an item infinitely in the shopping cart and keep others from purchasing it?
- Can a user lock an item in a shopping cart at a discounted price and purchase it after several months?
- What if a user books an item through a loyalty account and gets loyalty points but cancels before the transaction can be completed?
Penetration testers should consider all the business processes and application logic that can be used to exploit weaknesses within the application.
Result Analysis and Reporting
Just doing the pen-testing does not suffice; engaging in a tailed analysis of the testing results is crucial. Compile the findings and the analysis so that the security personnel can finetune the WAF and other security measures and developers can fix critical and high-priority vulnerabilities.
The key stakeholders must understand the nature of known and unknown vulnerabilities, sensitive data that are accessible, and the timespan the vulnerability remained undetected in the system.
An ideal pen testing report should contain the:
- Number of vulnerabilities
- Types of vulnerabilities
- Criticality of vulnerabilities
- Business impact
- Remediation guidance
- Observations from the tester
- Analysis
Indusface WAS, a comprehensive solution that leverages a combination of DAST and Manual Penetration Testing to identify vulnerabilities. With Indusface WAS, you can access in-depth reports that provide valuable insights into vulnerability findings, remediation recommendations, and prioritized checklists for enhanced security.
The unified dashboard offers a range of reporting features for penetration testing, including:
- Easy extraction of the pen-test report with a single click, allowing for a separate view from the comprehensive report.
- A dedicated section for efficient tracking of historical pen test results.
- Swift collection of re-validation data.
- Eliminating the need for external teams’ involvement during audits and compliance assessments to gather pen test details.
- A historical graph that presents a summary of penetration test results.
Explore a quick guide to the penetration testing reporting capabilities in Indusface WAS:
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 October 23, 2023
October 23, 2023