3 Recommendations to Overcome Web Application Security
Our web application security challenges troubling you? Often most companies are so focused on an extensive list of requirements wrapped in fast, flexible, cheap that the focus on doing it ‘securely’ is lost in the process. And the repercussions? – Hacks and data breaches to point of having breach fatigue.
Every day is loaded with such examples such as Target’s massive data breach resulted in 140 related lawsuits and the resignation of its CEO and Sony’s stock price plunged by $11.39 after a data breach. The blow is even more severe on smaller companies; 60% of them were out of business within just six months of a hack.
Like any responsible website owner, you are probably already aware of the web application security challenges. However, most application developers are so torn between deadlines and customer requirements, that security often takes a backseat. Here are three of our top recommendations that will keep securing without consuming resources.
Recommendations to Overcome Web Application Security
Recommendation 1: Get A Managed Cloud Web Application Firewall
Irrespective of all the planning to finding and fixing vulnerabilities at the earliest, business priorities take over. Patching tasks on critical and non-critical applications often get pushed. And it’s not just with your business, every company has a similar story.
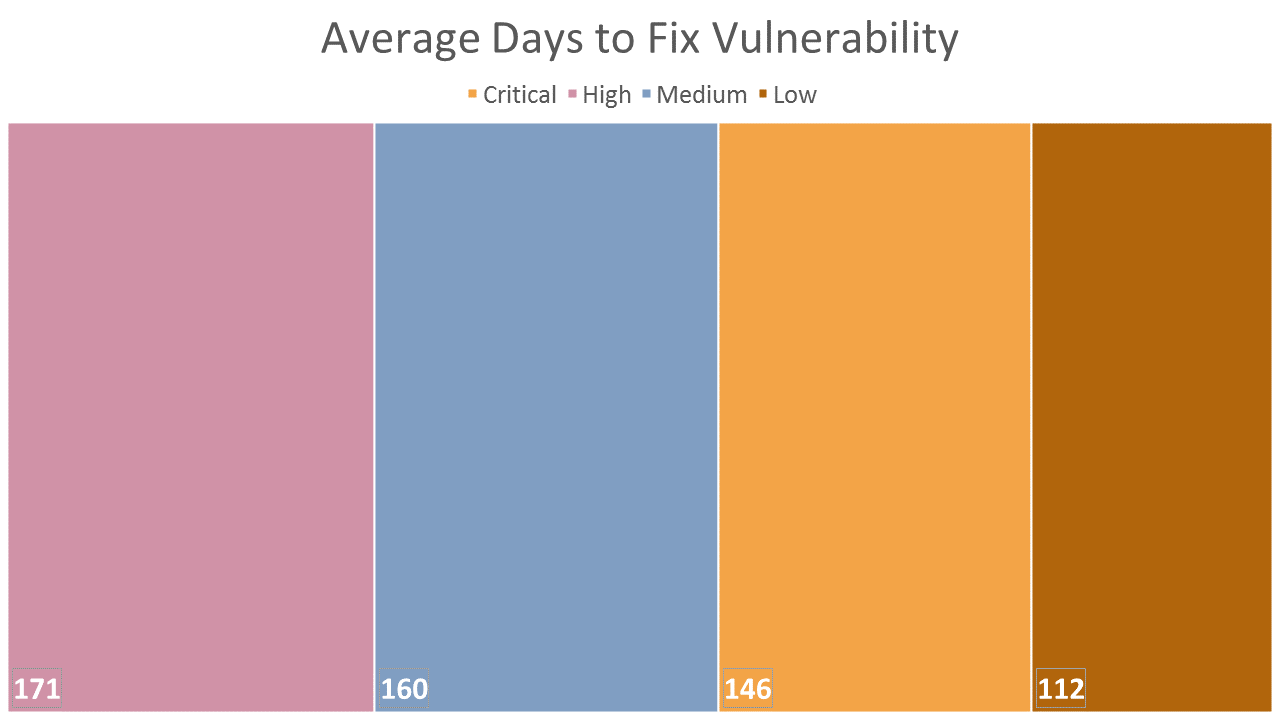
As per the Web Application Security Statistics Report, developers take 146 days on average to fix even critical vulnerabilities. So that’s close to 5 months of web application security challenge and time for attackers to hack your application.
A Web Application Firewall (WAF) covers the visibility and patching gap. It filters the traffic and blocks if malicious. Gartner recently recommended deploying a WAF in its ‘Overcoming Network Security Service and Support Challenges’ report and said “using a SAAS based managed Web application firewall” such as Indusface is a good alternative for Enterprises that do not want to procure new hardware and have time to hire and train staff to manage it.

Why Managed Cloud WAF
If you’re looking at ways to protect applications whilst optimizing resource usage, appliance-based WAFs seem contradictory. Appliance costs with hiring and training security employees would cost a lot of money and time. Today, that’s a major web application security challenge for most companies.
A cloud WAF, however, allows both small and big companies to secure their applications without the trouble of purchasing hardware. Indusface’s web application firewall further offers an extended team of security experts, ultimate custom rules, security analytics, and intelligence along with DDoS mitigation without ever needing to place an appliance or even hire a single security person.
Recommendation-2: Cover Your Distributed Denial of Service (DDoS) Vulnerability
It doesn’t matter even if you develop the most secure application or website; it will still be vulnerable to DDoS attacks. How? If your website is a shop, Distributed Denial of Service (DDoS) is like sending in a mob that doesn’t let your customers get in. Unless you find a way of spotting bad traffic without affecting the real users, there is no way out of it.
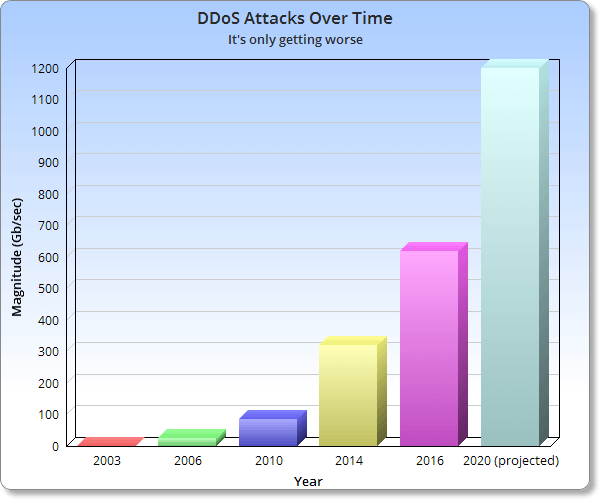
The number of DDoS attacks has grown significantly in recent years, and they continue to do so.
How to stop DDoS attacks?
Deploying a web application firewall is one of the must counter DDOS at the application level, and going for this with a deployment option in the public cloud ensures you get DDoS protection also at the Network level and this is taken care of by the public cloud providers such as AWS.
Recommendation 3: Do Periodic Penetration Testing
You probably have some sort of automated vulnerability detection tool, but does it truly make you secure? Let’s say that you patch all the generic OWASP Top 10 vulnerabilities that this tool finds. Does it ensure protection?
Applications are complex especially when they are unique to your company, using business logic specific to your business and application flow.
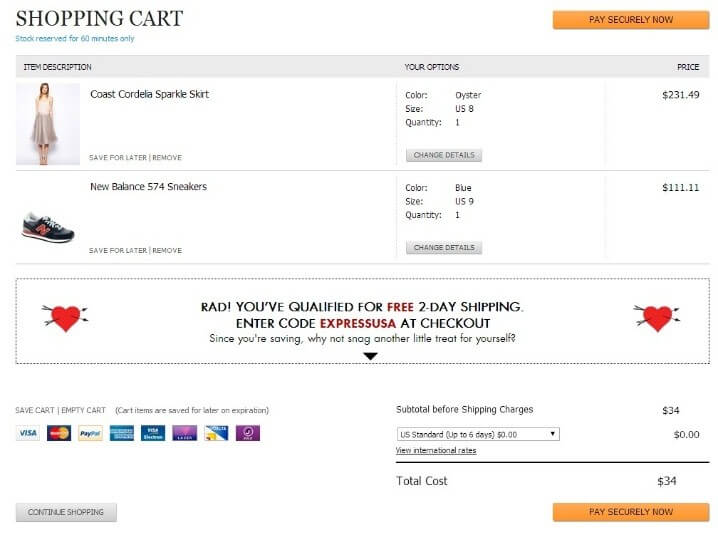
For instance, your e-commerce site allows users to add items to the cart, view a summary page, and then pay. What if he could go back to the summary page, maintaining their same valid session and inject a lower cost for an item and complete the payment transaction?
How to test for such flaws?
Such vulnerabilities even though can be difficult to find have far greater risks for the business and hackers will be using a combination of automated tools and manual exploits to do fraud. Stay a step ahead of the hackers and a combination of automated and manual pen testing to ensure that you fix them before hackers find and exploit them.

 July 14, 2017
July 14, 2017