Web Browser-Based Attacks – Types, Examples, and Prevention
Web browsers are vital for businesses, providing easy access to websites and content, but they also pose significant security risks.
95% of undetectable malware is spread through web browsing. Even more alarming is that browse-borne malware costs organizations an average of $ 3.2M.
This statistic raises a crucial question: how can you protect your end-users from these attacks?
In this blog, we’ll discuss why browser-based attacks happen, outline 10 common types, and offer strategies to safeguard your end-users.
What is a Web Browser-Based Attack?
A web browser-based attack targets vulnerabilities in web browsers to compromise user data or execute malicious code. These attacks also exploit weaknesses in web applications accessed via web browsers, compromising user data, stealing sensitive information, or disrupting services.
Attackers may leverage the website’s execution to target its end users. Consider clickjacking and malicious pop-ups. Here the attackers inject malicious code into the website. And the end-user systems will direct sensitive data to attackers.
Why do Browser-Based Attacks happen?
Browser-based attacks occur due to a combination of technical flaws, insecure practices, and malicious actions. Here are some key reasons why these attacks happen:
- Technical Vulnerabilities: Flaws in browsers, plugins, and web applications provide entry points for attackers to exploit.
- Insecure Web Practices: Poor coding, lax security measures, and inadequate validation create vulnerabilities ripe for exploitation.
- User Ignorance: Lack of awareness about threats and safe browsing practices makes users vulnerable to manipulation.
- Software Neglect: Failure to update browsers, plugins, and systems leaves known vulnerabilities unpatched, and easy targets for attackers.
- Third-party Risks: Dependencies on external scripts and services introduce additional attack vectors.
- Financial Motivation: Attackers engage in activities like data theft, fraud, and ransomware for financial gain.
10 Common Web Browser Based Attacks
1. Cross-Site Scripting (XSS)
XSS occurs when an attacker injects malicious scripts, usually JavaScript, into web pages viewed by other users. These scripts execute in the context of the victim’s browser, allowing the attacker to steal cookies, session tokens, or other sensitive information, deface websites, or redirect users to malicious sites.
Example: Consider a blog website that allows users to leave comments. An attacker could submit a comment containing a malicious script that, when viewed by other users, steals their session cookies. When those users’ browsers send the cookies to the server, the attacker intercepts them, gaining unauthorized access to their accounts. Take a look at our comprehensive guide on robust measures to prevent XSS.
2. Cross-Site Request Forgery (CSRF)
CSRF attacks exploit the trust a website has in a user’s browser by tricking users into unknowingly executing unwanted actions on a web application in which they are authenticated. The attacker crafts a malicious request and tricks the victim into triggering it, often through social engineering techniques.
Example: An attacker sends a victim an email containing a link to a malicious website. Upon visiting the site, the victim’s browser executes a hidden request to a legitimate site where the victim is already logged in (e.g., a bank). This request transfers funds from the victim’s account to the attacker’s account without the victim’s knowledge.
3. Phishing
Phishing attacks involve masquerading as a trustworthy entity to trick users into providing sensitive information such as usernames, passwords, or credit card details. Attackers typically use email, instant messages, or fake websites to deceive victims.
Example: An attacker sends an email pretending to be from a legitimate bank, requesting the recipient to update their account information by clicking on a link and entering their credentials on a fake login page. The unsuspecting victim provides their sensitive information, which the attacker then uses for malicious purposes.
4. Drive-By Downloads
Drive-by download attacks exploit vulnerabilities in a user’s browser or plugins to download and execute malicious code onto their system without their consent or knowledge. This code can perform various malicious actions, such as stealing data or installing additional malware.
Example: A user visits a compromised website that contains hidden malicious code. This code exploits a vulnerability in the user’s browser to silently download and execute malware onto their system, infecting it without the user’s awareness.
5. Man-in-the-Middle (MitM) Attacks
MitM attacks intercept communication between a user’s browser and a website, allowing attackers to eavesdrop on or modify the data exchanged. This can lead to data theft, session hijacking, or the injection of malicious content.
Example: An attacker positioned between a user and a public Wi-Fi hotspot intercepts the user’s HTTP requests. The attacker can view and modify the data transmitted between the user’s browser and websites, potentially capturing sensitive information such as login credentials or injecting malware into web pages.
6. Clickjacking
Clickjacking involves tricking users into clicking on something different from what they perceive. Attackers typically overlay transparent elements on top of legitimate web content to deceive users into interacting with hidden elements, such as buttons or links, which perform unintended actions.
Example: An attacker creates a malicious website that overlays an invisible iframe on top of a legitimate webpage, such as a social media “like” button. When the victim visits the attacker’s site and attempts to click the visible content, they unknowingly interact with the hidden iframe, triggering actions like posting unwanted content on social media.
7. Browser Hijacking
Browser hijacking occurs when malware takes control of a user’s browser, often through malicious browser extensions, toolbars, or plugins. The hijacked browser may redirect users to malicious websites, change their homepage or search engine settings, or inject unwanted ads.
Example: A user inadvertently installs a browser extension that claims to enhance web browsing but is actually malicious. Once installed, the extension modifies the browser’s settings to redirect the user’s searches to a fake search engine that displays ads or collects browsing data for the attacker.
8. Session Hijacking
Session hijacking involves stealing a user’s session token or cookies to impersonate them and gain unauthorized access to their accounts. Attackers intercept or obtain these tokens through various means, such as network eavesdropping or exploiting vulnerabilities in web applications.
Example: An attacker on the same unsecured Wi-Fi network as the victim intercepts their unencrypted HTTP traffic. By capturing the victim’s session cookies, the attacker can then use these cookies to authenticate themselves as the victim and gain access to their accounts without needing their login credentials.
9. Tabnabbing
Tabnabbing is a type of phishing attack that targets users who have multiple browser tabs open. When a user switches to a different tab and then returns to an inactive tab, the content of the tab has been replaced with a malicious page designed to mimic a legitimate site, prompting the user to re-enter sensitive information.
Example: A user has multiple tabs open, including one logged into their online banking account. After switching to another tab and returning to the banking tab, they find that the page has been replaced with a fake login page that closely resembles the bank’s website. Believing they have been logged out, the user enters their credentials, which are then captured by the attacker.
10. Formjacking
Formjacking involves injecting malicious code into web forms on e-commerce websites to steal payment card details and other sensitive information entered by users. Attackers typically exploit vulnerabilities in the website’s code to intercept and exfiltrate the data entered by unsuspecting users.
Example: An attacker compromises the checkout page of an online store by injecting malicious JavaScript code. When a user enters their credit card information to complete a purchase, the code silently captures the data and sends it to the attacker’s server, allowing them to steal the user’s payment card details for fraudulent purposes.
Protect Browser-Based Attacks with Client-Side Protection
Implementing client-side protection is a powerful way to protect your end-users, regardless of their browser security practices.
One of the most effective methods is deploying a CSP (Content Security Policy) header. CSP header helps detect and prevent attacks by specifying which sources are allowed to load resources like scripts, styles, and images on your site. CSP allows you to specify trusted sources for scripts, styles, images, and other resources, ensuring that only content from these sources is loaded.
AppTrana’s Client-Side Protection provides continuous discovery, monitoring, and inventory of JavaScript, overseeing all executed code. By injecting a CSP into the response header, it helps ensure that only trusted JavaScript is executed while blocking all others.
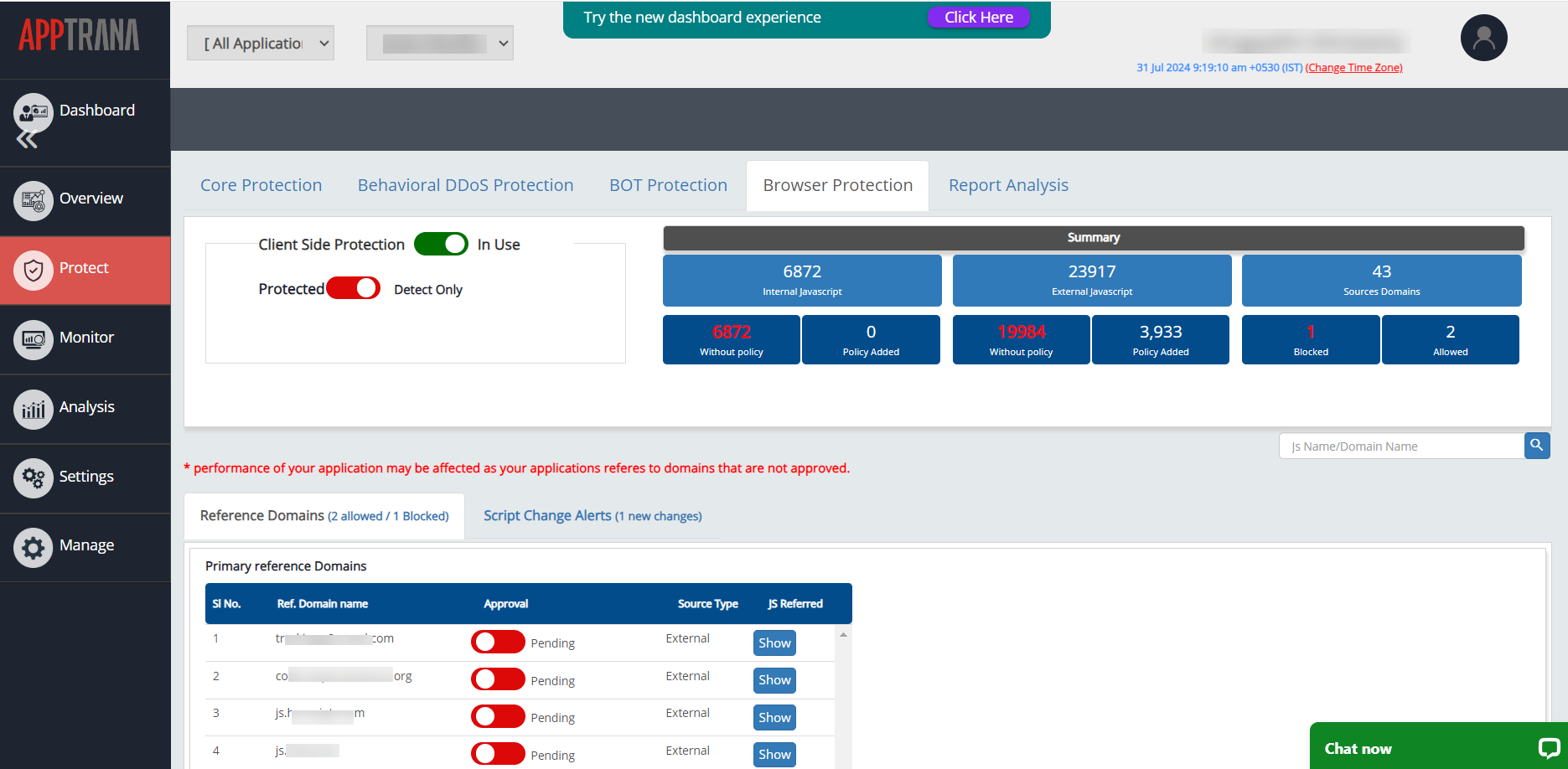
The CSP header enables the browser to report details about third-party services to Client-Side Protection, which are then displayed on the WAAP dashboard. This visibility facilitates a thorough review and assessment of each service’s security posture, enabling informed decisions on whether to allow or block them within your application.
AppTrana’s unique dual mode (Protected and Detect only) for managing CSP violations allows users to experiment with different directives safely, eliminating the risk of blocking legitimate scripts and affecting user experience.
Additionally, the client-side protection provides ongoing visibility into the third-party services used within your application, promptly reporting any changes or modifications. This allows you to stay vigilant and respond proactively to emerging threats.
Learn the fundamentals of Supply Chain Attacks in this upcoming webinar—an essential watch for anyone concerned about web browser security.
Other Recommendations to Prevent Web Browser-Based Attacks
Keep Software Updated
Browser Updates: Regularly update your web browser to the latest version, as updates often include security patches that fix known vulnerabilities.
Plugin/Extension Updates: Ensure that browser plugins/extensions, such as Adobe Flash, Java, and browser add-ons, are up-to-date. Consider uninstalling unnecessary or outdated plugins/extensions.
Enable automatic updates for your browser and plugins/extensions whenever possible. This ensures that you receive security patches as soon as they are available, reducing the window of vulnerability.
Use a Secure Browser
Choose browsers known for their security features, such as Google Chrome, Mozilla Firefox, Microsoft Edge, or Safari. These browsers often have built-in security mechanisms and frequent updates.
Consider using a security-focused browsers, such as Brave or Tor Browser, which prioritize user privacy and security.
Reduce Your Attack Surface with Browser Isolation
The primary strategy that has been gaining traction over the past few years. It reduces attack surfaces and protects against web browser attacks. Browser isolation separates browser activity from endpoints and networks.
It executes all web page codes in secure virtual containers. This minimizes the attacker’s ability to move laterally and infiltrate systems.
All malware is boxed in containers. A passive visual representation of the content will be provided when a user requests it. So, if the user clicks on a malicious attachment, the malware stays in the secure container. It does not reach the system.
The browser isolation is easy to deploy and scale. Yet, the biggest downside is that the user experience may not be reliable. It may be less than ideal.
Vulnerability Assessments
Risk detection stands as another pivotal element in browser security, employing an array of tools and methodologies to unearth potential threats and vulnerabilities. This encompasses activities like malware scanning, phishing detection, and recognition of suspicious activities.
Conduct regular vulnerability assessments and penetration testing of your applications to identify and prioritize security weaknesses.
Utilize automated scanning tools to detect common vulnerabilities such as XSS, SQL injection, CSRF, and insecure configuration settings.
Perform manual pen testing to uncover more complex vulnerabilities that automated tools may miss.
Input Validation and Output Encoding
Validate and sanitize all user inputs to prevent injection attacks such as XSS and SQL injection. Use parameterized queries and prepared statements to prevent SQL injection vulnerabilities.
Encode output data using proper encoding techniques (e.g., HTML entity encoding, JavaScript escaping) to mitigate XSS vulnerabilities.
Enable Click-to-Play for Plugins
Configure your browser to require permission before running plugins, such as Adobe Flash or Java. This reduces the risk of drive-by download attacks by preventing malicious content from automatically executing.
Exercise Caution When Clicking Links
Be cautious when clicking on links in emails, social media posts, or websites, especially if they seem suspicious or unsolicited. Hover over links to preview the URL before clicking to verify their legitimacy.
Avoid downloading files from untrusted sources or clicking on pop-up ads, as they may lead to drive-by downloads or other malware infections.
Use HTTPS Everywhere
Prefer websites that use HTTPS (Hypertext Transfer Protocol Secure) encryption for secure communication. HTTPS encrypts data transmitted between your browser and the website, protecting it from interception and tampering by attackers.
Educate Users
Raise awareness among users about common web browser-based attacks, such as phishing, XSS, and drive-by downloads. Provide training on how to identify suspicious websites, emails, and social engineering tactics.
Encourage users to report any suspicious activity or security incidents promptly.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 July 31, 2024
July 31, 2024



